Detainee Positioning System
[ad_1]
I. Introduction
The original intention of setting up prisons in our country is the same as that of other countries. The main purpose is to reform criminals, so that they can become a self-reliant and self-reliant member of society through reforming criminals.
However, the current situation of prison personnel management in my country is mostly still in the stage of patrolling by prison guards and adding cameras to monitor and alarm. Manual operations still account for a large proportion, and the degree of informationization is relatively low, and information collection is still only relying on manual input. Really associate the information system with the detainees; it is impossible to grasp the location information of each prisoner who should be reformed in time; it is impossible to know in time whether anyone has left the area that should not be left; it is impossible to know in time whether anyone has entered the area that should not be entered Area; Is there any violation of regulations currently; it is impossible to check some important video materials in the first time, etc.
In response to the above problems, Shanghai Renwei Electronic Technology Co., Ltd. adopts advanced Internet of Things technology to develop a set of all-time-space RFID intelligent positioning system. As my country’s key development of strategic emerging industries, the Internet of Things, in addition to social applications, also has important applications and broad development prospects in the prison field.
In the new era and new stage, it has become a trend to transform the prison’s management mode for reform personnel and improve the level of prison information.
2. System introduction
RFID is a communication technology that can identify specific targets and read and write related data through radio signals without the need to establish mechanical or optical contact between the identification system and specific targets. Therefore, RFID is a non-contact automatic identification technology, which can quickly read and write, and long-term tracking management, so it is widely favored in the field of intelligent identification. At the same time, with the rapid development of the Internet of Things technology in my country, RFID technology, as the supporting technology of the Internet of Things, is considered to be one of the promising information technologies. In the next few years, more products will be implanted with RFID tags, and the application of RFID technology will be quite extensive.
Location service is a technology that is very popular and valued by people. At present, the well-known positioning service is GPS (Global Positioning System), as well as the Beidou positioning system of our country; and more and more other wireless network technologies have also begun to enter the field of positioning services, such as GSM mobile phone positioning, Wi-Fi positioning, RFID positioning, ZigBee positioning, Bluetooth positioning, etc. The widespread use of RFID technology in the Internet of Things makes RFID positioning already have great advantages in indoor and other specific areas.
The all-time RFID intelligent positioning system is a regional positioning system. It uses high-frequency 2.4G and low-frequency 125K RFID technology to automatically identify people and objects and localize them to realize the management of people and objects, such as : Personnel attendance, personnel and item search, area limitation of personnel and items, personnel statistics, video linkage, historical track query, key area management, etc.
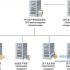
Three, system composition
The full-time RFID positioning system is mainly composed of two parts: positioning equipment and positioning system software.
3.1 Positioning equipment includes:
(1) RFID-2.4GHz positioning base station (also called reader, positioning AP)
The positioning base station is divided into single-frequency and dual-frequency. The frequency of the single-frequency base station is 2.4G, and the frequency of the dual-frequency base station is 2.4G and 125K. In the positioning area.
(2) Positioning label
The location tag is 2.4G plus 125K active RFID electronic tag. The location tag periodically sends out 2.4G signals and receives 125K activation signals. The location tags are divided into two types: personnel location tags and article location tags. The tag has a built-in battery that can be replaced. Because the power consumption of the tag is low, a battery of the personnel tag can be used for more than one year under normal conditions. Personnel tags have wristband type and card type, and function buttons can be customized on the card type. It can be used for request and call or location report function.
(3) Handheld reader
Also called a handheld terminal, it can receive the wireless signal sent by the positioning tag, and display simple information of the person wearing the tag on its own screen. (4) Network equipment
(5) Computers and servers
(6) 125K active antenna
The activation antenna is connected to the dual-frequency base station through a two-core shielded wire. The activation antenna is mainly installed in the entrance and exit area to assist access judgment and positioning. The activation antenna is divided into two types: ground-sensing antenna and rod antenna.
3.2 Positioning system software composition
The all-time-space RFID intelligent positioning system adopts cloud computing technology. Through the design of cloud computing, a large amount of data processing can be completed through multiple servers, avoiding the computational pressure caused by processing all data by a single server. The positioning system software is composed of It consists of four parts.
1. System core program: Mainly responsible for data management and receiving data sent from the data collection terminal, and compare, query, and count the data sent from the collection terminal.
2. Information collection program: It is mainly responsible for collecting the data of positioning tags and performing positioning calculations on the tags.
3. Display terminal program: Responsible for map display, personnel location display, alarm output, etc.
4. Backstage management: Responsible for equipment management, association of personnel and items with tags, file management of personnel and items, location area management, and various query statistics, etc.
Main functions of the system

