RFID-based inventory management system for important goods and assets
[ad_1]
system introduction
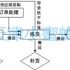
This system uses 2.45G RFIDTechnology, log important item information into the system and write it into the electronic lock. After the important item is locked with the electronic lock, use a 2.45G RFID reader to monitor in real time, including the real-time status, operating time, item number, and item name of the important item And the power of the electronic lock, etc., to realize the real-time monitoring, safety control and alarm of important items. The system is divided into 3 parts:
Log important item information: including item number, name, registration time, etc. The system uses a 2.45G RFID reader to write this information into the electronic lock.
System monitoring: Specify or cancel the items to be monitored and the power of the electronic lock.
Register important item information: including item number, name, registration time, etc. The system uses RFID reader to write this information into the tamper-evident electronic tag.
System alarm:
a. Damaged or unauthorized opening of the electronic lock in the monitoring state
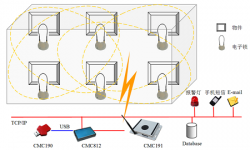
b. Alarm mechanism includes: SMS, Notes Email, alarm light
c. Early warning of insufficient power of the electronic lock or replacement of the electronic lock in advance

The administrator uses CMC190 to write item information into the electronic lock, and CMC812 to log important item information into the system.
After confirming that the electronic lock is in the closed state, lock it on the controlled object.
Place the controlled object within the signal range of CMC191, the system receives the data read by CMC191, monitors the real-time status of the item, and monitors the power of the electronic lock in real time.
When there is a violation of safety rules and CMC191 cannot detect it, the system will send mobile phone text messages, emails, and warning lights to alarm:
a. The electronic lock is artificially damaged
b. The power of the electronic lock is insufficient
c. The electronic lock leaves the monitoring area (stolen with the item)
d. The electronic lock is opened when it is not authorized. As shown in the figure:

System process:

System expansion
The system can use the handheld inventory machine to realize the on-site inventory of important items: download all item information to the handheld inventory machine, and when the inventory personnel approach the items to be inventory, they can sense the item information to prompt the inventory to be completed, and finally import the inventory results into the system.
[ad_2]