Beijing Yingzhike Intelligent Access Control System Design Solution
[ad_1]
Foreword
Beijing Yingzhike Digital Information Technology Co., Ltd. is a high-tech enterprise integrating technology, industry and trade, with security engineering design and construction qualifications. Yingzhike Company has a group of experienced technical developers and construction teams. The company produces and sells ENCYC intelligent access control management system and attendance system, and has the research and development and engineering construction capabilities in environmental monitoring systems, community intelligence, background music, studios, cable TV and satellite receiving systems, and building automation systems. Yingzhike provides customers with a full range of services from program demonstration, equipment selection, engineering design, installation, commissioning, technical training, and after-sales maintenance.
Relying on technology, taking advantage of talents, and based on the business philosophy of “technology, quality, service”, Yingzhike Company is making continuous efforts to make rapid progress towards the development goal of becoming an international first-class high-tech enterprise.
The non-contact smart card system launched by Beijing Yingzhike Digital Information Technology Co., Ltd. has more advanced technology than other similar products, the system is stable and reliable, and the performance-price ratio is good. It can be widely used in various fields. For identification card readers, it can be divided into two categories, namely contact type and non-contact type. The so-called contact card and card reader must insert the identification card into the card reader or swipe in the slot to read the card number. Such cards and card readers have inevitable shortcomings: for example, magnetic cards are susceptible to strong magnetic interference and lose data, are easy to be copied, and are easy to lose data under friction, humidity, heat and other conditions, and have a short service life. The so-called non-contact card and the card reader can read the data in the identification card when they are a certain distance away. Obviously, this kind of card is very convenient to use, as long as the card is hung in front of the chest, placed in the pocket, in the bag, and within the sensing range of the card reader, the door lock will automatically open. Yingzhike access control system uses this non-contact card and card reader.
At present, the access control system has become an extremely important part of the security protection system. In some developed countries, the access control system is developing rapidly at a much higher rate than other types of security products; the reason why the access control system can stand out among many security products, The fundamental reason is that it has changed the passive security methods of past security products such as closed-circuit monitoring, anti-theft alarms, etc., and replaced passive monitoring with active control. The control of the main channel greatly prevents criminals from intruding from the normal channel. And when a crime occurs, it can limit the scope of criminal activity by controlling the access door to stop the crime or reduce the loss.
In recent years, access control systems have quietly emerged in China due to their own advantages. Various types of places including post and telecommunications systems, power supply systems, banking systems, residential communities, resorts and other places have already used access control systems. Through this system The use of has greatly improved the work efficiency of managers and the degree of safety in the management area.
Introduction to ENCYC access control system
1. Brief introduction of access control system
In many places such as factories, schools, offices, shops, financial systems, military systems, residences, hotels, etc., closed management is required for the safety and effectiveness of study, work, and life. The traditional method is for staff to register and release personnel entering and exiting. This method is laborious, laborious and error-prone, and the management is not strict. With the advancement of technology, the access control system has gradually changed from the original key to open the door, to the IC card access control management, and finally to the current non-contact ID card access control system. The non-contact access control system uses personal identification cards to work. A personal identification card is issued to everyone who has the right to enter, which is equivalent to a key. The system judges whether the card holder can enter or exit based on the card number and current time of the card. If so, the system automatically opens the door; otherwise, it does not open the door. For factories, institutions and other places that require attendance, the access control system can also record whether each employee goes to get off work on time. Another advantage of the access control system is that a certain card can be added and deleted at any time. You don’t have to worry about what losses will be caused after a certain card is lost.
Access control system, also known as entrance and exit control system. A modern, fully functional access control system is not only used for import and export management, but also contributes to internal orderly management. It will automatically record the entry and exit of personnel at all times, limit the access area and time of internal personnel, and politely refuse uninvited guests. At the same time, it will effectively protect your property from illegal infringement.
2. System design goals
1. Compact structure, economical and practical. Taking into account the professional technical level and maintenance ability of the operators and users of the access control system, the integrated system is the best.
2. There is a certain degree of advancement, which can meet the application in at least 5-10 years, and it is not out of date. Therefore, an access control system with a computer as the core is a more sensible choice.
3. The system has room for expansion. When the system needs to be increased or upgraded, it is not necessary to replace the entire system.
Three, one card function
Smart cards have a considerable capacity. Each smart card provided by our company can implement functions such as access, attendance, security, and work certificates on the same card, as follows:
Replace the key to enter and exit the house
Instead of parking card
Replace time card
Instead of access card
Replace membership card
4. The characteristics of the smart ID card system
1. Practicability: When using a non-contact ID card to open the door and read the card, there is no need to take the card out of the wallet or pocket, as long as it is read at any angle within the effective sensing range. When reading the card, the card reader will have a sound and indicator light to remind you that the card has been read.
2. Advance advancement: According to the specific requirements of access control management proposed by users, a set of computer intelligent access control system that can realize all-in-one card management is designed based on the principles of convenient use, comprehensive functions, safety and reliability, and strict management, so it adopts the most advanced and convenient Smart ID contactless technology.
3. Openness: The software supports WIN95, WIN98, WIN2000 or WIN NT4.0, supports various international standards for intelligent engineering, has compatibility and scalability, and can be integrated with other intelligent systems based on the WINDOWS platform.
4. Centralization: fully consider the inheritance and information sharing of the various subsystems involved in the entire intelligent system, and realize the distributed control and centralized monitoring and management of each subsystem.
