Barrier-free personnel management system solutions
[ad_1]
1. System introduction
“Free Flow People Tracking System (FFPTS)” also known as “Personnel Accessibility Tracking Management System” is a management method for people developed with the development of modern automatic identification technology. With the development of radio frequency identification technology (RFID), FFPT has attracted unprecedented attention and invested a lot of effort in research and implementation. The so-called free tracking management of personnel is to complete the automatic identification and tracking of the object or the group of objects without any behavioral norms and restrictions on the personnel (recognition objects) entering a certain recognition area, so as to achieve the purpose of management. Of course, considering issues such as the privacy rights of the identified object, such free tracking and identification should be done in good faith and be informed that the system exists.
RFID technology has a long history of being used in personnel identification. One of the earliest applications of RFID is in access control management. The application of RFID in access control management can be regarded as the initial stage of personnel management, using a low-frequency RFID system. This low-frequency system is inexpensive, but there are also many technical problems. For example, in this management mode, since the low-frequency system does not have anti-collision characteristics and the recognition distance is short (usually less than 5 cm in the system used for access control), the behavior of the managed person is severely restricted and must be close to each other one by one. Distance recognition. Not to mention tracking and management on occasions other than access control. In recent years, people have begun to use high-frequency (13.56MHZ) RFID to build personnel management systems, and have achieved good application effects.
Compared with the low-frequency system, the high-frequency system has a longer identification distance, good anti-collision characteristics, and has a certain penetration ability to the human body. Therefore, the high-frequency RFID system can be used to manufacture the FFPTS system. The FFPTS system manufactured by using high-frequency RFID technology has the following characteristics:
In real life, due to the “liberalization” of human behavior, there is great arbitrariness. Therefore, in the management of human identification and tracking, problems such as long-distance and simultaneous identification of multiple targets are often encountered. It adopts high-frequency passive multiple targets, is cheap, and has no harmful radiation to the human body. It is an ideal RFID product for personnel identification.
From the perspective of practical application, build a free tracking and management network system for personnel. The local area network and wireless network communication system are used to process and distribute the individual data of the identified personnel and objects in a timely manner, with the concept of real-time. Therefore, for different application occasions, requirements for environmental adaptability and common interface characteristics will be put forward for the RFID system.
The RFID system developed in this project will solve these problems well;
Well-intentioned barrier-free tracking management, humanized management revolution. The research and development of this project provides a brand-new technical path for personnel tracking management on specific occasions. The management system reform brought about by the implementation of this technical solution is revolutionary and humane.
Develop an advanced FFPTS system based on RFID technology to break the monopoly of foreign technology. This FFPT system includes conference management systems of various scales, and its technology and management level can be comparable to or even surpassed similar foreign products. This has set up technical barriers for similar foreign products to enter the Chinese market.
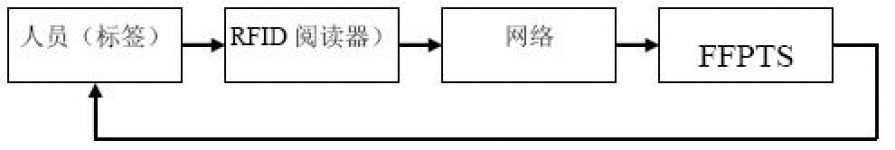
In the FFPTS system based on RFID technology, the most critical basic components are the RFID tag and the reader. These two basic components constitute the basic part of the RFID identification system.
In addition to the most basic reader and tag components, the components of the RFID system also include middleware, network, application software and other components. Different application systems have different requirements for RFID, but they also have the same characteristics. For a large-scale application system, they all include the following parts: ①front-end RFID data acquisition system, ②middleware, ③data transmission network, ④computer system, ⑤Automatic control and display system (including dynamic perception), ⑥Image acquisition and processing system, ⑦Backstage software platform and RFID data system related business systems, such as FFPTS, etc.

Figure 1-1 Schematic diagram of RFID FFPT system
In the above system, the RFID reader obtains the individual information of the object from the tag worn by the person, and transmits it to the FFPTS through the network. The system completes the free tracking management of the identified object based on the returned information.
The complete FFPTS system includes RFID acquisition system; display and operating system; automatic control system; image acquisition and processing system; document management and certification system; central monitoring system; central management system; central database; network and communication system; online work System; encryption system; other application systems (personnel positioning system, attendance system, query statistics system, etc.); ground frame antenna and other systems.
2. Function overview
Implement unified and standardized management of the personnel and vehicles involved in the system to realize the digitization and informatization of the information of the identified objects and the standardization and systematization of the overall process.
