RFID Management System for Detention Center Staff
[ad_1]
1. Analysis of the status quo of supervision of prisons
Detainees disobey supervision in the prison, bully, beat and scold fellow prisoners, take the place of duty at night, act as “cell bosses”, and fight fights from time to time. Some detainees feel “indifferent” to whether they have been punished in the prison. , And even after the punishment was completed, most of them still did not learn their lesson and continued to fight and make troubles, laying hidden dangers for the safety of supervision sites.
In terms of management, most of them are still at the stage of patrolling by prison guards and monitoring and alarming by cameras. Manual operations still account for a large proportion, and the degree of informatization is relatively low. It is difficult to achieve real-time supervision of detainees in prisons. Accidents often occur. It is lagging and cannot initiate active proactive prevention and early warning. In addition, information collection is still only relying on manual input, and it is impossible to truly associate the information system with the detainees. In order to ensure the management level of the prison, improve the monitoring status of criminal suspects, improve the efficiency of transformation, and avoid the hysteresis of safety accidents, the construction of information intelligence in the prison has become extremely urgent.
The company relies on the world’s top radio frequency electronic technology experts to integrate the world’s most advanced low-frequency trigger technology, antenna technology, optical communication technology, embedded technology, industrial Ethernet transmission technology, database processing technology, computer software technology, geographic information system technology, Internet technology and other multi-disciplinary comprehensive research topics have been developed and constructed this set of networked prisons’ intelligent management and safety protection system. This system uses the Internet of Things RFID (Radio Frequency Identification) radio frequency identification technology to realize automatic identification, location tracking, early warning and automatic alarm, emergency command and standardizing the behavior of detainees. It uses safe and reliable information collection methods to monitor, track, and identify detainees. Personnel and prison guards truly associate the personal information in the information system with the individuals in reality, and realize real-time tracking and alarming. Only in this way can the prison management be informatized, intelligent, and standardized in a true sense, and “require police force from science and technology”. .
The electronic wristband RW-T711 is a multi-functional composite tag that integrates radio frequency chips in the three frequency bands of 2.4GHz, 125K, and 13.56MHz. This electronic wristband can realize the two basic functions of personnel positioning and personnel identification, so as to use this feature to further realize the cross-border alarm of detainees, cross-regional alarm, designated route monitoring, emergency investigation, prison card management and other management Features. In addition, the electronic wristband for detainees also has an anti-disassembly function to prevent detainees from sabotaging the electronic wristband. The management system is a visual application system that uses RW-T711 electronic tamper-evident wristband to manage and monitor prison guards and detainees according to the needs of all parties in the prison. The system can keep track of the positions of detainees and prison guards, real-time identification, positioning and tracking indoors and outdoors, providing prison managers with valuable real-time location information, condition warning information, active alarm information and other comprehensive management information. At the same time, it enables managers to grasp the number and information of detainees in various controlled areas in the facility in real time, as well as information on prison guards patrolled around, thereby improving the security level of prison guards and equipment. The prison management system also uses the all-in-one card function of the RW-T711 electronic tamper-proof wristband to realize the all-in-one card for internal consumption and attendance in the prison. Through the high-tech functions of RW-T711, the prison intelligent management system finally improves the management efficiency and level of the prison through accurate real-time information methods, so that the management of the prison significantly improves the efficiency and benefits.
2. Significance of system construction
Liberate manpower and save costs
Real-time monitoring of location changes
Security camera, active tracking
Number of regions, real-time statistics
3. System construction requirements
Respond to the supervision situation in a timely manner, strengthen the management of prisoners, strengthen security measures, build Internet of Things applications in public security, and deployInternet of ThingsEquipment and supporting integrated monitoring platform software, real-time location personnel information and timely detection of criminals’ abnormal behaviors, realize joint actions with automated monitoring facilities such as video and access control, improve emergency response speed and incident handling speed, and form civil air defense, technical defense, physical defense, and joint defense The three-dimensional prevention pattern combining four preventions has changed passive supervision to active supervision, effectively improving the management level and efficiency of the prison.
4. The guiding ideology of system construction
The system construction aims to improve the informatization level of prison management work and prevent the occurrence of prison escape incidents. It focuses on real-time, efficient and scientific prison management work, and takes the promotion and full application of information systems as the core, with low investment and high investment. Benefit and focus on quality as the goal, carry out system design and overall planning within the overall framework of the construction of digital informatization prisons, and comprehensively promote supervision in accordance with the overall construction idea of “planning, step-by-step construction, construction while using, and gradual improvement”. The process of informatization and modernization of the management of prisoners.