5. Centralization: fully consider the inheritance and information sharing of the various subsystems involved in the entire intelligent system, and realize the distributed control and centralized monitoring and management of each subsystem.
ENCYC access control system design scheme
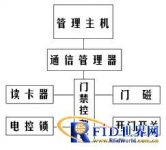
1. The composition of the access control system
The access control system is composed of controller, card reader, electric control lock, door sensor, door opening switch, identification card and communication manager, management host, management software, etc. The controller, card reader, electric lock, door sensor, door opening switch, and identification card constitute the basic access control unit equipment. The controller is the core of the access control system. It is composed of a corresponding peripheral circuit of a microprocessor. If the card reader is compared to the eyes of the system, and the electronic control lock is compared to the hands of the system, then the controller is the brain of the system, and it determines whether a certain card is a valid card registered in the system and whether the card conforms to it. Limited time period and door opening authority. So as to control whether the electric control lock is opened. The system composition diagram is as follows:

2. Types of Access Control System
Yingzhike access control system is divided into three types:
Independent type: The controller EDC-C10S is directly connected to the management host through the RS232 bus, which is suitable for simple systems with fewer doors.
Bus type: The controller EDC-C10B is networked through the RS485 bus and then connected by the communication manager and the management host. It is generally suitable for a small-scale local area network system.
MODEM type: The controller EDC-C10M connects with the management host through PSTN (Public Telephone Network), and is generally used for long-distance, large-scale systems.
3. Introduction to the features and functions of Yingzhike access control system
System features introduction
1. Intelligent communication bus: use RS-485 bus communication, or use MODEM to communicate via PSTN (Public Telephone Network). The system uses a polling method to monitor all information in real time. If a controller fails in the system, it will not affect the normal operation of the entire system, and the specific location of the failure can be indicated in the software. The important data on the communication line adopts dynamic rolling encryption technology, which has high security and confidentiality;
2. Good system scalability: RS-485 bus mode can realize local area networking within a range of 1200 meters, and each bus can connect up to 250 controllers and support up to 10 buses;
3. The system design is safe and reasonable:
▲ The controller can work offline, the controller will automatically store various historical records, and the privileged card can be used to set and delete the card when the controller works offline;
▲ The controller adopts an independent power supply. Even if the mains power is cut off (the power supply has an alarm prompt), it can still be powered by the backup power supply to ensure the normal operation of the controller. After the power is cut off, it can ensure that the saved information is not lost;
▲ The input of the controller adopts photoelectric isolation, and adopts internal and external dual watchdog circuit, which has strong stability and anti-interference ability;
▲ Each door has 5 inputs: door sensor, door open switch, infrared probe and 2 general inputs; 3 outputs: electric lock and 2 auxiliary outputs, users can connect various input and output devices according to their needs;
▲ Each controller can control two independent doors, with two independent card readers, exit buttons, and door lock interfaces. It can also be used in the case of single-door internal and external dual card readers;
▲ The controller uses Wiegand standard method to connect with the card reader, users can choose different grades and different manufacturers of card readers and proximity cards according to their specific needs;
▲ The software operation is convenient and simple: all Chinese interface, window mouse operation.
Introduction to the main functions of the system:
1. After reading the card through the personal identification card, the door can be opened only after being approved by the access control system;
2. All personnel enter and exit with the card, and the time, location and personnel of the card reading are automatically displayed and saved on the computer;
3. It can be opened and closed arbitrarily through the management host;
4. It is possible to delete or report the loss of an identification card or a batch of identification cards;
5. Through the system settings, some doors are artificially set to normally open or normally closed for emergency situations, etc.; when the door is normally open, the card reader system will still record all the cardholder’s information;
6. Each door can set 16 time zones for entry and exit;
7. Can flexibly set door opening permissions for designated doors and cards;
8. The system will alarm some abnormal doors in real time. After the card holder enters, if the door is not closed for a certain period of time (freely set), it will automatically alarm, and the computer will also automatically display and alarm;
9. The system monitors the entry and exit of all doors in real time;
10. You can set the operator’s authority level, and generate log files for all the operator’s operations;
11. The system can perform statistical inquiries on the operation status, alarm information, system operation status, and operator operation status of all doors and cards in any previous period of time, and can be previewed and printed;
12. It has the function of real-time alarm when the card is read without authorization and when the card is lost;
13. When the management software monitors, the alarm information is given priority. The control center can identify the alarm category, location and time of occurrence;
14. Door opening delay and alarm delay can be set arbitrarily;
15. If the door is opened in an abnormal state, an alarm will be triggered, and the alarm signal can be fed back to the control center or control remote access alarm equipment;
16. The system has the ability to adapt to abnormal situations. When the management host fails, the opening of the door will not be affected, and all the stored information will not be lost;
17. The unique system diagnosis function diagnoses the abnormal information of the system, and the system makes fixed points and timely alarms for equipment failures to facilitate timely maintenance and assist users to ensure the normal operation of the system;
18. Unique system monitoring window to ensure that users can still grasp system information at any time while running other programs;
19. Unique check and recovery function to help users ensure the integrity and consistency of controller data and management host data;
20. Unique privileged card function, when the management host is not working, you can still set and delete the card;
21. The system has several outputs and inputs to connect external alarm signals and some important equipment in the control room. The control center software has corresponding outputs and inputs to control the receiving platform;
22. Provide powerful print preview and printing functions, users can make various concise and beautiful reports according to their needs;
23. It is allowed to set the date limit attribute of the card, and automatically prompt after the limit date is exceeded to meet the user’s advanced management requirements.
[ad_2]