Bank access personnel management system
[ad_1]
Foreword
At the 11th National Conference, the Internet of Things was included in the government work report for the first time. The development of the Internet of Things has become an important national strategic measure. Before 2020, the state plans to invest 3.86 trillion yuan in the research and development of the Internet of Things. Networking will profoundly affect and change our future production and lifestyles, and it will also bring unprecedented development opportunities to all walks of life, including the banking industry. Just like the Internet, which was the engine of economic development in the last round, the development of the Internet of Things in the future will also have a significant impact on the bank’s business operation model, organizational structure, and management model. The United States has proposed plans to establish “smart actions” in six major areas for the Internet of Things, one of which is the establishment of a “smart bank.”
System Overview
In order to strengthen the bank’s safety and regulation work, prevent staff from entering areas beyond their own authority, poor VIP member experience, etc., strengthen the supervision and management of bank staff, effectively improve the experience of VIP members, and prevent staff from entering the danger area. Combining the actual situation of the bank, we have developed the “Bank Entry and Exit Personnel Management System”, which realizes timely, accurate and multi-functional supervision effects. The system has the advantages of simple operation, convenient use, reasonable configuration, strong pertinence, stable operation, etc. , Achieved various design functions.
This series of products integrates high-tech long-distance radio frequency identification technology, short-distance radio frequency technology and multi-user anti-collision technology monitoring technology. Tags, locators, readers, and communication gateways use new embedded microprocessors and embedded software Designed, the system has strong signal penetration, no electromagnetic pollution to the human body, and strong environmental adaptability. It can locate multiple tags at the same time and realize wireless alarm. At present, this brand-new information recognition, access, transmission, and management technology has been rapid Widely recognized by domestic and foreign counterparts.
This series of products has independent intellectual property rights and has applied for a number of invention patents. It can fully meet the automated management requirements for personnel entering and exiting in banks and other places.
Scope of application
Banks, companies.
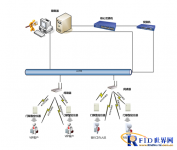
System Architecture Diagram System Architecture

System Value and Superiority System Value and Superiority
Bank entry and exit personnel management is a system developed by SMIC to meet the needs of banking and other industry users for information security and technology alarms. It mainly realizes active customer service, alarm video linkage, wristband label removal alarm, dangerous area alarm and other functions. .
At the same time, the system also has the following advantages:
Information security is in place
Taking into account the sensitiveness of banking sites and the importance of information security, the entire system adopts dedicated radio frequency protocols and dedicated encryption algorithms, avoiding wireless solutions using general protocols such as WIFI, thus greatly reducing access to the interior of the supervisory site through radio frequency communication networks. Possibility of data network.
Safe for the human body
The radio frequency RFID reader itself only accepts signals and does not send out any signals, and the influence of radio frequency signals generated by radio frequency tags on the human body is in full compliance with the national electromagnetic radiation protection regulations (GB9175-88 GB8702-88).
High reliability
Stability and reliability are the biggest challenges. Frequent false negatives and false positives are absolutely not allowed.
RFIDRedundant design of reader deployment
In order to improve reliability, redundancy should be considered as much as possible when deploying RFID readers to ensure that the signal from any radio frequency tag can be received by multiple radio frequency RFID readers at the same time. So as to ensure that in the event of individual radio frequency RFID reader failure, it can still ensure that all signals sent by the radio frequency tag, such as heartbeat, positioning, alarm, and low battery signals, can be reliably transmitted.
Do not miss the positioning of a large number of people
The main communication frequency adopts the 433M communication frequency, which has strong diffraction and penetration capabilities, ensuring that the radio frequency tag can be reliably read regardless of whether it is placed in any position or direction of the person, or blocked by the staff unintentionally.
At the same time, we have solved the problems of long distance, large flow, and ultra-low power consumption, and fundamentally improved the performance of the product. This ensures that the system can effectively reduce the collision rate of radio frequency positioning signals in the air in the case of high-density positioning of radio frequency tags, and greatly reduces the probability of radio frequency signal reception loss.
Highly integrated
In the future, more applications such as asset management, vehicle management, and tool management can be deployed directly and quickly on existing platforms. Reserve interfaces with security, office, application business and other systems to quickly integrate and form a synergy.
Easy maintenance
The system provides automatic maintenance functions for electronic tags and positioning equipment, and provides fault detection functions for radio frequency RFID readers, which greatly reduces the maintenance cost of the system.
System Components System Components
Card label
The card label is a new type of label specially designed for the RFID bank personnel entry and exit management system, which is used in the management of VIP customers and bank staff information.
Reader
433M band dual antenna reader, can identify 100 tags at the same time, provide SDK interface.
Access control locator
It can be used for dynamic management of key areas and can trigger alarms when approaching key areas.
Communication gateway
Provide power to the reader, process the data uploaded by the reader, and manage the reader in a unified manner.
System Function
Identification
The bank manager sends an RFID active card tag to each employee and VIP customer. The electronic tag has a unique ID number and cannot be changed. This solves the problem of unique identification of VIP customers and employees.
Active alarm in dangerous areas
Install access control locators in document rooms and cash rooms, and install ground-sensing locators on the perimeter walls. Set this area as a dangerous area. As long as employees without authorization approach the area, the system will immediately send an alarm. The alarm mode can be sound and light alarm, voice prompt, etc.
Personnel tracking
Person search
The’personnel search’ function can help managers quickly find the person they want to find. As long as you enter the information you want to find the person in the system, the system will immediately pop up the area where the person is located, the area will have a flashing effect, the operation is simple, and the effect is obvious.
Historical trajectory tracking
The historical trajectory tracking function is mainly to record the historical trajectory of the staff in a certain period of time. It can accurately tell the manager “when, who, and where”.
Authorization recognition
Bank employees and customers have corresponding authority levels. For example, ordinary employees cannot enter the cash room, document room, etc. without permission. However, due to the large number of bank personnel, the manager may not be able to identify each person’s authority in time, resulting in important documents Or the loss of cash.
Binding electronic tags with personnel permissions, and by deploying sensing devices in various locations throughout the bank, the system proactively identifies personnel permissions in time. When a person who does not have permission to enter a certain area enters the area, the alarm data will be uploaded to the back-end server. Managers can take actions in time through the back-end server.
Video linkage
The system is compatible with mainstream video interfaces such as Haikang and Dahua. When an alarm occurs, the on-site video surveillance images can be immediately accessed to help police officers analyze the scene of the incident, and make correct disposal decisions after further analysis of the pre-alarm.
[ad_2]