Wireless integrated security system solution for power distribution room
[ad_1]
Chapter 1 Proposal and characteristics of the wireless integrated security system for the power distribution room
As we all know, modern life is inseparable from electricity. The stable transmission of electricity is affected by various conditions and factors, such as weather, environment, man-made damage, equipment aging, etc. We cannot prevent weather changes, nor can we prevent equipment aging, but We can detect and monitor environmental changes and take early warning measures to prevent man-made sabotage. There are real needs from the following aspects:
1. Substation equipment in remote rural areas is often damaged, and transformers and transmission lines are often stolen; instant information alarm can reduce losses, and on-site alarm can also deter saboteurs.
2. Urban power distribution rooms and switch stations are located in every corner of the city, from large areas to small buildings, and there will be power distribution rooms or switch stations; the stable operation of the equipment is related to the normal work and life of people in the area. In the event of an emergency, the staff can be quickly notified to solve the problem.
3. The equipment room is cleaned regularly by a dedicated person to maintain a clean environment; equipment maintenance is also regularly inspected by staff; it is also very necessary to supervise the work of the staff.
4. There are smoke detection, exhaust fan, anti-theft alarm and other equipment in the computer room, and these auxiliary equipment need to be set for linkage operation in the same management platform;
5. The anti-theft alarm has multiple defense zone settings, which can be freely armed and disarmed, and the staff will not generate an alarm when they enter and exit; the alarm function can be expanded as needed;
6. The video camera equipment needs to be linked to capture the image of the person when the alarm is generated;
Kingkang power distribution room wireless integrated security system is especially proposed for urban and rural power distribution rooms, power distribution rooms and other power facilities. It has multiple functions such as access control management, real-time monitoring, security and anti-theft alarm, patrol inspection, and environmental monitoring. It can facilitate the entry and exit of internal staff, prevent unrelated personnel from entering and exiting at will, and can realize inspection and supervision work; at the same time, it can be connected to a variety of detection equipment to realize the linkage alarm function of defense zones and realize the monitoring of environmental changes. System application technical characteristics:
1. Radio Frequency Identification Card (Proximity Card): The core part of the radio frequency identification card is an IC chip produced by the most advanced microelectronics technology. The chip has a built-in unique ID code in the world. The role of the inductive identification card in the access control management system is similar to that of the key in the traditional mechanical lock, but due to the difficulty and uniqueness of its production, it is ensured that it cannot be copied, thus avoiding all the possibility of cheating in the “key” link.
2. Wireless integrated security control system (front-end controller): The front-end controller is the central centralized processor for all external devices (such as electric locks, alarms, sensors, door opening buttons, etc.) at each door point. The code of the proximity card (valid card) with permission to enter and exit the door is stored in the central controller database. When the front-end controller receives a valid card number, it automatically opens the electric lock, stores the door opening record and uploads it to the control center; the front-end controller detects When the electric lock is opened in an abnormal way, an alarm will be activated and the monitoring center will be notified. At the same time, the front-end controller can be connected to infrared radiation, smoke detection, human body induction and other sensors and alarms, fire extinguishing and other output devices. When it detects that the power distribution room is illegally invaded or the environment is abnormal, it can link the alarm and activate the corresponding external equipment. In this way, the system not only avoids the incomprehension when using mechanical locks, but also proactively defends, warns of all abnormal situations and reports them in time.
3. Wireless integrated security software management platform-KWSecurity management software: KWSecurity management software is the control center of the entire system. The effective card settings and permissions distribution mentioned above, and the parameter settings of the front-end controller are all completed through the management software. When changing the management personnel of the power distribution room or modifying the entry and exit permissions of the staff, it is only necessary to download the software to the corresponding front-end controller after the software modification. There is no need to worry about the original “key” that can open the door like a mechanical lock system. The management software can manage multiple front-end controllers. The card swiping records and alarm records of each front-end controller are stored in the management software database, and the personnel access and safety status of the power distribution room where each front-end controller is located can be checked at any time.
