RFID file management system solution
[ad_1]
I. Overview
With the continuous development of social science and technology, “spying” incidents of state agencies and units have occurred from time to time. In order to strengthen the management of confidential files, prevent the leakage of confidential files, and maintain the integrity and security of national information. Beijing Tigerred Technology Co., Ltd. has developed an RFID secret-related file location monitoring system. The system uses advanced RFID automatic identification technology and computer technology. Equipment such as batch borrowing and returning terminals, mobile point-and-hidden terminals, omnidirectional anti-theft channels, and the back-end database management system are coordinated to realize the whole process tracking and management of archives. The system implements strict specifications and requirements for the uniform coding, admission registration, borrowing, return, search, inventory, and real-time monitoring of archives, which improves the speed of file review, lending, and return, and improves the accuracy of the shelf. It enhances the information management level of archives management.
RFID technology can be used in several aspects in archive management:
(1) Statistics of physical files: Enter the whole case number, catalog number, title of the file, number of files in the file and storage location in the tag through the RFID read-write device. Labels are installed in the archives, and at the same time, the information is transmitted to the server through the network, and a database is formed after processing by a special management software. After this work is completed, the staff can use the intelligent archive rack automatic collection inventory system when statistical archive collections, and it is no longer necessary to check each case file.
(2) Management of physical archives: through the installation of intelligent security detection doors at the entrance of the archives warehouse, label information is collected in real time. If the physical archives are not authorized to leave the warehouse, the system will immediately alarm in conjunction with the security system to ensure the safety of the archives. . If it is an authorized file out of the library, the software will automatically record the out of library information and make statistics.
(3) Correspondence with the digital archive project: On the one hand, the digital information of the archive can be written in the label, so that during the adjustment and return of the archive digital process, only the label can be scanned. Missing scan. On the other hand, the label information can be connected to the archive management software through the interface program. When using the archives, the archives that need to be adjusted are retrieved through the archive management software, and the system will directly send the information of these archives to the terminal, and the warehouse staff will use the terminal. You can directly find the files in the archives warehouse to realize quick and accurate file adjustment. If cooperated with the smart file rack, this information can realize that the file rack automatically opens the rack where the file is located. The file adjustment personnel can find the required file in the rack according to the indicator light of the smart file rack, and the whole process can be completed in 10 seconds. Secondly, the access control system that reads the label information can ensure that the files will not be taken out of the file lending room during the borrowing process to ensure the safe use of the files.
2. System characteristics
1. File boxes and portfolios can be managed
There are two management modes of file box and file bag. The number of files in each box (bag) is calculated, and any missing files will be displayed in the system.
2. Authorized opening of filing cabinets
The file cabinet is equipped with an access controller, which can judge the authority offline/online, and supports the alarm of opening the door overtime, the alarm of abnormal door opening, and the video linkage of the door opening of the file cabinet.
3. Real-time archive location monitoring
To achieve file box-level positioning/monitoring, each file box has a fixed level and position accurately, and any file box placement error will be prompted.
4. File anti-theft
The unique identification of the archives, the carrier of data collection in each link of archives management, can store the basic information of archives and the status of requisition and return, etc., used for security control of archives in and out, to achieve the purpose of anti-theft and monitoring.
5. Files are quickly put on the shelves and organized, and searched quickly
The system provides a wealth of shelves, inventory and search functions, further saving time and manpower for organizing files.
6. With a librarian workstation, self-service borrowing and returning can be realized
Combining the debit card and work card of readers and managers, various operations of file management can be realized, including: information entry, batch borrowing and return, etc.
7. Intelligent real-time inventory file management
The RFID intelligent real-time inventory file management system is the latest product developed based on RFID (radio frequency) technology according to user needs. It is also the most advanced file management system in China. Compared with the barcode inventory file management system, it has inventory files. The advantages of standardized management, real-time monitoring of cabinet status, and high accuracy of real-time inventory. The hardware system is based on a highly reliable PLC, and the man-machine interface uses a 10.2 color LCD touch screen. And use the local area network to network the whole system. It has the characteristics of rich display content and simple operation. The accuracy rate of inventory in the cabinet file reaches 100%. Can control the automatic layer selection file cabinet under the operating environment.
RFID intelligent real-time inventory file management system, its file cabinet is made of high-quality cold-rolled steel plate produced by Baosteel, and is precisely manufactured by CNC sheet metal processing equipment. The chain sprocket of the transmission mechanism is selected from the high-quality chain sprocket produced by national famous brand products. It has the advantages of low transmission noise and low elongation; in order to ensure the correct position of the file box in the box, we also set up an anti-upside book stand in the box, and set up a custom adjustment area; to ensure that the user is in The required files can be accurately obtained in the shortest time, and a laser indicating recognition device is installed; the system adopts a light curtain safety protection device to effectively ensure the safety of persons and equipment; and an emergency brake button is provided to emergency brake equipment. The equipment is equipped with two emergency access schemes: in the case of system failure, the emergency manual button is used to complete the file access; in the case of a power failure, the emergency hand crank completes the file access after the main power supply is cut off.
The man-machine interface of the RFID intelligent real-time inventory file management system adopts a 10.2-inch color LCD touch display, and a set of fixed high-frequency RFID readers in the cabinet scans the file radio frequency tags in real time to complete the file input, output and file inventory. , The data update only takes 2-3 seconds.
Implementation process
Initialization: Load the files with the RFID electronic tags pasted into the filing cabinet. Each time a layer is completed, the file data location information of this layer is automatically entered into the database. It takes 2-3 seconds. According to the above process, complete the file loading of all layers of the cabinet , The cabinet file data location information is automatically entered into the database, and the initialization is completed.