Specific requirements are as follows:
All involved persons and vehicle information are entered into the database for unified management, and RFID tags are used for identification;
Set up verification channels in important passage places and areas to achieve “undocumented is difficult to move, leaving marks everywhere with the certificate”;
Realize hand-free verification mode, concealed installation or camouflage of card reader antenna, long-distance sensing capability, and pass verification without noticing the holder;
The identification and control of monitoring points must be accurate, real-time, and have a complete monitoring mechanism and post-audit capabilities;
A set of convenient and easy operation procedures shall be formulated for the control of outside personnel and vehicles of the system, and the supervision function of the system shall be fully utilized for perfect and effective management;
All links of the system operation, especially the certification link, must have good security and confidentiality;
The system itself must have redundancy design and disaster recovery function, and have a complete set of data backup and recovery mechanism;
The system provides a complete interface for function expansion and system upgrades; such as: adding attendance functions, dining, medical and other all-in-one card functions; adding personnel positioning functions; adding important items and document tracking functions; adding vehicle identification functions; managing and producing user units Multiple documents;
Conditions and restrictions.
The original network conditions of the user unit and some of the equipment that may be reused, as well as the original management system and process of the user unit, may have a positive or negative impact in the design of the new system and need to be optimized, modified or reused.
3. Overall design
1. Processing flow
Refer to Figure 3-1 for the standard system structure diagram of the entire system (may need to be adjusted according to site conditions)
2. Verification point staff processing flow
Refer to Figure 3-2 Verification System Work Flow Chart and Figure 3-3 Verification System Flow Chart
As far as the verification system is concerned, its functional positioning should be “assisting the staff on duty to check and verify the identity of the vehicles, people, and objects requested to pass, and to record the passing incidents.”

Figure 3-1 System structure diagram
For the personnel on duty (sentinel):
When it is an internal personnel, after entering the personnel identification area, the system will automatically detect its ID, and directly display its personal information, whether it has the access area authority and other information on the display terminal, and the personnel on duty will determine after comparison and judgment. Whether it is the person and whether he has the permission to pass, and decide whether to let it go.
For internal personnel who have not brought a certificate, they can judge whether to release by entering a positive number on the duty terminal. If there is no record, they will be processed by the duty room.
The external personnel who carry the visitor card are the same as the internal personnel who have the certificate.
For the duty room:
The processing status of the personnel on duty will be simultaneously displayed on the terminal in the duty room.
The duty room is responsible for the registration of outsiders or undocumented insiders and vehicles.
The handling of external personnel and internal undocumented personnel is basically the same. The duty room directly queries the reserved visitor list through the duty computer. If there is a record, the visitor card will be issued. If it is not approved, the approver will be contacted.
For the approver:
For reserved visitors, the approver can directly log in to the “Approval Module of Electronic Identity Management System” in WEB mode, directly enter the visitor’s information, and approve the passage. This operation is protected by the account password and is verified by a digital signature, and the approver will only be able to see the approval information and records corresponding to the person. In this way, the approved person can directly check the identity with the duty room and obtain the visitor card after arriving at the verification area. The card is used as an identity certificate for entering the controlled area and has an expiration date, which will be returned when you leave.
For visitors who have not made an appointment, the operator of the duty room will directly enter the information of the person (car) to be approved and submit it to the approver, so that the approver will give an approval after logging in (or notify the approver by calling to get the approval), Issue a visitor card.
3. Computer system processing flow
The verification point system is in a long-term operation state, and the monitoring of the terminal on duty and the terminal center in the duty room simultaneously displays the monitoring status of the verification point area.
Verification point system loop detection:
Wireless infrared (or thermal) equipment to obtain personnel passing information
RFID reader (antenna) to obtain RFID tag information
The capture camera records the image of the monitoring point when it is triggered
When obtaining personnel pass tag information or RFID tag information, the system triggers the personnel processing module to process the electronic document record corresponding to the RFID tag. Query the internal personnel database and external personnel database. If there are records, the corresponding records will be displayed; otherwise, the corresponding event will be prompted and handed over to the duty room for processing.
? On-duty personnel touch the display terminal
Provide the certificate information display interface.
Provide a manual query interface for certificates.
Provide SMS notification display interface.
Provide a simple communication interface.
Can be equipped with an internal phone platform.
4. Approval Process
For approvers, they can log in to the system for approval management (within the scope of their authority) at any time, and all their operations will be recorded. And you can inquire about the entry status and historical records of its approved persons.

