Campus access (passage) management system solutions
[ad_1]
Current status of campus management
1. Use gate channel with caution
The gate-type passage similar to the subway ticketing system is not very suitable for installation at the entrance of the campus, because there are several fatal problems.
The first is the injury to children. Although the gate channel has a variety of electronic and mechanical anti-pinch measures, there is still the possibility of trapping children, especially to children in kindergartens or lower grades of elementary school. .
Second, once the injury occurred at the school gate (in the case of Nanping, Fujian, it happened outside the school gate), the child could not enter the school quickly. Or once the injury occurs in the school, the children cannot be evacuated quickly.
The third is that the gate channel is generally not too high, it is easy to jump over, and it does not play a real role.
Fourth, the judgment of the gate-type passage depends on the obstruction of obstacles, and the ability to prevent trailing is relatively weak, and the possibility of getting in is relatively high.
2. The purpose of technical products is to accurately discover rather than control
The current technology products are still unable to automatically identify and automatically control suspects, and it is unrealistic to want to exclude suspects 100% from the campus. After all, equipment such as heightening courtyard walls and fingerprint recognition are not suitable. Used in school. Such efficiency is too low, time and application costs are too high, and it is easy to reduce the vigilance of managers.
Therefore, the first direction for selecting equipment should be accurate and rapid identification and rapid response.
3. The choice of actions after recognition is very critical
After the danger is identified, a comprehensive approach should be taken to eliminate the danger. Measures such as isolating the suspect from the child, intimidating the suspect, and calling for help immediately remotely will minimize the harm.
Suggested solution
A brief description of the working principle of campus access (channel): The four infrared probes on the channel are used to judge the direction of the people entering and leaving. At the same time, the card reader on the channel sends out a card reading signal to accept the card information carried on the body when the passing person enters. Computer software for identification. When a legal person passes, there is no abnormality in the channel. When an illegal person passes through and cannot be identified normally, the system will give an alarm and take a snapshot through the camera and display it on the computer in the administrator’s office in real time.
The campus access (passage) management system is coordinated and restricted by infrared detection, RFID technology, video surveillance, access control, alarm output, and video output to realize the humanized and intelligent access control. The logical design of infrared detection determines whether the channel system can accurately record the entry and exit status of each person. The selection of RFID determines the effect of long-distance card reading. The function that the channel system can achieve can be described as: the channel infrared detector can accurately obtain the number of people passing and the direction of movement, including accurate judgments of various complex situations (for example: 2 people coming oncoming, returning halfway and passing immediately, The clothing of the passer has the ability of infrared reflection, and the passer carries longer items, such as suitcases, bicycles passing, etc.). When a legal card passes, the entry and exit records can be used as the basis for attendance analysis and statistics, and can be set to video or capture. The purpose is to compare whether the cardholder’s appearance is consistent with the card registration, that is, to check the phenomenon of swiping the card on behalf of the card; when there is no card or an illegal card passes, video or capture and alarm. The history record includes a wealth of information: image screens, photos, directions of entry and exit, personal information, illegal information, location and time (accurate to the second) through the gate area.
In the entrance and exit control and the safety management of people, property, and property, safety and convenience are two opposite and contradictory concepts. There are bound to be inconveniences in places with high security levels, and barrier-free and fast identification channels are humanized design in security products. One of its products uses technology to bridge the contradiction between safety and convenience.
Security management design: The system can monitor and identify every person entering and exiting (including legal identities and cardless or illegal identities), and respond quickly. Legal identity entry and exit records (including images) are stored in the background database. At the same time, the entry and exit records of any period of time can be retrieved, and the entry and exit records of persons in sensitive time periods or all entry and exit records of sensitive persons can be screened in accordance with management regulations.
Humanized design: The original intention of the design of barrier-free fast-track is to carry out identity verification for entrances and exits with a very large flow of people (for example: campus campus, shuttle bus attendance, long-distance automobile ticket inspection, etc.). Its characteristic is that the identity check is fast and accurate, and the passer does not need to stay. Because in the process of identity verification, the main purpose of the system is to quickly and accurately screen illegal identities when most legal identities pass, so we have no reason to require most legal identities to sacrifice time to cooperate with the illegal identity verification, let alone because of this. Caused import and export congestion. Therefore, the design of barrier-free channels is very important. It is a common application method to quickly and accurately determine illegal identities and output alarm signals when people pass through barrier-free channels. Moreover, the system uses image comparison technology to record suspicious entry and exit during sensitive time periods. Personnel information is filtered. This is the organic combination of safety management and humanized management, and it is also an effective manifestation of the real intentions of managers.
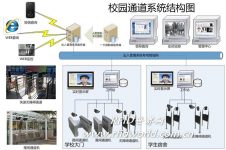
System structure and principle