Borrowing and returning: The host computer issues a borrowing or returning instruction, the file cabinet runs to the access window, the corresponding laser indicator lights up, the user takes out or saves the file, and the data is updated immediately.
In the library file access control management system: unauthorized files out of the library door alarm, automatic camera data collection.
Main functions can be realized
1), the host computer automatically counts the files in the cabinet in real time
2), the local machine automatically counts the files in the cabinet in real time
3), multiple upper computer network management files
4), database radio frequency tag management files
5), file management report printing
6), running status display
7), running log records
8), light curtain safety protection
9), manual/automatic layer walking
10), emergency hand crank function
11), slow stop and slow start function
12), automatic door
13), the file is located to this
14), access control management of archives in the library
Three, system structure
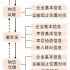
The intelligent file management system adopts advanced RFID automatic identification technology and computer software technology. It uses RFID electronic tags as information storage media and sticks them on the file bag. The basic information of the file and the return record of the file are stored in the RFID chip, using non-contact Smart librarian workstations, smart bookshelves and other RFID reading and writing equipment, in conjunction with the back-end database management system, can realize the information management of the work process of borrowing, returning, searching, and inventory of files. At the same time, the system installs an intelligent security door at the entrance and exit of the archives room. Through remote RFID authentication, it can realize the functions of automatic anti-theft and file entry and exit confirmation.
3.1 RFID data management system
The system consists of a central database and a terminal manager, which is the data access center and information input and output terminals of the system. The terminal manager includes a librarian workstation integrated with RFID reading and writing equipment, smart archive racks, card issuers and other equipment. It is an important port for the central database to obtain and output information. The role of the librarian workstation is to write the information in the database into the label or import the information in the label into the database; the intelligent archive rack is the hardware for the administrator to collect and communicate on-site information, and the administrator imports the collected data to the center The database, in turn, provides data support for the use of various functions of the archive management information system. The function of the card issuer is to complete the function of issuing and setting up librarian authorization cards.
3.2 Archives Management Information System
The system consists of a storage location management subsystem, a query management subsystem, a destruction management subsystem, and a safety management subsystem. The storage location management subsystem is composed of the storage location automatic identification module and the archives automatic identification module, and the safety management subsystem includes a monitoring module and an alarm module. The specific functions of the system are as follows:
(1) Storage location management subsystem: The hardware of this subsystem is mainly realized by the intelligent file storage rack. This subsystem can realize the automatic matching of the file bag number stored by the file automatic identification module and the storage location number stored by the storage location automatic identification module , So as to better realize the positioning of the archive storage position when the archives are in and out of the library. In addition, the storage location automatic identification module also has the functions of storage location allocation and storage location information management, which can realize the visualization and dynamic management of archives storage locations.
(2) Inquiry management subsystem: When files need to be consulted, this subsystem provides file cataloging inquiries, secret level inquiries, etc., and issues outbound instructions. The instructions transmit the inquiry signal to the file rack through the computer bus, so that the file rack is placed on the file rack. The indicator light is on, and the management personnel perform library operations according to the indicator light.
(3) Destruction management subsystem: Before the archives are put into storage, the storage period of each file is set in the destruction management subsystem. When the storage period is reached, the destruction management subsystem automatically reminds the management personnel of the relevant information of the invalid file. Personnel for further processing. Managers can also view the archive information that is about to expire or has expired from the subsystem.
(4) Security management subsystem: This subsystem is responsible for file anti-theft and on-site supervision, and implements the security mechanism of file management. When the file bag leaves the storage location under abnormal conditions (referring to the case where the outbound instruction is not issued by the query subsystem), the reader/writer installed on the file storage rack will capture this information and wirelessly transmit the file information back In the management system, the monitoring module will immediately send this abnormal information to the alarm module, and the alarm module will send an alarm to the computer control center after receiving the information. In addition, when there are files illegally taken away from the archives room, the alarm information can also be prompted through the intelligent security detection door.
(5) Warehouse temperature and humidity management system: The warehouse temperature and humidity management system is also controlled by temperature and humidity sensors. When the warehouse temperature and humidity are close to the set temperature and humidity, the system will automatically alarm to remind the management staff to dehumidify, dehumidify, and cool down. Work. Standard configuration of temperature and humidity management system, unified interface design, including temperature and humidity sensor module, infrared sensor module, sound sensor module, Hall sensor module, infrared reflection sensor module, photosensitive sensor module, smoke sensor module, Sensor DIY kit.The temperature and humidity sensor adopts DHT11 chip; digital output, no debugging, no peripheral circuit, low power consumption, high reliability; 14-bit precision; I2C interface
(1) Temperature: (0°C)~ (50 °C); ±0.5°C @25°C
(2) Humidity: 0 to 90% RH; ±3.5%RH;
(3) Power consumption: 30uW
The temperature sensor module supports the thermistorphotoresistor sensing experiment; supports the dynamic real-time display of the NTC temperature characteristic curve, and provides a screenshot of the dynamic real-time display of the curve; supports the temperature control potentiometer adjustment function.
To sum up, the RFID data management system and the archive management information system realize the connection between the systems through the system interface. The RFID data management system realizes the collection, storage, and reading and writing of electronic tags of archive data; the archive management information system realizes the access to archive information Application and management. At the same time, different permissions can be set for system users to realize the security management of users.
4. Implementation benefits
● Intelligent file management, avoiding manual operation errors;
● Detailed data model diagram of file rack distribution address, making file search easy and convenient;
● File location management, effectively avoiding file loss and reducing loss;
● Facts-in-place management, effectively avoiding file misplacement;
● Simple operation and scientific management, effectively improving management efficiency.
[ad_2]