4. Wireless communication equipment: The wireless communication equipment is the communication bridge between the management software and the central controller. It combines the management software and numerous front-end controllers to form a network for the safe management of various power distribution rooms. With the help of a mature and highly-covered mobile communication network, wireless communication equipment uses GSM short message or GPRS wireless network to communicate between the management software and the central controller, which guarantees effective communication and low communication costs. It also facilitates the networking of the system. Where conditions permit, wired networks can also be used. However, in view of the scattered locations of power distribution rooms and the inconvenience of wired networking, this program mainly describes wireless networking systems. When it comes to wireless communication, people may have cognitive misunderstandings, thinking that wireless means that there is no need to connect between the controller and its peripheral devices such as card readers, electric locks, and detection probes. In fact, this is incorrect. As far as the power supply of the electric control lock is concerned, a wired power supply must be connected. In addition, all the above-mentioned devices are installed near the door, and the mutual connection is very simple. Most of the transmitted signals are switch signals, and no wireless is required. The wireless communication technology described in this solution refers to the networking mode of the front-end controller and the upper management computer. Usually, the network of the access control system adopts the wired RS-485/422 bus, and the newer products use the TCP/IP network for networking. These two methods obviously have limitations in the management of the power distribution room. The first is the communication wire. The investment is huge; the wireless integrated security system we now propose is to connect each front-end controller with the upper-level management computer in a wireless way to form a wireless transmission network, and this wireless way uses the ready-made GSM/GPRS communication network through SMS or wireless The network is used to transmit data, and where there is a mobile phone signal, it can communicate with the network.
Chapter 2 System Overview, Design Principles and Functional Features
1. System overview
Kingkang power distribution room special security system adopts the most advanced digital electronic technology, identification technology, wireless communication technology and network technology. It integrates intelligent identification, computer network management, and digital monitoring into one intelligent access control, pushing access control and anti-theft management to A new field. In this system scheme, we will use the front-end control machine to centrally manage and decentralize the entry and exit management, anti-theft management, inspection management, and environmental monitoring of each area (mainly the power distribution door here). We can use the proximity card as a configuration The vouchers for electrical room maintenance personnel and inspectors to enter and exit the power distribution room can be generated through the computer to generate a report on the entry and exit of the power distribution room channel security, and can be set through various defense zone alarms, and use wireless communication to transmit alarm information in real time and connect to the environment The detection equipment linkage equipment regulates the temperature and humidity of the power distribution room to ensure the stable operation of the power distribution room.
2. Design principles
Due to the need for safety and high-efficiency management, the design of the integrated security system of the power distribution room should follow the following principles:
Practicability of the system: The content of the integrated security system of the power distribution room should meet actual needs. It is convenient and simple to build or modify the system, and is convenient to use; the software is simple to operate and easy to use, and it is convenient to save and transplant data.
System stability: Since the integrated security system of the power distribution room is an uninterrupted long-term work system, the safe and stable operation of the power distribution room is closely related to people’s lives, so the stability of the system is particularly important. The system is required to have more than one year of successful application experience in the market, with a corresponding customer base and customer service system. In terms of communication, the wireless networking method adopted by the system is based on the GSM/GPRS mobile communication network, where there is a mobile phone signal to ensure stable communication.
System safety: All equipment and accessories in the integrated security system of the power distribution room should operate safely and reliably, while also complying with relevant Chinese or international safety standards, and can work effectively in non-ideal environments. The powerful real-time monitoring function and linkage function fully guarantee the safety of the use environment.
System scalability: The design and implementation of the integrated security system of the power distribution room takes into account the actual needs of future scalability. It can also flexibly increase, decrease or update each subsystem to meet the needs of different periods, maintain a leading position for a long time, and become a reality A model of application. When the system is designed, a reasonable configuration is made for the functions that need to be realized, and this configuration can be changed. Even after the project is completed, the configuration change is also possible and convenient. The system software will be upgraded and perfected according to the requirements of the developers in different historical periods, and the software will be upgraded free of charge for the corresponding application customers.