Schematic diagram of structure
The system adopts distributed database management. All data exists in the central database and the local database at the same time. When there is data change (such as account opening, loss reporting, account cancellation, etc.), the data is automatically synchronized at each management workstation through the network.
When the network or server fails, it will not affect the operation of the channel control system.
If the network or server fails, all data will be automatically stored in the management workstation database, and automatically retransmitted when the failure recovers.
The data transmission adopts the CRC check method to check to ensure the correctness of the data transmission.
{$page$}
Main components of campus access (passage) management system
(1) Data server: store all personnel information files, entry and exit log, and capture images when passing.
(2) Card-issuing workstation: cardholder file management, cooperate with card reader to complete card issuance.
(3) Communication and monitoring workstations: complete channel machine entry and exit records and 24-hour monitoring tasks.
(4) Channel machine: real-time feedback of entry and exit records, and alarm when illegal persons enter and exit.
(5) Surveillance cameras: monitor and take pictures of people entering and exiting.
(6) Campus card: Use the campus card in the hand of the existing students to enter and exit the campus with the Shuai card.
functional module

System function module diagram
The personnel setting modules include: personnel information entry, batch card issuance, file editing, card issuance, card loss report, loss report cancellation, card replacement, personnel account cancellation, and personnel setting.
Data processing query modules include: manual supplementary recording, manual supplementary recording management, manual query, historical data access query, room real-time status query, room query, and room remote data query.
The item management modules include: item registration, item collection, uncollected items, received item query, and sending information to the big screen.
System setting modules include: client setting, video host setting, camera setting, department setting, room setting, authority setting, operator setting, large screen setting.
System function description
The main task of this system is to manage the entrance and exit of the campus building. The management modules include: personnel setting module, data processing query module, item management module, and system setting module. See below:

When the user passes, the user’s name, class information (content can be set), photos and basic information are displayed in real time
When the user does not have a card or is not authorized (such as expired or not in this system card), the system will automatically alarm and prompt, and can automatically take pictures and archives electronically.
To prevent following, one card can only pass one person
For two-way channels, the system can identify and display the user’s entry or exit
Different alarm sounds can be set separately for each channel
You can set the alarm for special users. If you need to remind a certain person that there is an important meeting, you can set it from the system. When the person passes by, the system will automatically prompt. The prompt method is voice or voice prompt.
For those who do not bring the card due to special circumstances, you can register to manually replenish the card.
If the management center cannot be connected due to a server or network failure, the operation of the system will not be affected, and the data will be automatically retransmitted after the failure is restored.
Each computer can manage four channels.
Main functional module design
The personnel setting modules include: personnel information entry, batch card issuance, file editing, card issuance, card loss report, loss report cancellation, card replacement, personnel account cancellation, and personnel setting.
1. Batch import personnel information function sub-modules:
Main function: Use existing database information to quickly import occupant information from EXCEL tables, and update new information in a timely manner.

2. File editing module:
Main function: It can edit the information of existing personnel, add, delete, change, search by department, dormitory, name, etc., determine personnel, and edit. The system supports two methods of manual entry and batch entry of electronic documents.
Card operations such as card registration, card replacement, loss reporting, account cancellation, etc. are supported. All quantity changes are broadcast to the network within one second, and all subsystems are automatically synchronized.
Support department adjustment of batch personnel through excel file
Comprehensive authority management allows the managers of each department to independently maintain the internal data of the department.
Quick personnel search: Support searching by department, campus, name, pinyin and various combinations, and support swiping inquiries.
Supports batch photo import in multiple ways.
{$page$}

3. The channel passes through the personnel setting sub-module:
Main function: Assign authority to legal personnel in this campus building, and add and delete authority to pass personnel in this building according to department, room or name.

4. Personnel card loss report submodule:
Main function: Report the loss of the card to the person whose card is lost or invalid. If the person who reports the loss does not have a new card to reissue, it will alarm when passing through the channel, and if the card is reported to pass through the channel for the second time, the system will also issue an alarm and take a camera capture.

