Alcohol anti-counterfeiting solution based on UHF security tags with security algorithms
[ad_1]
In recent years, alcohol fraud has occurred frequently, and how to prevent counterfeiting of alcohol has become a concern of major wine merchants. Commonly used alcohol anti-counterfeiting technologies include physical destruction, fragile labels, laser anti-counterfeiting, and code telephone inquiries. With the development and maturity of technology, RFID has been used by major wine merchants as one of the important means of anti-counterfeiting in the future because of its unique label identification and strong anti-copying ability.
At present, the following four problems need to be solved in the application of RFID alcohol anti-counterfeiting:
1. The RFID anti-counterfeiting label must be completely destroyed after the product is used and cannot be used again;
2. RFID anti-counterfeiting labels must be unique and cannot be copied during use;
3. Provide consumers with simple and easy means of counterfeiting;
4. Meet the needs of traceability management.
For the first problem, fragile anti-counterfeiting labels are mainly used to solve the problem. This method is used in the production process to paste anti-counterfeiting labels on the upper and lower parts of the bottle cap by manual or mechanical pasting. When used, the labels are broken through special adhesive and fragile substrates, which can effectively prevent anti-counterfeiting. The label was illegally transferred. The second problem is to use the uniqueness of the GEN2 protocol UHF tag TID and the feature that the TID cannot be modified after the tag leaves the factory to achieve anti-counterfeiting. However, the UHF tag TID can be easily obtained by universal readers, and there are security loopholes. In addition, driven by profit, it is easy to produce new counterfeit products. Therefore, this problem still has security risks. The third problem is to realize the inquiry by providing an all-in-one inquiry machine or an anti-counterfeiting code on the label surface. However, the high cost of the all-in-one inquiry machine cannot be popularized, and the usage rate of inquiring through the anti-counterfeiting code on the label surface does not exceed 4%. It is very necessary for consumers to provide simple and easy counterfeiting methods. The fourth problem is currently using high-frequency labels to identify single products. Data collection and management are mainly through the use of ultra-high frequency box labels attached to wine packaging boxes to achieve wine traceability. This method greatly increases the management cost of the traceability link and brings a greater cost burden to the enterprise.
In response to the above problems, our company has launched a complete set of alcohol anti-counterfeiting solutions based on UHF tags with security algorithms. Consumers provide a convenient way to query, and provide long-distance, multi-label inventory functions for wine traceability.
An Introduction
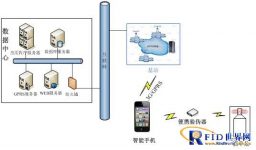
The consumer counterfeit verification system in the scheme is shown in Figure 1. There are four main components: data center, consumer smart phone terminal, portable counterfeit detector and anti-counterfeit electronic tag (integrated with the wine item to be checked).

Figure 1 Schematic diagram of consumer counterfeiting system
Component function
Data Center: Complete verification of portable counterfeit detectors and anti-counterfeit electronic tags.
Consumer smart phones: As the transmission channel between the data center and the portable counterfeit detector, install counterfeit checking software.
Portable forgery verification device: It has a unique portable forgery verification device ID number and its corresponding portable forgery verification device authentication key, and integrates SM1 algorithm and SM7 algorithm.
Wine list product (anti-counterfeiting electronic label): The anti-counterfeiting electronic label is affixed to the joint part of the wine list bottle cap to realize anti-transfer.
Realization principle
The anti-counterfeiting electronic label is a chip product independently developed by Huada Electronics and has independent intellectual property rights. This product is an ultra-low power consumption, long-distance identification communication, UHF passive electronic tag chip with domestic SM7 algorithm, provides a unique identification number, has 512bits of user storage space (divided into general subarea and security subarea) and 160bits The main feature of the UII storage space is to realize the two-way authentication and information flow encryption between the reader and the anti-counterfeiting electronic tag. The following is a brief introduction to the implementation method.
Two-way identification
Anti-counterfeiting electronic tags and portable readers can achieve two-way identity authentication during use: the identity authentication of the electronic tags adopts the triple identity authentication mechanism encrypted by the SM7 national cryptographic algorithm, and the encryption and decryption operations required for identity authentication can only be performed in the security of the reader The module and tag chip are carried out in the security sub-area, and the authentication process is shown in Figure 2.

Figure 2 Identification process
The specific process is divided into the following steps:
1) The portable forgery verifier sends an authentication command.
2) After the anti-counterfeiting electronic tag receives the authentication instruction, the anti-counterfeiting electronic tag sends a random number RT to the portable forgery verifier.
3) The portable forgery verifier generates a random number RR after receiving RT, encrypts RR and RT through SM7 to obtain Token1, and sends Token1 to the anti-counterfeiting electronic label.
4) After the anti-counterfeiting electronic tag receives Token1, it decrypts it with SM7 algorithm to obtain RR’ and RT’. Compare RT’ and RT. If RT’ is consistent with RT, the anti-counterfeiting electronic tag generates a new random number RT”, and encrypts RT” and RR’ to form Token2.
5) After the reader receives Token2, decrypt it with SM7 algorithm to get RR”. Compare RR” and RR, if RR” is consistent with RR, the authentication is passed.
Information flow encryption
This scheme uses symmetric cryptographic algorithm encryption for the bidirectional data transmission between the anti-counterfeiting electronic tag and the portable counterfeit detector to ensure that the transmission information is transmitted in ciphertext form, and the imitator cannot obtain the plaintext data, thereby ensuring the security of information transmission in the secure sub-area.
The portable forgery verifier performs data transmission between the user’s mobile phone and the data center, and the upstream data is encrypted using the symmetric cryptographic algorithm SM1. Effectively respond to security threats such as eavesdropping and data interpretation that are faced in the process of mobile phone transmission. The imitator cannot obtain the plaintext data, thereby preventing the leakage of label security information and the security of the label authentication key.
Long-distance, multi-tag reading
The label adds anti-counterfeiting authentication and information security functions, while retaining the original application advantages of UHF labels, which can ensure the realization of single product management, rapid warehousing management, and anti-crossing management in the traceability of wine, thereby reducing wine The cost of traceability management. Among them, the advantages of UHF tags and higher frequency tags are as follows:

Summarize
Starting from the need for wine traceability and anti-counterfeiting, this solution uses self-developed UHF anti-counterfeiting electronic tags and portable counterfeit detectors to support the use of anti-counterfeiting electronic tags and data transmission through the national secret SM1 and SM7 algorithms, effectively solving the identification of anti-counterfeiting electronic tags Security issues of process, information and information transmission; through the customized professional design of tag antennas, the superior reading performance of anti-counterfeiting electronic tags can be achieved, which can be combined with enterprise logistics and applied in traceability management to improve the level of enterprise logistics management and realize wine Traceability; the portable counterfeit checker provides consumers with a convenient and quick way to inquire, ensuring that the anti-counterfeiting method can be recognized and used by consumers.
[ad_2]



