RFID application scheme in campus information construction
[ad_1]
1 RFID information model
1.1 Overview of RFID
RFID (Radio Frequency Identification) radio frequency identification is a non-contact automatic identification technology, which automatically recognizes the target object and obtains related data through radio frequency signals. The identification work does not require manual intervention and can work in various harsh environments.
1.2 Data structure of RFID
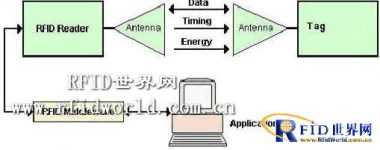
A complete and typical RFID system usually consists of 4 modules: tag (Tag), reader (Reader), RFID middleware, application program (Figure 1).

Figure 1 RFID system
1.2.1 Label
The tag is composed of an antenna and a chip. The antenna transmits radio frequency signals between the tag and the reader. The chip stores the unique electronic code and user data of each tag. Each tag has a globally unique ID number – UID, UID is placed in the ROM when the chip is made, and cannot be modified; the user data area is for users to store data, which can be read, written, overwritten, and added operate.
1.2.2 Card Reader
The card reader is a device that reads (or writes) tag information and can be designed as a handheld or fixed type. The operation of the card reader on the label has 3 types: 1) Identify: read UID; 2) Read: read user data; 3) Write: write user data.
1.2.3 RFID middleware
RFID middleware is the glue that combines the underlying RFID hardware with the upper-level enterprise applications. Although in principle the middleware is a horizontal software technology, in the RFID system, in order to make it more suitable for specific industries, RFID middleware will do certain adaptation work for the industry.
In the specific case of the RFID system, the middleware layer has the following specific functions in addition to the usual functions: reading/writing is more reliable; pushing or pulling data to the correct location through the card reader network (similar to a router); monitoring And control the card reader; provide safe read/write operations; reduce radio frequency interference; handle tag-type and reader-type events; application notifications; accept and forward interrupt instructions from applications; provide users with exception warnings[2].
1.3 RFID related standards
At present, RFID has not formed a unified global standard, and the market is a situation where multiple standards coexist. However, with the beginning of the large-scale application of RFID in the global logistics industry, the unification of RFID standards has been widely recognized by the industry.
The core of the RFID standard contention is mainly in the field of RFID tag data content coding standards. At present, five major standards organizations have been formed, representing the interests of different groups or countries in the world. EPCGlobal was jointly established by the North American UCC Product Uniform Coding Organization and the European EAN Product Standard Organization. It has hundreds of members around the world and is supported by retail giants Wal-Mart, manufacturing giants Johnson & Johnson, Procter & Gamble and other multinational companies. ISO represents European and American countries and Japan; IP2X members are mainly in Africa, Oceania, Asia and other countries. In comparison, EPCGlobal has the upper hand because of its integration of American and European manufacturers.
1) EPCGlobal standard.
In addition to issuing industry standards, EPCGlobal is also responsible for EPCGlobal number registration management. EPCGlobal system is a system based on EAN·UCC code. As a coded representation of product and service circulation process information, the EAN·UCC code has a set of globally unique identification codes that cover various tangible or intangible products in the trade circulation process, including trade items, logistics units, locations, and assets. , Service relationship and other identification codes. The EAN·UCC identification code is established at the source of circulation as the product or service is produced, and is accompanied by the flow of the product or service throughout the entire process. EAN·UCC identification code is a fixed structure, meaningless, and the only all-digital code in the world. In the EPC label information specification 1.1, the 64296-bit electronic product code is used, and the 962256-bit electronic product code is used in the EPC label 2.0 specification.
2) ISO standards.
The International Organization for Standardization (ISO) has also developed a series of standards for RFID automatic identification and item management. For example, ISO created a standard for using RFID to track cattle. ISO11784 defines how to organize the data structure of tags, and ISO11785 defines the air interface protocol. The International Organization for Standardization has also drafted and established air interface standards (ISO14443 and ISO15693) for RFID tags in the fields of payment systems, contactless smart cards and contact cards, and established standards for testing the compatibility of RFID tags and card readers (ISO18047) and tests. Standards for the performance of RFID tags and readers (ISO18046).
1.4 RFID technology and identity authentication technology
At present, barcodes, magnetic cards, and IC cards are widely used, but the barcodes use the user name/password authentication method for identity authentication, which has fundamental security risks, and is inconvenient to carry and use. Magnetic cards and IC cards use It is the identity authentication of the IC card authentication method, and it can only be used under a specific system, and its versatility is not high. The emergence of RFID has solved this kind of problem well. RFID uses radio frequency to carry out non-contact two-way communication, so as to realize the identification of objects, and remotely transmit the collected information and data through wireless technology.
Compared with the currently widely used barcodes, magnetic cards and IC cards, RFID has a long reading distance (several meters to tens of meters), strong penetrating ability, anti-pollution, and high efficiency (multiple tags can be processed at the same time), It has the characteristics of large amount of information, easy to use, and low cost. Generally speaking, it can be summarized as having the two major characteristics of ease of use and versatility.
2 RFID application scheme in the informatization of Xiaogan University
2.1 The overall model of RFID application scheme
The campus network infrastructure of Xiaogan College began in 1997 and has developed to a certain scale. The core switch is Huawei S8505 10 Gigabit core routing switch, 100M is connected to China Telecom, 2M is connected to the education and research network, and the firewall is Cisco AS5550. The number of Internet access points is more than 4000, the database server is Sugon R4280, and the storage is Inspur AS330. The data center is under construction. The whole school uses the online version of Trend Antivirus software.
According to the overall planning goal of the information system, combined with the actual situation of Xiaogan College, the overall model of the RFID application scheme is shown in Table 1.
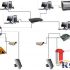
Figure 2 shows the overall deployment of the system architecture of the RFID application solution. In this scheme, a card can be used in the whole school, which is convenient and reliable. All data is kept in the data center. The data center is directly connected to the bank, and other departments are not connected to the bank. Students and teachers can use the card to eat, go to the doctor, shop, entertain, and board the computer, etc. The Academic Affairs Office can also accurately understand the student’s information and whereabouts.

