1 background In recent years, with the development of my country's economy, the tourism service industry has developed rapidly, and the following ...
1. Background-current problems in the production of wineries In today's society, counterfeit goods have become a worldwide problem. Driven by interests, ...
I. Introduction With the development of the economy and the improvement of living standards, art collection is becoming a new consumption hotspot for ...
1 Introduction For a long time, in the field of product authentication, authentication technology has been a problem that industry professionals are ...
Project background RFID anti-counterfeiting traceability technology breaks through the ideas of anti-counterfeiting traceability technology in the past, ...
I. Introduction "A home with mahogany is like sitting in a money vault." Mahogany furniture is famous and excellent in quality, and has been a leader in ...
There are mainly two types of identity authentication technologies used in traditional systems: (1) Personal identification code and password. The two ...
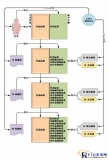
1 RFID system composition and principle 1.1 System composition One of the most basicRFIDThe system generally consists of an electronic tag (Tag) ...
A Shenzhen brand jeweler has adopted this system solution to achieve channel control of franchisees in various provinces and cities across the country, and ...
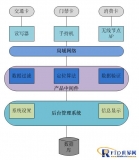
I. Overview With the social and economic development and prosperity, the flow of people in various industries continues to increase. The focus is on how ...
As China's top, most representative, and largest-selling liquor brand, Wuliangye has always been the primary target of counterfeiting crimes. Therefore, ...
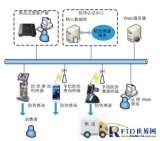
The mobile security anti-theft system for the cultural relics on display in the museum directly conducts active monitoring and management of the cultural ...
- « Previous Page
- 1
- …
- 7
- 8
- 9
- 10
- 11
- 12
- Next Page »