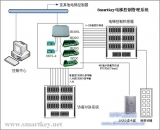
1. System overview The safety of the elevator system of the building is an important part of the safety of the entire building. In this system, all ...
The second generation ID card information automatic entry and data collection backup system solution
I. Introduction With the continuous popularization of the second-generation ID card, the second-generation ID verification machine has been ...
1. Development background: Trailing robbery is one of the most common problems in robbery crimes at cash counters. Solving this problem has become a top ...
The bank's treasury is a very important area, and some monitoring methods are needed to realize real-time monitoring of personnel. The use of RFID ...
I. Overview Electronic tag (Tag): It is composed of coupling components and chips. Each tag has a unique electronic code. The internally stored ...
1. Program description 1 Overview 2. Why use fingerprints? 3. Why useAttendance System? Improve management efficiency. Using advanced ...
There are currently several views on RFID anti-counterfeiting: one is a unique ID number to complete, and at the same time some algorithms are ...
1. Overview of fingerprints: 1) What is a fingerprint The uneven skin on the inner surface of our palms, fingers, feet, and toes will form a ...
Since 2004, the second-generation resident ID card has entered people’s lives and is widely used for account opening, investment, social security and ...
Introduction This system uses RFID technology to solve the problem of wine in the anti-counterfeiting and logistics traceability process. Our company ...
The application solution of Hanwang OCR certificate recognition system in the telecommunications industry product description In the past two ...
1. Face recognition technology Face recognition is based on the facial features of a person, and the input face image or video stream is first judged ...
- « Previous Page
- 1
- 2
- 3
- 4
- 5
- …
- 12
- Next Page »