Easy maintenance of the system: The maintenance of the integrated security system of the power distribution room during operation should be as simple and easy as possible. The operation of the system is truly to the extent that it can work when the power is turned on, and it can be operated when it is plugged in. And there is no need to use too many dedicated maintenance tools during the maintenance process. From the configuration of the computer to the configuration of the system, the configuration of the front-end equipment has fully considered the reliability of the system and implemented the corresponding certification. While achieving the lowest system failure rate, we also consider that even for unexpected reasons When a problem occurs, ensure the convenient storage and rapid recovery of data, and ensure that the channel can be opened quickly in an emergency. The maintenance of the entire system is online, and the normal operation of all equipment will not be stopped due to the maintenance of some equipment.
All in all, the system can be more convenient, safer and more reliable for the management and monitoring of power distribution rooms.
Three, the main design basis specifications
1. International integrated wiring standard ISO/IEC11801
2. “Code for Electrical Design of Civil Buildings” JGJ/T 16-92
3. “The People’s Republic of China Security Industry Standard” GA/T74-94
4. “People’s Republic of China Public Safety Industry Standard” GA/T70-94
5. “Engineering Technical Code for Monitoring System” GB/50198-94
6.Standardization Management Measures for the Electric Power Industry
Chapter III Structure and Configuration of Special Integrated Security System for Power Distribution Room
1. The functions and features of the system
In addition to the channel control and management and anti-theft alarm functions, the integrated security system of the power distribution room also adds environmental monitoring and equipment linkage functions. It is the best choice for unattended power distribution rooms and computer rooms:
1. Access control function:
1) It can manage 30,000 effective users; store 100,000 event records offline;
2) Door opening methods: card, card or password, card plus password, automatic opening/closing at regular time, remote opening/closing, support for multiple identity authentication, up to 6 layers;
3) Support wiegand 26/34 and password keyboard, support biometric access (fingerprint, iris recognition device);
4) The door can be opened remotely through software and mobile phone text message;
5) The maintenance efficiency of the power distribution room can be improved, the management is more standardized and effective, the real-time monitoring of events, and the burden of maintenance and management personnel can be reduced.
6) A proximity card can replace all the keys of the power distribution room to prevent the confusion of key management; and a card can have different access rights, and the authorized card can enter the power distribution room within the scope of its duties. All incoming and outgoing situations are recorded in the computer, which is convenient for inquiring about the time of specific events and fulfilling responsibilities.
7) If the employee’s proximity card is lost, you can report the loss and delete the authorization immediately in the system, so that even if someone else finds the proximity card, they cannot enter the power distribution room for damage. This is much more convenient than ordinary mechanical locks. You don’t have to To be safe, change the lock again and re-key each person. For those who resigned, fired, or left, the proximity card can be recycled and reused, or the authorization can be deleted. Because the proximity card cannot be copied, there is no need to worry about re-entering the power distribution room after resignation.
8) In special circumstances, the software can be forced to operate, and the door can be forced to close through the function of the software, so that even authorized card holders cannot enter. After that, the system can be restored to normal through the software.
2. Anti-theft alarm function:
1) There are 8 basic defense zones and 8 can be expanded;
2) Support software defense zone timetable setting, cycle by day, support software defense zone linkage table setting
3) Different defense zone types can be defined according to the different detection terminals accessed by each input
4) Support a certain defense zone when a false alarm occurs due to a detection device failure, temporarily disconnect the defense zone, and interrupt the alarm, and restore the normal defense zone after the fault is repaired (or other situations where the defense zone setting needs to be temporarily interrupted)
5) Automatic arming, remote arming and disarming, swiping card arming and disarming, button arming
6) Support custom alarm content edited by software, and send self-check information to the management mobile phone regularly
7) Powerful self-monitoring ability, tamper-proof alarm, 220V power failure alarm, low-voltage alarm of backup battery
3. Inspection function:
1) The software can edit the inspection menu and send it to the front-end controller;
2) The inspector can choose to send the inspection status to the management center in real time through the man-machine interface;
3) Software electronic map display, which can monitor the inspection status in real time;
4) Effectively supervise and manage the work of staff, and check whether various inspection tasks are in place;
4. Environmental monitoring function:
1) Temperature and humidity detection, real-time display;
2) The upper and lower limits of temperature and humidity can be set. Once the limit value is reached, an alarm will be triggered or the linkage device will be activated to regulate the temperature and humidity;
5. Dedicated integrated management software
All Chinese operating system based on Windows, friendly interface, convenient and simple operation.
