Credit Suisse Technology Access Control System Solution
[ad_1]
The software comes with web Server, no need to install IIS and database, the B/S architecture can be achieved by installing the access control software provided by our company. The interface is simple and the operation is simple. The software includes access control functions and simple attendance functions;
1. Basic functions of the software:
1. Access management,
2. Time period authority management,
3. Real-time door status display,
4. Real-time record extraction,
5. Simple attendance management,
6. Open the door remotely,
7. Offline operation,
8. Access control data browsing,
9. Electronic map function,
2. Introduction of access control function:
1. Real-time monitoring and photo display: real-time monitoring of the card swiping situation, and display the photos stored in the computer by the card swiper for verification by the security guard.
2. Card + password function: If you use a card reader with a password keyboard, the system will have the card + password function. That is, the door can be set to require the user to input the correct password after swiping the card, and the door can be opened only after the card and password are correct. One card can have one password, that is, everyone has their own password. This function can prevent the card from being picked up to open the door, or stealing a colleague’s card to open the door to do things that shouldn’t be done, etc. For the same door, you can set some people to request a card + password, and some people can enter by simply swiping the card. The password can be 6 digits.
3. Access password function: that is, the user can open the door as long as the user enters a legal password, and the system does not record the event and the person who presses the password.
4. Illegal break-in alarm: that is, the door is not forcibly opened or broken in by legal means (swiping card, button, etc.), the system monitoring interface will prompt with a red signal and drive the computer speaker or alarm to sound.
5. The door has not been closed for a long time and alarm: the door is opened for a long time (how many seconds to open the alarm, this time can be customized) forget to close the door, the system software monitoring interface will prompt the time and location of the alarm information in red, and drive the computer The speaker reminds the staff on duty to pay attention. If the controller is connected to the alarm output and the fire linkage expansion board, it can also drive the alarm to sound on the spot to remind relevant personnel to close the door. This function needs to be equipped with a door sensor or an electric lock with a door sensor feedback signal output and connected to the controller. It can be set as the number of seconds to alarm or keep alarming until reset.
6. Duress alarm: When the staff is forced to open the door, the staff enters and enters the duress password on the password keyboard. When the door is opened, the staff will not be harmed by gangsters who become angry. The software interface of the general control center It has been shown that the location has been duressed to open the door, and the speaker will sound an alarm.
7. Illegal card swiping alarm: also called invalid card swiping alarm. That is, if someone tries to swipe the card with an unauthorized card, the system will give a red prompt alarm on the monitoring software interface and drive the computer speakers to remind the staff on duty to pay attention. If the controller is connected to the alarm output and the fire-fighting linkage expansion board, it can also drive the alarm to sound on the spot to deter people with bad intentions at the scene and remind the security to come.
8. Return back and anti-following function: If you enter the door without swiping your card, the system will not allow him to go out when you swipe your card. Or after someone swipes in and throws the card to others through the window, trying to let others in, the system will also refuse the swipe card to come in. Generally used in military, national defense scientific research and other occasions.
9. Interlocking: In some special occasions, it is required that the other door is not allowed to be carried out before the other door is closed. The double-door controller can realize the double-door interlocking. This function is mainly used in banks, savings houses, vaults, etc.
10. Open the door with multiple cards: that is, several people are required to be present at the same time, and the door will be opened by swiping the card one by one, and the door will not be opened if a person does not appear alone and swiping the card. Generally used in bank vaults, antique collection places, museums, etc.
11. Regular door opening/closing function: also called timing task function. For example, the office lobby of the Civil Affairs Bureau, embassy, etc., require the door to be opened during the daytime, and people who come to work outside can come and go freely. After get off work at night, personnel from the unit are required to swipe their cards to allow entry and exit. Outsiders are not allowed to enter. The door remains closed at night. Status, internal employees of this unit are not allowed to enter and exit.
12. Record button door opening event: You can record when the button was pressed to open the door. Although you can’t record who pressed it, you can know when the button was pressed, and when the last person left last night.
13. Electronic map: The icon of the door can be placed in a certain position of the corresponding map, and the display is more intuitive and user-friendly during real-time monitoring.
14. The remote door opening manager can open a door remotely by clicking the “remote door opening” button on the software interface after receiving the instruction. Remote door opening records can also be recorded through settings.
15. Flexible authority management: You can set which doors a person can pass, or a person can pass all the doors. It is also possible to set which doors certain people can pass through. The setting results can be arranged by door or by person, and the user can clearly see who can pass through a certain door, or which door a certain person can pass through. It is clear at a glance, and can be printed or output to an Excel report.
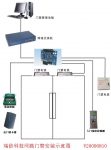
Three main components of the system:
1 computer
2 Network switch
3 Access controller
4 Electric mortise lock
5 Fingerprint reader controller
6 ID card reader
7 Emergency button
8 Access control power box

[ad_2]