5. System Overview
The overall design of the “Intelligent Security Management System for Prisons” adopts radio frequency identification technology, computer communication technology, data encryption technology and other cutting-edge high-tech fields to establish a multi-functional personnel positioning system, that is, it has long-distance reading and positioning functions. Dual frequencyelectronic label(2.45G+125KHz) and 2.4GHz signal field strength value judgment and positioning. After the system is completed, it will have a unified management platform and database to provide the most detailed basic data for management decision-making. It is important for the intelligent management and control system of prisons to improve management capabilities through information technology. platform.
The prison’s intelligent security management system consists of three parts. First, the core hardware of the prison’s intelligent security management system (including: anti-disassembly electronic wristband, dual-frequency electronic tag, ceiling-mounted positioning base station, hemispherical read-write Activator, low frequency activator, integrationReaderEtc.); Second, the prison intelligent security management system software (including front-end display software and background management software); third, middleware (including industrial-grade switches, cabinets, PCs, servers, uninterruptible power supplies, etc.) .
The core technology of the system construction adopts the standard 2.4G and 125K low-frequency trigger technology commonly used in the market. All the core equipment provided by the company has completely independent intellectual property rights. 2.4G micro-power technology, wrist strap key type anti-disassembly design, 125K cable Antenna technology, synchronous transceiver mechanism, etc. are all created by the company, which greatly improves the service life and positioning accuracy of the wristband, which far exceeds the domestic industry level.
In terms of the overall system architecture, service equipment selection, wristband label function selection, basic data collection, etc., full consideration is given to the realization of subsequent functions, taking into account the compatibility of equipment, the scalability of the system, the scalability of functions and the diversity of applications sex;
System development and resource construction conform to a unified technical specification and characterization system, pay attention to the continuity and sharing of development work, and pay attention to leaving standardized data and control interfaces for subsequent system development and promotion. Unified development of technical indicators such as application technology, data storage format, signal transmission format, interconnection interface mode, etc.;
6. The working principle of the system
The intelligent security management system of the prison adopts the application of semi-active electronic tags, using electronic tags as the most advanced identification code at present, installing them on controlled targets, and tracking and locating them as the only identifier of the target. At work, managers use networked wireless identification base stations to track and locate targets.
The anti-disassembly electronic wristband works in two modes of “active or passive”. The wristband emits signals actively or is triggered by instructions from a reader (or low-frequency activator). The activators distributed in various areas or inside and outside the access control have been actively transmitting 125KHz low-frequency electromagnetic wave signals at close range, and the anti-removal electronic wristband within the signal range of any activator can be activated smoothly, and the number emitted by the activator can be obtained. Number and calculate the RSSI field strength value. The electronic wristband then wirelessly transmits data such as “tag ID + tag status information (is the voltage normal? Is the anti-disassembly status normal? etc.) + activator number + RSSI value” and other data wirelessly transmitted at 2.4GHz frequency. The long-distance reader/writer antenna installed in the prison cell, the entrance guard, and the air release area receives the carrier signal sent from the anti-removal wristband, and transmits it to the reader through the antenna adjuster, and the reader demodulates and decodes the received signal Then it is sent to the prison’s intelligent security management system software for related processing, and the system judges its legitimacy and location information based on logic.
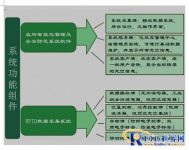
7. System components
The intelligent security management of prisons is mainly composed ofRFIDThe data acquisition system and the prison intelligent management and security system software consist of two parts.

8. System function
1) Real-time tracking and monitoring of controlled targets, automatic position display;
2) Real-time query and print the current and a certain period of time controlled target quantity (production area, surveillance room, corridor, etc.), activity trajectory and distribution;
3) Detainees trespassing in the restricted area backstage will automatically alarm. Some areas are restricted areas. Unauthorized detainees illegally break into the background system and automatically alarm and pop up the video window of the incident; at important gates of the prison, the permission and time period permissions can be set in advance, and unauthorized personnel can enter and exit the gate. Will automatically trigger an alarm;
4) Track playback, prison management personnel and authorized leaders can query the movement track of a certain prison area or a certain group of detainees during a certain period of time according to their own authority;
5) Emergency call for help. When prison guards are besieged by detainees or some detainees find bad intentions, they can press the prison guard card button or pull off the anti-disassembly chain for emergency help;
6) All-in-one card function, the electronic anti-tamper wristband (tag) has a built-in non-contact all-in-one card chip. The prison guard card can realize access control, electronic door lock, inspection, attendance and internal consumption functions, and the electronic wristband of detainees can realize functions such as dining and internal consumption;
7) Query statistics and report functions, the management system can automatically generate various charts that meet the daily management of managers
Including: bar graph, pie graph, curve graph, list, etc. These charts can conveniently help prison managers analyze and count the work and activities of various personnel over a period of time, as well as the occurrence, frequency, location, and cause of various alarm events that are necessary for prison management. Various factors.
