RFID book file management system solution
[ad_1]
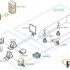
In an era where cost and efficiency are increasingly pursued, people are constantly looking for better technologies and methods for library and archive management. The library and archives management system developed by Shanghai Kongcheng IOT using RFID technology can greatly improve management methods, increase work efficiency, liberate library and archive staff, and allow them to engage in more valuable work.
The Shanghai Kongcheng IOT RFID book file management system installs an electronic tag for each book file. Through the tiny chip and antenna of the electronic tag, it is convenient to track and record every place the book file passes through in the flow process. The book files will be recorded when they pass through different offices or checkpoints, and they can be clearly seen on any internal network computer. The user can easily know the current location and storage location of the book file, and confirm the removal of the book file Or deposit status. This tracking system is very convenient to use, and it is easy to integrate with the existing library and file management system.
system structure
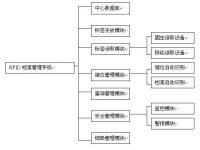
Shanghai Kongcheng IOT RFID book file management system mainly includes five parts:
1. Data center: It is composed of a central data server and a management terminal, which centrally stores and processes the management information of books and archives.
2. Housekeeping management system: It is composed of a management terminal and a label issuance and printing terminal, which can complete the unified production of RFID tags for book file information and new book files.
3. Circulation management system: help the administrator to write relevant information in the label when the book file is loaned out, check the book file and verify the information in the RFID label when returning it.
4. Query system: easily query the location of each book file through the management terminal and handheld.
5. System management: set system functions and permissions, account management, etc.

System functions
Book file management and storage: When new book files are stored in the library, the new book files are cataloged according to the category, year and author of the book file and other relevant information, and RFID label printing data is generated. Then, according to the printing data, write and print the RFID label, and paste the printed RFID label on the book file for readers to refer to. At the same time, the successfully printed data will be sent to the database of the data center for other modules in the system. Inquire.

Smart warehouse
Circulation management: Circulation management is divided into borrowing management module, return management module and anti-theft and loss prevention module.
When borrowing, the system will first verify the identity of the borrower, and enter the borrowing management system after passing the verification. The borrower consults the catalog number of the book file through the query management system. The system finds the location of the book file according to the entered catalog number, and prints out the loan list at the same time. The administrator uses the RFID reader to read the information written in the RFID of the borrower’s library file, and the information automatically enters the system management interface. After the administrator writes the fixed information of the borrowed book file in the RFID tag, including the borrower’s name, unit, lending time, borrowing period and other information, the book file is sent to the borrower to complete the borrowing management.
When the book file is returned, the administrator uses the RFID reader to read the book file, check the borrower’s information, whether the borrowing time is overdue, and confirm whether the data of the borrowed book file is the same as the information in the RFID tag. If there is a problem in this process, the system will enter the corresponding processing module for processing, and if there is no problem, it will send it back to the corresponding location based on the location information of the book file in the RFID.
The anti-theft and loss-prevention module cooperates with the export security inspection device of the library and archives to track the book files. The security inspection device will alarm when the library files that have not been checked out or are forbidden to be borrowed are out of the house, reminding the management personnel to stop them in time.
Data center management: including data management, collection and statistics, equipment and system management.
Data management mainly refers to the storage, modification and update management of basic information such as the catalog number, personnel information, and year of the book file, as well as the certification of the administrator of the book file. Data collection refers to the collection of information about borrowing and returning books and archives. Data statistics refers to the statistical analysis of data by time (day, week, month, year), book file information (department, personnel, etc.).
Equipment management refers to the information authorization and configuration management and maintenance of handsets, readers and other equipment.
The management of the system refers to the authorization and maintenance of the system operator, and the authorization and control of the operator.
Book file query: search the catalog number of the book file according to the style of Shanghai Homo sapiens; search the location of the book file according to different rules, check the introduction of the book file, etc. As shown below:
System Features
1. Completely non-contact system, the most economical solution: embedding non-contact chips into low-cost media can meet the needs of the solution to the greatest extent. The application of this advanced technology can greatly reduce equipment investment and maintenance costs And the cost of hardware wear and tear.
2. Fast scanning and barrier-free reading: When RFID tags are scanned, there is no need to align the reader with a straight line, and the reading and writing speed is fast. At the same time, RFID uses radio waves to transmit information, and there is no transmission barrier problem.
3. High security and flexibility: The inside of the RFID tag can be divided into separate application areas to store different application data. Each electronic label has a 32-bit globally unique serial number, which is written during the production process and cannot be changed.
4. Simple to implement and easy to use: system installation and debugging are very simple, and later use and operation and maintenance are also very convenient. Finding and identifying books and files is fast, and it is anti-theft and anti-loss, and can provide reliable performance and high security.

Advantages of RFID application in file management
(1) Non-contact data collection. RFID technology has greatly enhanced the manager’s ability to collect, exchange, and track information about items stored in the warehouse. The manager does not need to open the file box, just pass the file box with the RFID tag in front of the reader, and the specific name, quantity, file summary and other information of the files in the box can be displayed on the computer screen, reducing the manager’s The operation link improves operation efficiency and helps managers implement dynamic management of inventory files.
(2) Fast scanning, and a large amount of one-time data processing. The RFID reader can quickly read multiple related data information including cargo location information and file content summary information from multiple radio frequency tags at the same time. For example, some readers can read data of 200 tags per second, which is more than 100 times faster than traditional scanning methods.
(3) The reading distance is long, and the reading distance can reach tens of meters using UHF readers or handhelds. You can use the handheld to quickly inventory and organize files.
(4) The label information capacity is large, the service life is long, and it can be reused. Compared with traditional data storage media such as bar codes and magnetic cards, the amount of data that RFID tags can store is greatly increased, reaching a capacity of 1K or more; the content of the tag can be repeatedly erased and written without damaging the function of the tag. The label can be reused.
(5) High security. The data access of the label is protected by a password, and the identification code is unique and cannot be forged. This high-security protection measure makes the data on the label not easy to be forged and tampered with.
(6) The anti-pollution performance and durability are strong. The traditional barcode carrier is paper, so it is easy to be contaminated. However, RFID has strong resistance to water, oil, chemicals and other substances. In addition, because the barcode is attached to the plastic bag or the outer packaging carton, it is particularly vulnerable to breakage; RFID label stores the data in the chip, so it can be protected from contamination.
(7) The volume is miniaturized and the shape is diversified. RFID is not limited by size and shape in reading, and does not need to match the fixed size and printing quality of the paper for reading accuracy. In addition, RFID tags can be miniaturized and developed in various forms to be applied to different files.
(8) It can be reused. Nowadays, the bar code cannot be changed after it is printed. The RFID tag can repeatedly add, modify, and delete the data stored in the RFID tag to facilitate the update of information.
(9) Penetrability and non-barrier reading. When covered, RFID can penetrate non-metal or non-transparent materials such as paper, wood, and plastic, and can perform penetrating communication. The barcode scanner must be at a close distance and there is no object blocking the situation before it can read the barcode.
(10) The tag has the EAS anti-theft function, and with the door-shaped channel antenna, it can prevent the loss of files and realize the alarm function of illegal removal.
[ad_2]