The system has good scalability, with wireless networking and wired networking functions;
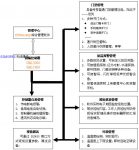
2. Functional management structure model
The integrated security system of the power distribution room is an intelligent management system that combines multiple functions such as access control, anti-theft, patrol inspection, and environmental monitoring:

Three, the basic components of the wireless integrated security system of the power distribution room
1. Front-end controller: The front-end controller is composed of a stable switching power supply, a control board, and a short message transceiver module; the control board can be connected to 2 card readers, 8 switching inputs, 8 relay outputs, and 4 AD input interfaces; The SMS transceiver module is responsible for communicating with the wireless integrated management software installed on the computer of the management center.
2. Wireless integrated management software: Centrally manage and monitor all units through the computer, and perform corresponding management tasks such as access control authorization, defense zone settings, environmental monitoring, inspection settings, and information statistics.
3. The management center computer short message transceiver module: responsible for the communication with each front controller, it is the short message sending and receiving terminal. In theory, each SMS transceiver module can communicate with N wireless access controller mobile phone numbers, but considering the actual application operation and system stability, it is recommended that each SMS transceiver module manage within 50 wireless access controllers; One management computer can receive multiple SMS transceiver modules.
4. Mobile phone SIM card: Each front-end controller needs to be equipped with a mobile phone SIM card, and the SMS transceiver module of the management center also needs a mobile phone SIM card.
5. Manage mobile phones and alarm mobile phones: The system can set 4 mobile phone numbers as management mobile phones, and 5 mobile phone numbers as the person in charge of handling alarms, except for all the management mobile phone card numbers of the management center SMS transceiver module for each front-end controller. The management mobile phone can send relevant instructions to directly operate the wireless access controller, and the alarm mobile phone can instantly receive the alarm information sent by the front-end controller, and take emergency measures immediately!
6.Access control peripheral equipment: proximity card, card reader, electric lock, door sensor, door open button
1) The proximity card has a variety of shapes and can be selected at will. The chip in the card is written with a 32-bit code that will never be repeated. When the card is close to the sensing area of the card reader, the controller can make a judgment based on the chip data on the card read by the card reader. The proximity card does not need to be touched during operation and will not wear out. The chip is encapsulated in the card and will not be corroded, so it is durable and can be used for more than 10 years.
2) The card reader is the control part that reads the proximity card. A built-in radio transmitting antenna can receive information such as the code sent by the card when the proximity card is approaching. After the card reader analyzes and confirms that it is a valid card, the code is transmitted to the control part.
3) The electric lock is used to replace the mechanical lock. After the controller sends the door open signal, the electric lock can be opened automatically.
4) The contact detector is used to detect the opening and closing status of the door to determine whether the door opening is valid or approved, and then the controller triggers an alarm signal.
5) Go out can be set to go out by pressing the button.
7. Anti-theft alarm peripheral equipment:
Detection equipment: infrared beam, glass break detection, smoke probe, water immersion probe, equipment displacement detector, etc.;
On-site alarm equipment: siren, flashing lights, etc.;
8. Temperature and humidity detection probe: The front-end controller comes with a temperature and humidity detection probe, which can detect the temperature and humidity of the indoor environment in real time.
9. Inspection and inspection: The inspection status of the equipment room can be reported immediately to provide a basis for work supervision.
10. Extensible function: Extensible video capture and voice prompts.
[ad_2]