Application of RFID in Archives
[ad_1]
People always hope that when they need a piece of information, they can quickly find it, but in the archives management hall and the archives management office of enterprises and institutions, you can often see that the managers are anxious and busy to find the required information. For a long time, this problem has made file management personnel strenuous. At present, domestic archives mainly use file numbers and bar code marks for internal shelving and positioning. In the logistics process of physical archives, file numbers and barcodes play an important role. Traditional file management methods have low efficiency such as redundant file quantity, difficulty in query, inventory, and long processing time. The application of information technology is the key to solving the problem. The introduction of RFID technology will completely change people’s understanding of archive management activities.
By analyzing the existing problems in current file management, Hangzhou Ziyue Technology Co., Ltd. designed a set of file management automation system based on RFID technology, and elaborated on the system’s functional module architecture and management business process, with a view to file automation , Make improvements in intelligent management.
1. The status quo and problems of file management
In recent years, my country’s archives industry has made great progress. The scale of archives industry has expanded and the number has increased day by day. The types of archives have become increasingly diversified, and the amount of information has expanded rapidly. However, the problems caused by traditional file management methods and technologies have become increasingly prominent:
1.1 The file cataloging process is cumbersome and inefficient, and the organization time is long
In the traditional way, the archives need to be classified, sorted, and bound after entering the library, and then the relevant information of the archive box is manually written, and finally the archive directory is manually copied, and the directory and the files are packaged in the archive box. This method of operation consumes a lot of labor and time, resulting in many files being stacked for a long time after entering the library, and a corner cannot be sorted and archived in time. In addition, file cataloging and file box transcription are mostly simple and repetitive labor, and manual processing makes the entire process cumbersome and inefficient.
1.2 The order of file storage is more likely to be disrupted
Although files are generally stored in categories, in the process of file access, due to the randomness of manual operations and some inevitable errors, the order of file storage will inevitably be disrupted, resulting in disorderly file storage and difficulty in searching.
1.3 File review takes a long time
With the increasing size and variety of files, when searching for a certain file, the administrator first finds the file shelf where the file of that type is stored, and then searches each grid of the file shelf according to the cataloging information of the file. Once the file is not stored in the specified location as required when accessing it, it is like looking for a needle in a haystack, and all files need to be screened.
1.4 The file inventory operation is unscientific
Due to the large number of files and the file materials are all enclosed in file boxes, generally only the number of file boxes is counted when counting files. However, the types and quantities of files stored in each file box are different, and this inventory method does not truly reflect the true information stored in the files. If you want to open each file box for inventory, it will be a very huge project.
1.5 The management of invalid files is lagging behind
The validity period is one of the important signs of the value of archives. Therefore, archives exceeding the validity period are of no value and need to be destroyed frequently to reduce the occupation of archive inventory resources. However, due to the difficulty of file inventory work under the traditional management mode, management personnel are very inaccurate in grasping the storage time information of files, so that invalid files cannot be discovered and processed in time. Therefore, many old archives that have expired are still stored on the shelf together with valid archives, forming a large number of redundant archives, which brings additional load and cost to archive management.
In view of this status quo, technical upgrading and transformation of archives management is imminent. In order to solve the above problems, the Archives Bureau adopts advanced RFID technology to solve the above problems, and at the same time increases the anti-theft function.
2. Advantages of RFID technology solutions
2.1 Introduction to RFID technology
RFID (Radio Frequency Identification), or radio frequency identification, is an automatic identification technology that emerged in the 1990s. A typical RFID system consists of three parts: a radio frequency electronic tag, a reader or reader, and an antenna. It integrates multiple technologies such as coding, carrier, identification and communication. The main principle is to use radio waves to read, write and identify a marked medium. Non-contact is its obvious feature. In practical applications, the reader writes data in a specific format into the RFID tag, and then attaches the tag to the surface of the object to be identified. The reader can also read and identify the electronic data stored in the electronic tag without contact, so as to realize the functions of long-distance, contactless collection and wireless transmission of object identification information.