4. Introduction to personnel monitoring
4.1.1 Real-time positioning of personnel area
It can locate the area of the person wearing the location tag in real time and display it on the map of the monitoring terminal
4.1.2 Regional personnel statistics and electronic roll call
Count the number of attendance and actual attendance in each area, as well as the actual attendance in a specific area, and compare it with the expected attendance to determine whether the attendance is complete. And display the name of the absent person.
4.1.3 Personnel search
At the monitoring terminal, you can enter the person’s name or tag number to find the current location of the designated person’s location, and at the same time pop up a video of the person’s location.
4.1.4 Disappearing alarm
Can focus on monitoring certain tags, when these tags leave the designated area or disappear, the system will find corresponding alarms
4.1.5 Out of bounds, leaving the alarm
Some areas are important areas, and an alarm message will be issued if unauthorized persons enter. It can also be set in some areas that certain personnel are not allowed to leave within a set time, if they leave or disappear, the system alarms.
4.1.6 Alarm for too long detention time
Some specific areas can be set, and the persons to be located cannot enter these areas for more than the specified time, and the system will alarm if the time exceeds the specified time.
4.1.7 Track playback
You can query the movement trajectory of a certain label in a specified time period, and which areas the label has been to during this time period, and generate a report on the trajectory.
4.1.8 Video linkage
A camera can be bound to each positioning device, and the video of the area where the positioning device is located can be called by clicking the map of the positioning device on the map of the monitoring terminal. When there is a specific alarm, the system will automatically call up the video of the area where the alarm occurred.
4.1.9 Temporary authorization of personnel
When a person needs to temporarily enter or leave an important area, he can be temporarily authorized in the system to allow him to enter the important area or leave the work area for a certain period of time.
For example, if the superintendent wants to talk to Zhang Tian, the system can temporarily authorize Zhang San to enter the superintendent’s office for 15 minutes or more.
4.1.10 Electronic label failure alarm
The failure of the electronic tag mainly refers to the low voltage of the tag battery; the wristband worn on the person’s hand is damaged or removed;
As long as the wristband worn on the person’s hand is taken off, the system will give an alarm; whether it is cut or removed with a tool, the system will give an alarm. The system will also prompt when the battery voltage of the label is too low, and the battery needs to be replaced as soon as possible.
4.1.11 Personnel ask for help
There are function buttons on the card-type positioning label. When a person is in danger or needs help in a situation, just press the function button and the system will display the location of the help and call out the nearby camera video.
4.1.12 Itinerary
Personnel schedules can be arranged in advance, such as: Zhang San must work in the workshop at 8:11 in the morning, in the cafeteria between 11:30 and 12, and in the prison from 7 in the evening to 7:30 the next day. If at 9 o’clock, Zhang San left the workshop without authorization and appeared in the cafeteria. The system will warn: Zhang San illegally left the workshop and entered the canteen.
4.1.13 Patrol arrangements
The designated personnel can be arranged to patrol the designated places according to the time period. If the designated personnel do not patrol the designated places within the designated time, the system will alarm. And save the daily patrol records in the record for easy query in the future.
4.2 Item monitoring
4.2.1 Item area positioning
Real-time monitoring of the location information of dangerous goods through electronic maps.
4.2.2 Item search
You can enter the name and number of the item on the monitoring terminal to find the location of the item
4.2.3 Alarm for disappearance of items
When the monitored item disappears on the map, the system will send out an alarm that the item disappears.
4.2.4 Unauthorized alarm
The system will report to the police if the item leaves the designated area without authorization.
4.2.5 Alarm beyond authorized time
When an authorized item exceeds the time allowed for authorization to leave a certain domain, the system alarms.
4.2.6 Alarm for item label destruction
If the label bound to the article is removed, the label will continuously send a removal alarm message to the system.
4.2.7 Low battery alarm
When the voltage of the battery in the label is low, the system will warn that the power of the specified label is insufficient, and the battery needs to be replaced as soon as possible.
V. Introduction to some background functions
5.1 Client login interface

5.2 System main interface

5.3 Illegal entry into important areas
When someone illegally enters an important area, the system will pop up the corresponding video and display the information of the alerter

5.4 Viewing personnel movement tracks
Check the movement track of the person or object by entering the person tag number, ID number, or person name and the time period that needs to be played back.

5.5 Personnel location information display
The humanoid icon on the map represents the real-time location of the person

5.6 Real-time people counting, electronic roll call

5.7 View the location of designated personnel
Enter the tag number or name of the person you want to find to find the current location of the person

Six, successful cases

Shanghai Renwei Electronic Technology Co., Ltd. Tel: 18237875670
[ad_2]