8) Video linkage, on-site real-time online; monitoring probes are installed in supervision houses, production areas, living areas, etc., the probes work around the clock, and the information is stored in the memory in real time. When the reader receives a special ID (detainees breaking into unauthorized areas, prison guards being surrounded, etc.), it sends an instruction to the back-end service manager, and a video box pops up on the software, and the manager can instantly query the occurrence of abnormal situations Location and site conditions to avoid dangerous situations;
9. System characteristics
The goal of the implementation of this system is to create a comprehensive business management platform suitable for digital and intelligent prison management. This system has the following characteristics:
9.1.1. High reliability:
The equipment used in the system is designed and produced in accordance with industrial standards. The core adopts a highly integrated embedded system, the backend adopts large-scale database technology, and the main equipment adopts a waterproof and moisture-proof shell, which is fully adapted to the local use environment. 2.4G reader has self-check and heartbeat packet upload function, positioning activator has antenna open circuit and short circuit, power-down self-check alarm function, mobile phone detection terminal application also greatly strengthens the robustness of the overall system, ensuring the use of each system The links are stable and reliable.
9.1.2. Economical and practical:
The cost of system construction and maintenance is relatively low. Compared with other personnel positioning solutions, the comprehensive solution that uses the combination of three-frequency composite card application has low operating costs, high equipment integration, fast construction, high degree of intelligence, convenient maintenance, simple operation, etc. The characteristic is a set of pragmatic and comprehensive system.
9.1.3. Advanced system:
The system adopts the most advanced semi-active and active RFID wireless communication technology, wireless smart card, embedded system, database technology, encryption and other advanced technologies. It is a typical case of advanced technology integration and application. It is a digital and integrated prison personnel management system. A model project of intelligence.
9.1.4. Convenient maintenance:
The system adopts a modular design. When a module fails, only the failed module needs to be replaced, and the system can return to normal. The wireless long-distance card reading method breaks the maintenance of a large number of signal cables in traditional projects. In particular, the 2.45G radio frequency identification reader and 125K positioning activator will report their own working status on a regular basis, and the background management can immediately get system failure prompts when the node is faulty. Shorten the discovery and processing time of sudden failures.
9.1.5. Flexible expansion:
Modular network architecture and radio frequency communication design make the system have good capacity expansion performance. When the system is expanded, only the corresponding network terminal and wireless card reading system hardware need to be added. The 125K low-frequency positioning activator can be flexibly deployed as needed, and the newly added system hardware will be quickly integrated into the existing network, eliminating the need for complicated hardware debugging operations.
9.1.6. Open system:
As a comprehensive application system, its openness is an important condition for system expansion, new service loading, and connection with future new systems. The system has an open structure from the bottom hardware data signal to the software back-end database, which can facilitate the docking with other software and hardware systems of the prison system.
10. Design basis
“Intelligent Building Design Standard” GB/T 50314-2006
“Code for Quality Acceptance of Intelligent Building Engineering” GB 50339-2003
“Code for Construction of Intelligent Building Engineering” GB 50606-2010
“Technical Code for Security Engineering” GB 50348-2004
“Safety Protection System Acceptance Regulations” GA 308-2001
“The People’s Republic of China Security Industry Standard” GA/T94-2005
“Entry and Exit Control System Engineering Design Code” GB 50396-2007
Engineering site drawings and user requirements
11. Overall design of platform system
The personnel positioning system of the prison is a comprehensive management system based on the three-frequency anti-disassembly electronic wristband reading and writing technology. Its fundamental requirement is “information sharing, centralized control”, so the design of the system should not be a simple combination of individual functions, from a unified network platform, a unified database, a unified identity authentication system, data transmission security, various management system interfaces, The technical realization of the overall design ideas of software such as exception handling is considered, so that the intelligentization of the comprehensive performance of each management system and each card-reading terminal equipment achieves the best system design.
11.1. Positioning system management platform
The data management platform and portal management platform are the most important core parts of the prison location management system construction project. The basic personnel management, tag management, access control management, location management, trajectory management, electronic map management, authority management, etc. The system belongs to different application levels of the digital overall support platform. Among them, basic personnel management, electronic map management, and label management belong to the basic data layer of the overall platform, and belong to the basic platform as well as unit management, dictionary library management, and personnel authority management systems; access control Management, location management, and track management belong to the application layer of the overall platform. Therefore, it is necessary to carry out system planning within the framework of the overall support platform of the digital area, and design and develop it as an integral part of the construction of the digital area;
In the construction of the digital prison system, it is necessary to unify the basic information in the prison system, re-plan related business processes, and build and expand the technology platform to achieve the original intention of digital information sharing. The personnel positioning system occupies a very important position in this, and it plays a role in promoting the construction of the entire digital prison.
