RIFD meeting automatic sign-in system, automatic integration to avoid human intervention
[ad_1]
1. System significance
1. The meeting is automatically reported, and the statistical results of the names, photos and number of participants are displayed in real time. The whole process is automatically completed to avoid human intervention;
2. The reporting process is simple, fast and has complete report and query functions;
2. System architecture and program description
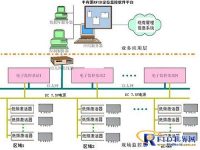
This system integrates automatic identification technology, computer network technology and projection technology to form an integrated system for meeting automatic registration. Its working mechanism is: the electronic card is activated by the electromagnetic interrogation signal continuously emitted by the card reader, and a response signal carrying the electronic card number is fed back to the card reader. It is through the signal between the electronic card and the reader. Inquiry and response, the card reader can accurately and quickly identify the number carried in the electronic card, and output the read electronic card number to the computer, external controller or other terminal equipment in a certain output format, so as to realize the electronic Identification of the card. When a representative wearing an electronic card arrives at the entrance of the check-in terminal, the nearby card reader transmits the read electronic card number to the check-in terminal via Ethernet, and the check-in terminal transmits the data through the computer network (the read electronic card) Number) to the remote computer server. In this way, the check-in terminal and the query terminal connected to the server can update the data in real time: the check-in terminal displays real-time information such as the photo and name of the channel representative, and the query terminal displays the real-time situation and statistical data of the meeting report in real time, such as the number of people, The actual number of people and the number of people who have not arrived.
2.1 System architecture


2.2 Program description

Install a low-frequency activator for each access control that needs to be managed, and each activator leads to 2 low-frequency activation antennas, namely No. 1 antenna and No. 2 antenna, which are arranged on the outside and inside of the door, and one is installed next to the door. The 2.45G long-distance reader/writer independently developed and produced by our company uses Suzhou Xindao as the signal receiver.Semi-activeRFIDThe low-frequency activation tag is activated by the activation antenna No. 1 and activation antenna No. 2 in turn when entering the access control, so that the system judges that the person has entered the access control. On the contrary, the system recognizes that it is going out. This completes the management of the entire access control system personnel entry and exit judgment.
[ad_2]