Data processing query modules include: manual supplementary recording, manual supplementary recording management, manual query, historical data access query, room real-time status query, room query, and room remote data query.
5. Inquiry module of personnel entering and exiting:
Main function: for inquiries about personnel entering and exiting, there is an image comparison function for all inquiring personnel in abnormal time periods.

5. Manual supplement recording sub-module:
Main function: manual entry for students who have no card in and out or who are returning late at night,

6. Manual supplement recording management sub-module:
Main function: It can be inquired at any time, the input of the administrator and the data collection of the personnel who return late.

7. Room query sub-module:
Main function: Inquire about the situation of the whole building at any time. Keep abreast of students’ school conditions.

{$page$}
8. Remote bed checking sub-module:
Main function: Senior administrators can query each building in real time through the campus network. A school administrator with administrative authority can monitor the monitoring screen of any campus in real time while sitting in the office. On the remote monitoring terminal, operations such as video recording and photographing can be carried out. The historical monitoring records of any campus can be called remotely.

9. Campus night check-up management function: Teachers at night can check the home situation of students at night through the campus network, and can make remote inquiries to understand the night situation of student dormitories in real time.

The item management modules include: item registration, item collection, uncollected items, received item query, and sending information to the big screen.
10. Item registration:
Main function: Register and convey the parcels and letters of the staff in the building through the entrance of the campus.

11. Query function of unclaimed items:
Main function: for items that have not been picked up in time, you can inquire afterwards.

System setting modules include: client setting, video host setting, camera setting, department setting, room setting, authority setting, operator setting, large screen setting.
12. Department setting function:
Main function: It is mainly to enter the science department set up by the school, and set the department for the entry of later personnel. The department can be modified, added, and deleted.

13. Room setting function:
{$page$}
Main function: Add rooms on the actual floor.

14. Video Surveillance Center

You can record manually and automatically.
The automatic recording time can be set according to the week and time.
Using the world’s most advanced H.264 technology, under the premise of ensuring high-quality image effects, the campus gate measured only 1.6G per channel for 24 hours, and the 160G hard disk dual-channel video can be stored for more than 40 days.
Linked with the channel control system of the front desk, it can realize the normal and illegal passing photos of students.
Originally connected to the database in the background, the photo information of passers can be displayed at the same time when the video is played back.
When recording, the name of the person can be superimposed on the screen.
Problems with the channel management system
1. The implementation of any management system needs to be complied with by the management personnel, and the passage management system also has such problems as the initial management, such as the problems of entering and exiting personnel without cards or swiping cards. It is necessary to improve the corresponding management system and cultivate the card-swiping habit of personnel entering and exiting.
2. No software is successfully developed at one time. Different customers have different needs. To perfect the software requires further development, so as to perfect and reach maturity. The same is true for channel software, which has a high room for secondary development. This requires continuous communication between customers and us, step by step powerful software functions.
3. Training. Because the campus administrators are old and not professionals, they have certain difficulties in the management of the channel software, and we need further training.
4. If there is a campus power outage or network problem, when the channel is opened again, the anti-pass-in function needs to be turned off for two working days. Due to power outages, anti-pass-in and other reasons, there may be inaccurate statistics.
System test
(1) System test purpose
At each stage of software design, each link must be as early as possible to check out and eliminate as many errors and defects in the system as possible, and continuously improve and improve the quality and reliability of the software.
(2) Principles of system testing
1. Avoid the system developers from testing the programs they have developed, which will help overcome blind self-confidence and the continuity of misunderstandings about functions.
2. The design and selection of test cases, and the definition of expected results should be conducive to error detection.
3. Strictly implement the test plan and eliminate the arbitrariness of the test.
4. Reasonably conduct regression testing and verification to prevent the introduction of new and more serious errors in the troubleshooting process.
5. Properly save test cases, test plans, error statistics and final analysis reports to facilitate maintenance.
(3) Test method
1. Static analysis: Check and analyze the documents generated at each stage of requirements analysis, software design, and coding.
2. Dynamic test: Use the data set as input, actually run the program to check the behavior of the program, and confirm whether the program is correct according to whether the corresponding output meets the user’s expected result.
3. It can be used: a. Black box test method-functional test b. White box test method-structure test
[ad_2]