2.2 The advantages of applying RFID technology to file management
1. Non-contact data collection. RFID technology has greatly enhanced the manager’s ability to collect, exchange, and track information about items stored in the warehouse. The manager does not need to open the file box, just pass the file box with the RFID tag in front of the reader, and the specific name, quantity, file summary and other information of the files in the box can be displayed on the computer screen, reducing the manager’s The operation link improves operation efficiency and helps managers implement dynamic management of inventory files.
2. Fast scanning, and a large amount of one-time data processing. The RFID reader can quickly read multiple related data information including cargo location information and file content summary information from multiple radio frequency tags at the same time. For example, some readers can read data of 200 tags per second, which is more than 100 times faster than traditional scanning methods.
3. The label information capacity is large, the service life is long, and it can be reused. Compared with traditional data storage media such as barcodes and magnetic cards, the amount of data that RFID tags can store is greatly increased, reaching a capacity of 1K or more; the content of the tag can be repeatedly erased and written without damaging the function of the tag, thus The label can be reused.
4. High security. The data access of the label is protected by a password, and the identification code is unique and cannot be forged. This high-security protection measure makes the data on the label not easy to be forged and tampered with.
5. Strong anti-pollution performance and durability. The carrier of traditional bar codes is paper, so it is easy to be contaminated, but RFID has strong resistance to water, oil, chemicals and other substances. In addition, because the barcode is attached to the plastic bag or the outer packaging carton, it is particularly vulnerable to breakage; RFID label stores the data in the chip, so it can be protected from contamination.
6. The volume is miniaturized and the shape is diversified. RFID is not limited by size and shape in reading, and does not need to match the fixed size and printing quality of the paper for reading accuracy. In addition, RFID tags can be miniaturized and developed in various forms to be applied to different files.
7. It can be reused. Nowadays, the bar code cannot be changed after it is printed. The RFID tag can repeatedly add, modify, and delete the data stored in the RFID tag to facilitate the update of information.
8. Penetrability and non-barrier reading. When covered, RFID can penetrate non-metallic or non-transparent materials such as paper, wood, and plastic, and can perform penetrating communication.The barcode scanner must be at a close distance and there is no object blocking the situation before it can read the barcode.
9. The tag has an anti-theft function, and cooperates with the door-shaped channel antenna, which can prevent the loss of files and realize the alarm of illegal removal
3. Project plan design
3.1 The overall framework of the project
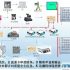
The idea of on-site management is to manage the gates of archives, including archive entry, inventory, inspection, anti-theft management, destruction management, etc. The number of gates of the archives bureau is generally based on the actual situation on the site. There are currently four archives bureaus. Take the door as an example. There is one door in the archives hall, and two file cabinets are placed in the two archive rooms. There are three small doors (the three small doors are exactly the same). The four channels are mainly to install fixed readers and antennas. At the same time, it is equipped with a handheld device. The fixed reader/writer is directly connected to the local area network through the wired network. The handheld device can transmit the collected data to the back-end computer via GPRS or WIFI, which can be managed in a unified manner in the back-end.
The specific functions are described as follows:
(1) Admission
Before the new archives are put into storage, the new archives must be cataloged according to the relevant information such as archives category, year and secret level, and written into the RFID tags through the terminal manager, and the generated electronic tag data is sent to the central database for system preparation. Called by other modules.
The process of file admission is shown in Figure 2:
When entering the library, the storage location management subsystem of the archive management information system issues an entry instruction, and then reads the file box information to be entered, and then the storage location automatic identification module matches the file box information with the archive automatic identification module. The storage location automatic identification module allocates the storage location of the archive box. After confirming that it is correct, the administrator sends an admission confirmation message, which is transmitted to the archive rack through the computer bus, the storage location indicator lights up, and the administrator puts the file box in To the storage position indicated by the indication point, press the confirmation button on the storage position, the indicator light will go out, and the confirmation signal will be fed back to the management system, and admission is over. After all the archives have been stored in the library, the archive information that has been in the library can be inquired in the query management subsystem, so as to realize the visualization and dynamic management of the archives.