The personnel positioning system built on the digital prison is not a simple accumulation and collection of card application systems in the prison, nor is it a general-purpose one-card multi-purpose system.
11.2. Unified data platform structure

This positioning system uses cloud computing, and the cloud positioning service (CenterService) is the center of the system. It uses cluster deployment to summarize and distribute tag locations and various alarm information. Support a large number of concurrent connections of information collection programs and monitoring display programs.
System administrators can log in to the web back-end management system through the management terminal, manage file data and system permissions and store them in the database; the web back-end management system also provides statistical report functions.
The cloud collection software (Agent) is responsible for receiving the location information and alarm information of the tag reported by the RFID receiver in real time, and preprocessing the information periodically, using a complex positioning algorithm to locate the location of the tag on a certain receiver. Then report the processed positioning information to the cloud positioning service. Agent has an intelligent load detection function, which can automatically report location information to the cloud location service with lower load.
The cloud location service further processes the location information reported by the Agent, periodically counts the number of people in each area, and judges whether the person illegally leaves the specified area or enters the key area illegally according to each person’s daily itinerary. The personnel statistics information of the area can be displayed on the LED screen on a regular basis. The alarm information and label location information can be output, and information can be integrated with third-party systems.
After the system administrator logs in to the cloud location service through the monitor display program (Monitor), they can receive the location information of the tag in real time and display it on the interface through animation; receive various alarm information in real time and remind them through sound and light. System administrator. The monitoring display program can also obtain the video image of the camera through the hard disk video recorder to further understand the scene of the positioning scene and respond in a timely manner.
11.3. Unified portal management platform structure

Figure 2 Unified portal architecture diagram
The portal platform of the prison’s intelligent security management system adopts a one-stop customized platform service, one-stop service center: The one-stop service center implements service publishing and customization based on portal technology, and one-stop services can be established in the portal according to different user types Template, when the user first uses the portal, the portal already contains one-stop service for the user type. On this basis, the user can adjust according to personal needs and preferences, customize various information within the scope of his authority, including self-selection of the page Style, adjust the order of menus, define your own content pages, etc., bring great convenience for users to use digital prison services. The system environment is built in the information management center, and the platforms are respectively deployed on the data server and application platform server. The application maintenance of the system is managed by the information management center. The management center sets up a card management office to uniformly manage system application permissions and user card issuance. .
11.4. Application authority management:
In the traditional mode, separate user authentication and authorization systems must be established for different application systems of users. In this way, on the one hand, it will cause the repeated placement of user authentication information in the databases of multiple application systems, resulting in a large amount of data redundancy, and the user management modules of each application system will inevitably be developed repeatedly, giving the system’s user authentication information management And the user’s use causes a lot of inconvenience (for example, users need to register or change their own authentication information, they must do it one by one in all application systems); on the other hand, when users switch between different application systems, they must repeat multiple Logins. In addition, the traditional development model is based on the user authentication information management model of the relational database, the data reading speed is slow, and the portability is poor. At present, many shortcomings of user authentication in these traditional development models have seriously affected the performance and ease of use of Web-based application systems.
The authority management under the unified portal provides an efficient directory-based authentication service by establishing authoritative user information of the enterprise, and uses different authentication methods for various applications to achieve the effect that users can access different application systems with a set of user names and passwords. In system applications, when users log in to the digital positioning system, they must pass the identity verification of the unified identity authentication gateway. After passing the verification, the user enters the digital positioning portal and other application systems, and can roam between applications without having to log in repeatedly. At the same time, based on hierarchical authorization, it can effectively control the user’s access and operation authority to different systems. The unified application authority management system guarantees the overall security and reliability of the system, and at the same time brings great convenience for users at all levels of the prison to use software functions and information resources.
11.5. User card issuance management:
Responsible for the management of the wristband and the management of personnel, as well as the maintenance of the public information of the system, etc.
The main functions are:
Very complete wristband management functions such as wristband use, wristband return, and broken wristband registration;
Equipped with various card account management functions such as wristbands and prison guard cards;
Provide a wealth of wristbands, prison guard card queries, and statistical reports;
Responsible for the daily management of various card wristband distribution, wristband recycling, wristband recharge, loss report, unhooking, card replacement, wristband flow query, password modification, etc.
Maintain system public information
Generate various settlement reports for wristband operators
Provide the authorization cancellation function of various core business modules
Provide operator management
[ad_2]






