New Force Personnel Access Control and Attendance Management System Solution
[ad_1]
1. System Overview
1.1. System background
With the rapid development of social economy and technology, radio frequency identification technology has become more and more widely used in various industries, especially identification and security industries. The traditional attendance methods are too outdated, and when there are too many attendance personnel, it will cause queuing. The situation affects efficiency and corporate image. At the same time, the access control system as an important unit of the intelligent building is getting more and more attention. The traditional access control system uses mechanical locks and swipe card authentication methods, which require close operation, which is extremely inconvenient and easy to lose when the user’s hands are occupied. , Copying, and being embezzled, the cost is also relatively high.
1.2. Status Quo and Analysis
The emergence of radio frequency identification technology has made up for these shortcomings, and radio frequency tags are non-contact, fast in reading and writing, low power consumption, and long in reading distance. This system uses RFID technology, using 13.56MHz, UHF915MHz or 2.4GHz technology. The access control controller, computer technology and personnel attendance management software have designed a high-security intelligent access control attendance system, and an intelligent access control attendance system that quickly confirms the real identity of personnel through RFID authentication. When the user enters the detection range of the access control time and attendance system, the system will automatically obtain the identity information to determine whether the user is a legitimate user, and record the attendance information of the entry and exit personnel, and send an alarm signal to the illegal intruder.
For user units that need to implement automated personnel access control and attendance systems, they generally have the following requirements:
1) Attendance and access control all-in-one card, which can be used as an access control card while realizing attendance;
2) It can be set for late arrival, business trip, leave entry and automatic deduction;
3) The detailed records of attendance and access of each individual can be easily inquired through the computer of the system.
2.system introduction
2.1. The working principle of the system
This system uses RFID radio frequency identification technology for personnel access control attendance management. All employees wear an RFID electronic tag as an access control attendance card. It is used to record the attendance when on and off work, as long as the tag is within the valid recognition range of the reader, the reader can automatically recognize the tag information, if it is a valid card, it will automatically record the attendance information through the software system and control the electronic lock to open the door . If it is an invalid card, the alarm device will be activated through the access controller.
RFID radio frequency identification is a non-contact automatic identification technology, which automatically recognizes the target object and obtains related data through radio frequency signals. The identification work does not require manual intervention and can work in various harsh environments. RFID technology can identify high-speed moving objects and can identify multiple tags at the same time, and the operation is quick and convenient. The RFID system is mainly composed of three parts: a reader, an antenna and a tag. It has the following characteristics:
1) Non-contact identification;
2) Object identification: The tag has a unique ID number to realize the unique identification of the object;
3) Long recognition distance: different RFID frequency band technologies can be used to achieve different field requirements;
4) Anti-conflict: a large number of tags can be identified at one time;
5) Strong anti-interference ability: RFID wireless identification can be used in harsh environments and can work normally.
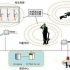
2.2. System topology diagram
The structure of the system consists of the following parts:
1) RFID readers, antennas and tags, RFID card issuers
2) System server computer
3) Access control software (collect infrared detector signals and control RFID reader identification)
4) Voice prompt speaker
5) Electronic door lock
6) Access control attendance machine
7) Staff attendance management software (employee entry card issuance, attendance information setting, printing report, etc.)
.jpg)
Figure 1: System topology diagram
2.3.System functions
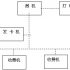
The system has three important components: information management module, RFID access control software and attendance management software. The information management module is responsible for authorizing users, and attendance management and access control are the main functions realized by this system.
.jpg)
2.3.1. Information Management Module
The information management module mainly distributes RFID tags to all personnel, and can authorize users at the same time. Information management is roughly divided into the following three parts:
1) Add user information: Add new RFID tags for new employees or employees who have reissued cards, authorize the tags, and correspond to personnel information and RFID tags.
2) Deletion of user information: In case of employee resignation, etc., the employee’s RFID tag will be scrapped and related information will be deleted.
3) User information modification: RFID tags need to be re-managed in situations such as changes in employee positions, and the corresponding personnel information needs to be modified.