(2) Inventory
Due to the use of RFID, file inventory has become a simple and fast task: the inventory command is issued by the query subsystem of the file management information system, and the RFID reader immediately completes the collection of relevant file information and corresponding storage information, and automatically Return the collected information and check the data in the central database. For the information that cannot be matched, the management personnel shall use a handheld reader to conduct on-site verification, modify the system information or on-site information, and complete the file inventory.
(3) Check
The review process of the archives is shown in Figure 3:
When querying related archives, the administrator first consults the catalog number of the archives through the query management subsystem. The system will extract the data information stored in the central database according to the catalog number, and issue an outbound instruction after verification. The automatic file identification module will map its storage location number according to the catalog number to find the physical location where the file is stored. The manager issues an outbound instruction, and the storage indicator lights up. When the file passes through the warehouse, the RFID reader at the warehouse will feed back the read file information to the management system, and the management staff will confirm that the checked file is consistent with the exported file before confirming the warehouse. At this time, the system will record the time information of the archive’s delivery time. If the feedback information is inconsistent with the query information, the monitoring module will send an abnormal alarm to the alarm module.
(4) Safety management
The security management subsystem can realize real-time monitoring and abnormal alarm functions on the archives site to prevent archives from being destroyed and stolen.
(5) Anti-theft management
All collection files are in the reading range of the reader. When the file is taken out, the RFID reader at the exit port captures the file information and checks it with the outgoing instruction information. If the file leaves the warehouse abnormally without the outgoing instruction issued by the archive management information system, the monitoring module will be activated The alarm module issues an alarm for abnormal conditions.
(6) Destroy
The value of archives has a time effect. The archives that have lost their archived value need to be destroyed to reduce the occupation of archive management resources. When the archives are in the library, the storage period is written into the RFID tag and stored in the central database. During the storage process, when a file reaches the storage period, the destruction management subsystem will automatically pop up the file failure prompt, and the administrator will destroy it or continue the storage process. At the same time, managers can also send wireless instructions through the archive destruction management subsystem, and the RFID tags on each archive box will feed back the storage period information, so as to realize the effective period management of the archives.
3.2 Channel design scheme
The design of the passage plan was designed after the site survey. First, the four passages are introduced. The passages are also divided into two types: the small door of the archives (three) and the door of the archives hall (one). ):
3.2.1 Gate design scheme
Generally, it is based on the needs of customers. If it is not for aesthetics, it can be installed on the beam above the door. If the marble is hollow, it can be installed inside; if it is solid, it can be installed underneath. The outside of the antenna can be made into a lampshade; if not Considering aesthetics, it can also be installed on both sides of the door.
3.2.2 Small door design scheme
The door of the file room can also be installed in more scenes according to the needs. If the customer is looking good, it can be installed in the ceiling or on both sides of the door.
Four, hardware product application program
3.1 Label selection and design
1. Setting of label information items
The information items stored on the file label include: file category, file name, file number, file secret level, storage time, preservation period, summary of file content, etc.
The information items stored on the storage location label include: storage location type, storage location number, stored file number interval and quantity.
2. Making the label
It is recommended to use Label for label production, which can print information on it and paste it in the position required by the customer.
3. Label installation
In the file label, the electronic label is sealed into a card or self-adhesive paper and affixed to each file box or file. The file box is made of plastic or paper material, which facilitates the pasting and removal of RFID tags. At the same time, the box body is not easy to damage and can be recycled to reduce storage costs. Considering the needs of moisture-proof and moisture-proof, a small amount of desiccant can be placed in the box.
4. Introduction to E44:
The performance of E44 is introduced in the following table:
Specification description E44
Product model Impinj E44
Physical characteristics size 105mm×6mm
Material PET
Ambient operating temperature -40°C to 65°C (-40°F to 149°F)
Storage temperature -40°C to 80°C (-40°F to 176°F)
Protection level
Enclosure IP-00
Protocol EPC Class1 Gen2
Capacity EPC: upto 96bits TID: 96bits
Frequency band 920-928
Application of high dielectric constant materials, such as near aluminum foil, near metal, near liquid applications,
For plastic surfaces
Used for glass car windows, etc.