Figure 3-4 Approval flow chart
Four, function allocation
1. Verification point system (institution)
The verification point system includes two parts: the verification point subsystem and the duty room subsystem. It is responsible for the identity authentication and related data recording and processing of the identified objects with electronic certificates (including vehicles and objects identified by automatic license plate recognition technology) . The main functions of the verification point system include:
♦ Supervise (prompt) the identity authentication of the identified object
♦ Perform information retrieval and query on the identified objects (persons, vehicles, objects) with electronic certificates, analyze and process them through predefined rules, and submit the processing results to the upper level for processing.
♦ Alarm for persons and objects without electronic documents
♦ Alert on expired and lost certificates.
♦ Inquiry function under special circumstances (such as the user forgets to bring his ID)
♦ User notification information prompt function (for example, when a user arrives at a certain place, the system prompts “a leader asks you to go to a certain place to do something”).
♦ Notifications triggered by designated events.
♦ Automatically record user events (documents, time, images and other information archive) for inquiries.
♦ Special events are automatically submitted to the duty room and central management system for processing or recording (such as: illegal user events)
♦ The terminal on duty can provide a simple multimedia communication platform.
2. Central Management System (Organization)
The central management system is the management center of the entire electronic identification system. It includes a central management subsystem, a central monitoring subsystem, and a certificate management subsystem. It is responsible for managing and coordinating the operation of the entire system. Its main affairs are:
♦ Various configurations and parameter settings of the entire system
♦ System operator account password and authority management
♦ Monitor and display the working conditions of all personnel verification systems and provide alarms for special situations
♦ Provide statistics and query of all personnel data and user events of the whole system
♦ Classified display of personnel dynamics when the system is running
♦ Generation and printing of various reports
♦ Query positioning of specific personnel
♦ Approval management of external personnel and vehicle entry and exit
♦ Data collection and sorting (manual) of all identified objects (people, vehicles, objects) in the system
♦ Informatization, digitization, sorting and input of the identified object data into the computer system
♦ The production of the electronic certificate of the identified object (including printing or printing)
♦ Authorization of the electronic certificate of the identified object
♦ Production and management of temporary electronic certificates
♦ Management of the extended system: such as one-card system, personnel positioning system, etc.
Five, data structure design
1. Logical structure design
The system logic structure of the system is divided into five layers:
Application layer
Central data layer
Network link layer
Information processing layer
Hardware device layer
Information acquisition equipment and control equipment at the verification point
include:
Personnel RFID equipment, including passive radio frequency readers and antennas.
Personnel infrared detection equipment.
Video and image processing equipment, including cameras, image capture cards
The display terminal is mainly one or more display screens.
Control equipment, possibly used control equipment such as automatic doors, etc.
[Information processing layer]
The identification information obtained through the hardware processing layer is processed by the identification software of the verification point computer. The processed information is stored locally or transmitted to the central data layer for processing through the network link layer.
【Network Link Layer】
Responsible for connecting the data of each verification point with the central data layer through the network equipment to form an organic whole.
【Central Data Layer】
Responsible for the data storage and read-write requirements processing of the entire system. Consists of a database server or an array of database servers.
【Application layer】
This layer includes all data processing and related function expansions attached to the central data layer.
mainly includes:
Central management system (including: central monitoring subsystem, central management subsystem, certificate management subsystem)
Verification point system (including: verification point subsystem, duty room management subsystem)
WEB function expansion subsystem
2. Security and confidentiality design
The RFID equipment currently in use is the most advanced product series at home and abroad, and has passed industrial-grade testing for safety in use. All RFID electronic tags have a globally unique label UID, and there is no possibility of duplication.
All user data is generated and managed independently by the user. The system maintainer only provides guidance on the credential production and management software and the database backup management and other operation instructions. In principle, they do not touch any real user data. (Note: In the early stage of system use, test data can be used to guide users. If users really need it in the future, users can be instructed on site, but no user data will be taken away or copied.)
All data is transmitted in the internal LAN, and the security is protected by the internal network.
The security of the database is managed by the users themselves, and the system maintenance personnel only provide operation guidance.
Any card of the same type from a foreign company will be recognized as an illegal document.
All user operations can set account passwords for operation restrictions and operation log records.
The certificate management system can report loss, deactivate, and cancel specific certificates at any time, and take effect in real time.
In order to ensure the stability of the system, in the case of ensuring the security of the verification point system, a local database can be configured to ensure that the system can still operate normally under network failures.
When entering the verification channel, the document archived photos are automatically recalled for comparison by the personnel on duty, which can prevent fraudulent use.
The certificate card and data registration are divided into individual responsibility. The certificate preparation process is carried out in multiple steps, and after review and approval, the possibility of error is reduced and the possibility of individual certificate preparation is eliminated.
It is convenient to carry out regular and irregular data inspections, and print hard copies for review and archiving.
[ad_2]