2.3.2. Attendance Management Module
The attendance management module includes manual attendance, intelligent attendance and attendance time settings.
a. Manual attendance: In case of special circumstances, such as label loss, damage, etc., the administrator can supplement it through manual attendance.
b. Intelligent attendance: The use of long-distance RFID cards for attendance saves time, without manual intervention, improves work efficiency and reduces the possibility of errors.
c. Attendance time setting: Attendance time setting refers to the time when the attendance system is activated. During the set time period, the attendance system works normally. After this time period, the system will shut down.
d. Attendance record query: The system administrator can query the attendance record of an employee or the overall attendance record of a certain department through the system, and it can be printed into a report for easy management.
2.3.3. Access Control Module
The access control module includes electronic lock control and alarm control,
Electronic lock control: The main function is an open and close function of the electronic lock switch, which is the realization of intelligent access control.
Alarm control: Voice alarm for illegal card users who try to enter the enterprise to act as a warning.
2.3.4. Smart attendance and access control workflow
When the RFID tag holder enters the working area of the reader, the reader recognizes the RFID tag, and the host authenticates and judges the identity of the tag. If the authentication result is true, the host will send the door opening control to the access control and attendance machine. Commands and attendance records, the access control and attendance machine controls the relay after receiving the door opening command, and the energization of the relay causes the magnetic electronic lock electromagnet to conduct conduction to open the door lock.
When the authentication result of the host is false, it is judged that the person entering the door is an illegal user. At this time, the host will send an alarm control command to the access control attendance machine. After the access control attendance machine receives the command, it will immediately drive the alarm module and start the voice prompt. The relevant information of the cardholder who illegally broke into the door is sent to the upper computer, so that the manager can understand the situation in the first time and make it convenient to deal with it.
The system will record and store the relevant information of each incoming person in the database of the server for management. Regardless of legal or illegal persons, the system will record and store authentication results, personnel information, time, and door lock status or alarms and other information. The specific process is shown in Figure 3:
.jpg)
Figure 3: Work Flow Chart of Access Control and Time Attendance
3.Technical selection
Regarding the RFID personnel access control and attendance system, 13.56MHz, 915MHz passive reading and writing systems and 2.4GHz active reading and writing systems can be used to implement. For different applications, different frequency bands can be adopted.
3.1. 13.56MHz Time Attendance System
The 13.56MHz identification tag is within 10cm and is mainly used in short-range attendance systems, such as manual card swiping by personnel.
3.2. 915MHz RFID technology
When the personnel are not very dense, the area is relatively wide, the tags will not be blocked by other personnel (such as personnel entering the attendance area in turn), and when the cost is more sensitive, 915MHz RFID can be used, which has the following advantages:
1) Realize long-distance card reading. According to different models of products, 0-10 meters of label information can be read, so as to realize long-distance automatic attendance;
2) The tag is light in weight, and employees can use the tagging method;
3) The label adopts a passive design method and has a long service life;
4) There are many kinds of labels, and the cost is low;
5) The reader has strong anti-collision ability and can identify multiple tags at one time.
3.3. Active RFID technology
When the application is crowded with people and the tag will be hidden by the human body, 2.4GHz or 433MHz RFID can be used. This system has the following advantages:
1) The tag is powered by a battery, and the distance it can be recognized by the reader is longer, and it can be adjusted from 0 to 100 meters;
2) The penetrating ability is strong, and it is not affected by being blocked by the human body. The label can be placed in the bag, pocket, etc.;
3) Strong anti-collision ability, can identify more than 500 tags at a time.
4. System Features
1) Long-distance automatic attendance, no need to manually swipe the card;
2) It can synchronize attendance for multiple people to avoid queuing;
3) Diverse configurations, which can set permissions for personnel;
4) Equipped with illegal alarm device to avoid illegal entry by outsiders;
5) The operation of the system is simple and practical, and the maintenance is simple.
5. Other application areas
Attendance management for campuses, mines, enterprises, etc.
Workshop work timing
Sign-in management for enterprises, patrols, meetings, etc.
6.Recommended hardware equipment selection
.jpg)
.jpg)
.jpg)
[ad_2]