Jiesda: Network Time Attendance Management System Engineering Design Plan
[ad_1]
(I. Introduction
The advanced information management system is an important sign for the establishment of modern management, and the popularization and application of smart IC cards is an important means to promote and improve information management.
At present, the internal complicated transactional management of enterprises and institutions, such as employee identification, attendance, canteen sales, internal channel management, and internal shopping, consumption, entertainment charging management of enterprises and institutions, internal and external vehicle management, internal patrol monitoring management, etc. Staying at the elementary level of manual operation, not only the repetitive workload is large and the management difficulty is high, but the comprehensive management cost is also high, which makes certain loopholes in management more and more enlarged. If the smart (IC) card “all-in-one card” management system is enabled, comprehensive applications such as employee identification, attendance, dining, access control, parking, entertainment, shopping and consumption will be integrated on the smart IC card, so that one IC card is responsible for the certificate and internal Various functions such as consumer currency, access control, conference registration, etc., on the one hand, can reduce management procedures and reduce management costs, on the other hand, it strengthens the orderly and effective monitoring and management of people, finances, and logistics, and improves the sharing and utilization of limited resources. Rate, the management of enterprises and institutions has risen to information management.
(2) Design principles and goals
1 Design principles
1.1 Practical flexibility
We have accumulated many years of industry experience after extensive market research. Based on the comprehensive consideration of the diversity of user needs, the ease of operation, and the practicability of the system, the entire system runs through a variety of parameter settings, and can customize projects and settings. The free combination of report format and related query conditions can be adapted to the requirements of specific users.
1.2 Accuracy
In the process of designing the entire system, we strictly adopt software engineering methods to ensure the quality of the products by step by step in terms of requirements analysis, selection of development tools, code writing, test maintenance, etc.
1.3 Safety and reliability
The system is equipped with a special authority system and password system to strictly control the scope of responsibility of each operator. Each operator can only operate the functional modules and departments for which he has authority. It can even be set that some operators only have the authority to inquire about a certain department, while other operators have the authority to modify and delete related information of a certain department. In short, the operations of each operator to the departments and functions of each system can be assigned very meticulously according to needs. The system is equipped with a detailed operation log, which is convenient for the system administrator to keep abreast of the use of the entire system.
1.4 Universal ductility
Because we consider that some users sometimes do not adopt the entire system at once, but implement it in phases. When we design, we have ensured that our system can be arbitrarily combined. Therefore, whenever a user needs to add a system or module, it will not affect the system data and require no additional work. In addition, considering the scalability of the system, the cross-platform use of the system and the diversity of the database, we have made careful selections in the design of the database structure, the selection of the development tool language and the system structure to ensure the versatility of the product , Scalability.
2 Design goals
The project plan is based on meeting the basic needs of users as the starting point. According to the detailed needs analysis of specific customers, we will configure a complete solution.
3 Means of realization
3.1 Development tools
It adopts the world-famous software tool developer Borland’s object-oriented Delphi 5.0, which has a multi-layer structure and close integration of e-commerce.
3.2 Operating System
The most widely used Windows NT or Windows 2000 is adopted as the server to ensure convenient and practical management.
3.3 Database
SQL SERVER: It is a medium-sized relational database management system produced by Microsoft. It has the following characteristics:
1. Client/server architecture
2. The graphical user interface makes the management of the system more intuitive and simple.
3. Abundant programming interfaces provide users with greater choice for application design.
4. Organic integration with Windows NT operating system and multi-threaded architecture design improve the speed of concurrent access by the system to users.
5. The support for Web technology enables users to easily publish the data in the database to the Internet.
6. The price advantage. Compared with other large database systems such as Oracle and Sybase, the price of Microsoft SQL Server is very cheap.
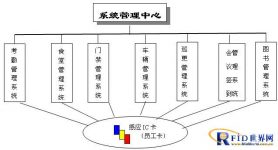
(3) System composition
The “One Card” system consists of a system management center, an attendance management subsystem, a canteen management subsystem, an access control management subsystem, a patrol management subsystem, and a library management subsystem.
The system structure diagram is as follows:

Figure 1 System structure diagram
(1) System Management Center
The management center is mainly responsible for the summary, statistics, and analysis of the entire system information, as well as the issuance, recharge, loss reporting, deletion, and query of inductive smart IC cards; it can also be connected with the financial management system of enterprises and institutions to provide relevant financial management data.
System network structure:

(2) Attendance information management subsystem
The structure diagram of the network version attendance management system is as follows:

2. Equipment configuration:
a) Computer, printer, UPS;
b) Attendance management system software;
c) Inductive attendance machine: stand-alone 4MB capacity, 15,000 attendance records, and the data will be stored for 100 years after power failure;
d) Inductive IC card: Mifare chip, 8K capacity, 16 cells and 64 read-write units.
3. Attendance management system functions:
A special attendance system for employees can be set. (Overtime is in units of half an hour, in actual units, and in whole hours).
An infinite number of different working time groups can be set according to the needs of the attendance system. And it can set the valid clock-in time and allow late and early leave time for it. Each group of employees can schedule shifts by date, and there can be countless kinds of commuting schedules each day, and each schedule can have up to four commuting hours per day, and each period of time can be set for half-way breaks and whether to work overtime (this is overtime) In order to work overtime regularly, the off-duty card is not required to be issued after get off work, and the off-duty card is not issued until the end of overtime get off work).
It has the function of signing cards for employees on business trips.
According to the above settings, the program automatically processes and analyzes the employee’s commuting time, late arrival, early leaving, various overtime, various leave (leave category, leave category, business trip) situation, so as to generate a series of various status of attendance daily reports, Monthly report, quarterly report, annual report, attendance summary report for any period of time, abnormal summary report, etc.;
You can customize the query conditions for compound query, and generate various query reports that meet the conditions.
The authority system can set all the functions of the system, and set the systems and functions that can be operated by different operators. Each operator can only perform his duties within the function authority allowed by him.
All data can be interacted with Microsoft Excel.
(4) System characteristics
1. Convenience and speed
Thanks to the inductive IC card, the reader can operate the card within 5cm without inserting or removing the card. At the same time, the inductive IC card is non-directional for reading and writing. The card can be swept across the surface of the reader in any direction. The completion of the card reading operation greatly improves the speed of each punching in (only 0.1 second).
2. Safety and stability
Each IC card uses a dedicated reader to set read and write permissions and accurately record data, so as to prevent forgery and counterfeiting, and the read-write terminal will not affect normal operation due to changes in the environment. Reflects the accurate and effective management of the resources of “people, finances and materials” by the enterprise, and guarantees the safety, reliability and consistency of the system and technology.
3. Flexibility
Since the “one card” management system has the independence of front-end functional response and the compatibility of other related business functional management systems, it can be used alone, but also supports the network environment, and can be implemented under any network structure. So as to facilitate the expansion and full utilization of the system.
4. One card with multiple functions
A card can not only be used as the identification of faculty and staff, such as work permits, student cards, and entrance passes, but also can store a large amount of data (including personal information) for easy query, and it also has the function of “electronic wallet”. Employees and students can use the card You can go to canteens, OK entertainment venues, canteens, etc. for consumption.
5. Management automation
In the “all-in-one card” management system, a computer network is used to conduct unified and standardized management of all internal data, and related data settings are shared, which can greatly reduce workload, save comprehensive management costs, and improve work efficiency.
(5) System security mechanism
1. The security of IC card
1) Unique card number: The serial number of the induction IC card is unique, and it has been solidified in the chip and cannot be changed.
2) Communication encryption: the communication between the card and the reader adopts the three-time mutual inductance verification technology that meets the ISO9798 international standard to verify the legitimacy of the card and the reader device, that is, the reader needs to verify For the legitimacy of the IC card, the IC card must also verify the legitimacy of the reader; in the communication process of three mutual authentications, all data is encrypted to ensure that it is not illegally modified.
3) Authorized card opening: The authorization method is adopted for reading and writing control, that is, an authorized “initial card” can be used to read and write the IC card of this system on a dedicated card writer. Therefore, there is no password cracking in this authorization method. As long as the “initialization card” is not stolen, the absolute security of the system can be guaranteed.
2. The safety of reading and writing equipment
1) The data of all reading and writing devices (attendance machines, toll machines, access control machines) are stored in the FLASH chip, which is protected against power failure and will never be lost.
2) The various parameters of the read-write equipment can be changed and operated only through the “system management card”.
3) If the management computer fails and causes data loss, reset the FLASH chip pointer from the read-write device and collect the data again (when the FLASH chip storage is not full before it is emptied).
4) Each consumption record has a consumption serial number, and records the current card read and write operation serial number to ensure the security of each transaction.
5) Set the maximum consumption limit on the toll collection machine. When the limit is exceeded, the alarm will be “beep and beep”.
3. The security of network communication
In the communication of the “all-in-one card” management system, all consumption points, attendance points, and gate control points have dedicated all-in-one card network ports to ensure that data is not intercepted during communication.
Shenzhen Jiesda Technology Development Co., Ltd.
Contact: Yao Zhengrong
Telephone: 83765948
Fax: 83763869
Mobile phone: 13923719498
E-mail:[email protected]
[ad_2]