Simple analysis of access control system based on RFID technology
[ad_1]
Automation, informationization, and intelligence have become the needs of the development of the times. Since the beginning of the 21st century, infinite technology and computer technology have continued to develop in depth, and the Internet of Things industry is booming. The access control system based on RFID technology is a good embodiment of the practicality of the Internet of Things. The access control system can be divided into the following three categories according to the way of access identification: password identification; card identification; biometric identification. Password identification is to identify access rights by checking whether the input password is correct. The security of password identification is relatively high, but the password is easy to forget, and it is cumbersome to enter the password every time you enter the door. Biometric identification is to identify people through some biological characteristics. Biometric identification is highly safe and very convenient, but its high cost makes it difficult to be popularized. Card identification is divided into two categories: the first is the use of magnetic cards, but magnetic cards are low in security, easy to wear and require frequent magnetization; the second is RFID cards, which are cheap, easy to use, safe and can use databases It is well managed, its cost-effectiveness is extremely high, and it has good promotion prospects.

In summary, this article introduces an access control system based on RFID technology, which has low cost and high security. Ability to view information about the access control system in real time.
1 Overall structure and working principle
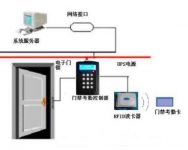
The overall system architecture consists of two parts: the upper computer server management system and the lower computer card reader. The lower computer card reader mainly consists of 6 parts: power supply, main controller, liquid crystal display, card reader module, antenna, and serial communication. Among them, the card reader module M102GPCV3 adopts 13.56MHz non-contact radio frequency technology, which can read MifareOne S50, S70, FM11RF08 and compatible cards. The LCD displays some prompt information and time and date. The serial port is used for communication between the lower computer and the upper computer server. The upper computer server management system uses the database MySQL database management, and the specific management interface is displayed in the form of web pages.
The working principle of the entire access control system is: one person, one card, and the corresponding personal information is established in the database management system according to the serial number of the card. When you want to open the door, swipe the card on the lower computer. The card reader of the lower computer transmits the serial number to the upper computer server. The server queries the corresponding personal information in the database according to the serial number and transmits it to the lower computer. At the same time, the lower computer reads the data of the fixed sector block of the card (card reading), compares the read data with the data sent by the upper computer, and opens the door if they are exactly the same, otherwise an error is displayed on the LCD and the door does not open. All the above information will be uploaded to the upper computer management system for storage. The upper computer management system can change the data information set by the lower computer (write card).
2 System hardware design
2.1 Overall hardware design
The main controller of the access control system is the ARM-STM32F103VET6 chip with Codex-M3 core, the main frequency is 72MHz, the on-chip 512KB FLASH, and multiple USART controllers are built in, which are respectively used for the RFID read/write module connection and the communication of the host computer. The read/write module adopts the M102GPCV3 module with a working frequency of 13.56MHz. The main control board uses the JTAG port for program debugging and downloading, and the LM117 provides 3.3V and 5V voltages for the system board. The I/O port is connected to 12864 LCD, which is used to display relevant prompt information and time and date. USART1 is connected with the card reader module to read card information, and USART2 is connected with MAX232 to communicate with the host computer.
2.2 The hardware design of the card reader module and the main controller circuit
The M102GPCV3 read-write module design provides two interface modes: 10Mb/s I2C bus mode, up to 1228.8Kb/s UART mode. UART mode is adopted here, and card information is read and written through M102GPCV3.
3 System software design
3.1 The overall software design of the system
The overall software design of the access control system includes the software design of the card reader of the lower computer and the software design of the upper computer database management system. The card reader of the lower computer of the access control system mainly realizes the reading of the card and the communication with the upper computer management system, which is realized by C language programming in the Keil4 environment. The upper computer management system is written with Myecfipse and Firefox programming aids. As shown in Figure 3.
3.2 The software design of the card reader system of the lower computer
The lower-level computer access control card reader system is shown in Figure 4. The lower-level computer reader system needs to follow the ISO14443TYPEA standard transmission protocol, that is, follow the order of card detection → anti-collision → card selection → key authentication → block reading. In anti-collision, the serial number is read out, transmitted to the upper computer management system, and saved to the database management system. The data read by the read block is compared with the set data and judged.
3.3 The software design of the upper computer database management system
The upper computer database management system records and publishes information when cardholders swipe their cards to enter the door, as well as add, delete, and modify cardholder information and permissions. The information is stored in the database, and the information table is made in the Java language and posted on the website. Ordinary users can log in to an ordinary account to access the LAN website and query information about the access control system. The administrator can log in through the administrator account to modify the card information and permissions.
4 Conclusion
Through many physical tests, the RFID access control system designed by this scheme is safe, reliable and easy to use. And compared to other access control systems, it has a very high cost performance. With the rapid development of the Internet of Things technology in the world and the promotion of my country’s Golden Card Project, it is believed that RFID technology will be more and more applied to all walks of life. RFID-based banning systems will also develop with this trend. Facts also prove that, according to statistics, RFID access control sales accounted for 87.2% of the entire security market in 2008.
[ad_2]