3.2 Reader installation
In the archives project, readers are installed on the ceiling of the archives room. The normal operation of the equipment requires an external 220VAC power adapter and a local area network or wireless local area network coverage for data transmission. Connect the TCP/IP port of the RFID tag reader to the computer network port, so that the data read by the RFID tag reader can be transmitted back to the server through the network or wireless network.
Reader introduction:
RFID interface protocol: EPCglobal UHF Class 1 Gen 2 / ISO 18000-6C
Certification: Consistency and interactivity in a high-density reader mode environment
Architecture: Processor Intel IXP420 (266 MHz), Linux system 64 MB SDRAM / 64 MB Flash, sensitivity: -80db
Remote management protocol: EPCglobal Reader Management 1.0.1, SNMP v2 with MIB II;
Network services: DHCP, LL A, NTP, HTTP, Telnet, SSH, SNMP, mDNS, DNS-SD
Dense reader protocol: Dense reader mode, listening before sending, automatic triggering and event management
Reader communication protocol: EPCglobal Low Level Reader Protocol (LL RP) 1.0.1 Impinj Mach1
RF power: +30dBm/+32db with extension cable
Power: AC/DC power converter, maximum power 45 watts (120 or 240 VAC)
Communication interface: RS-232 (DB-9F), LAN TCP/IP (RJ-45), 4 GPIO inputs and 8 outputs
Antenna: 4 ports, reverse TNC
Dimensions: 22.7 x 32.4 x 5.7 cm (8.95 in x 12.75 in x 2.25 in)
Weight: 2.7 kg (6 lbs) Working temperature: -20℃ to +55℃ Dust and humidity adaptation: IP54
LED indicator: power, connection, work, antenna 0-3, CPU, read, monitor, failure
Software support: Java and .NET APIs for Impinj reader/writer protocol (Impinj gateway demo program)
Passed certification: FCC Part 15
3.3 Handheld reader
It is used for file inventory, clean-up along the shelf. For the information that cannot be matched, the management personnel shall carry out on-site verification with a handheld reader, modify the system information or on-site information, so as to complete the file inventory.
RFID handheld reader based on Windows CE 5.0, this product has the advantages of low power consumption, multiple data interfaces, simple human-computer interaction interface, etc., and can be widely used in various RFID systems. Typical applications include:
Logistics and warehousing management: logistics industries such as item flow and warehousing management, as well as post office flow management systems for mail, parcels, and luggage transportation;
Supply chain application areas: the application of goods supply process;
Product anti-counterfeiting detection: use the write protection function of the memory in the label to identify the authenticity of the product;
Other fields: in club management, library, student registration, consumption management, attendance management, and other systems have been widely used.
Features:
It is an ultra-perfect combination of integrated PDA and RFID data collection, using a streamlined Windows CE embedded operating system, which can realize RFID data collection and storage functions;
Comprehensive functions, with Bluetooth, WIFI, GPS, GPRS (3G), one-dimensional and two-dimensional bar code functions; (optional, users can choose whether to add these modules according to specific needs);
3.4 Antenna installation
In order to ensure the reading of file tag data, the specific conditions of the channel are required. The customer must pay attention to the beauty and the best effect at the site. Therefore, consider installing the antenna in the ceiling for the small door of the file room, and adjust the antenna azimuth on the spot. The laird antenna is used in the field.
Circular polarization 8dbm Sexual polarization 8dbm
The antennas using Laird technology are circularly polarized and linearly polarized antennas, which provide signal reception and transmission technology in the 902-928M frequency band. Laird Technology’s industry-renowned design method achieves the highest efficiency and performance in the entire frequency band.
Both the standing wave ratio and the axial ratio are excellent, allowing users to obtain maximum performance for this type of antenna. The antenna is mounted in a heavy-duty radome shell and can also be mounted directly on the wall, allowing any wall or mast installation.
The antenna is to provide an integrated coaxial pigtail and multiple types of connectors to choose from.
characteristic:
Ultra-thin
Very low VSWR and shaft ratio
Weather protection cover
Wide selection of connectors and cables
Polarized antenna and linear antenna
Application occasions
storehouse;
Airport hospital
Traffic terminal
Conveyor belt
Logistics management;
Personnel management.
[ad_2]