Figure 2 Schematic diagram of RFID application scheme in the informatization of Xiaogan College
2.2 Organizational Guarantee
The informationization leading group of Xiaogan College is responsible for the overall responsibility, and the dean of the college is the group leader. The main responsibility is to strengthen the leadership of the school’s informatization construction, supervise and inspect the implementation of the national informatization construction guidelines and policies in the school; review the school’s informatization construction Long-term development plan, etc.
The main responsibilities of the informatization construction expert group of Xiaogan College are: responsible for reviewing the school and various departmental information project construction plans and implementation plans; responsible for providing guidance and consultation on the technical issues of the school information construction project; reviewing and implementing the school information construction project Project establishment, inspection, acceptance and evaluation; to provide counsel and consultation for the decision-making of the school’s information construction leading group.
The laws, regulations and school system are as follows: “Regulations on the Security Protection of Computer Information Systems of the People’s Republic of China”; “Administrative Measures on Information Security of Xiaogan College Campus Network”; “Administrative Regulations on Xiaogan College All-in-One Card”; “Xiaogan College All-in-One Card Use Responsibility Letter”.
2.3 Personnel management
The school has established an information office, which is linked to the network center. Its main responsibilities are: drafting the school’s information construction plan and implementation plan; responsible for formulating the school’s relevant information construction management rules and regulations; implementing project management for the school’s information construction work; responsible for school information The construction and management of the management system; organize different forms of information technology training to continuously improve the level of information application skills of the school’s teachers and students; carry out education information construction research; complete the daily management of the school information construction leading group, etc.
2.4 Information Management
In this application scheme, the data center is also very important, including data security, storage, backup, analysis, and so on.
2.4.1 Database model
Centralized database and distributed database are mainly considered in the selection of database distribution plan. Using a centralized database, all data are stored on the central database server, which is conducive to data maintenance and consistency. But once the central database fails, the entire system will be paralyzed. With a distributed database, the data will be scattered on each database server. The advantage is that if one or several servers fail, the system can still continue to run, but it takes a certain price to keep the data in each sub-database consistent with the central database. It is suitable for database systems with extremely high requirements for real-time, stability and database performance. Because the campus card system is mainly distributed in the campus, and the deduction of the amount is done on RFID, the main function of the back-end database is to store information and query, and the real-time requirements are relatively low. The centralized database can already meet the data processing requirements.
Data loss can be caused by many factors. Misoperation, disk and other equipment problems, etc., may cause data loss. Therefore, data backup should be the basic service provided by the data center. From the point of view of the data center, not only the fast backup and recovery of data must be considered, but also the backup and recovery measures must be provided to deal with disasters. The so-called disaster refers to the loss of data due to earthquakes, fires, and hardware damage. In order to prevent this situation, the data center will establish a data backup center, which will be stored off-site. If an accident occurs and a data center node cannot work normally, data can be obtained from the data backup center so that the entire system can still be used. Provide services to the outside world.
There are many ways of data backup, which are basically related to the requirements of recovery.The data backup technology used in data centers is currently basically NAS (Additional Network Storage) technology and SAN (Storage Area Network) technology.[3]There are limitations. The latter is a relatively advanced technology with high cost, which can better realize storage equipment sharing and expandability. The storage format of the data is shown in Table 2.

2.4.2 Card authorization management
At present, the personnel data of Xiaogan College comes from the two departments of the Personnel Office and the Academic Affairs Office, which manage the data of faculty and students respectively. The center will submit it to the bank after approval. When the bank completes the card opening, the bank returns the account opening information and blacklist to the card management center, and then synchronizes the corresponding information to each application system according to the needs of each application system. Individual users can check all their personal information through the Internet, including consumption status, deposit status, and passing status.
2.4.3 Data access authorization management
The permissions of various types of personnel are as follows:
1) The management personnel of the data center have super user permissions and can see all the data. The selection of personnel is required to be managers with high political and professional qualities.
2) The dean and secretary of the college have the authority to view all data, but they do not have the authority to modify or delete data, but they can assign the administrator of the data center to modify it.
3) The person in charge of the financial department has the authority to view all consumption, deposits, and economic totals.
4) The person in charge of the Academic Affairs Office has the authority to view all personnel information, including teachers and students.
5) The person in charge of the personnel department has the authority to view all teacher information.
6) The person in charge of the academic department has the authority to view all student information.
7) The management personnel of the secret-related archives room have the special authority of the secret-related archives room.
8) Teachers and students of drug-related laboratories have special permissions for drug-related laboratories.
9) Other personnel only have the authority to view their own information.
2.5 Security Management
2.5.1 System security
The system has security, including network system, host system, data access system, data transmission system security, data backup and disaster recovery reliability. In order to ensure the safety of system software, application software and data, the system strictly selects operating system platforms and development platforms, designs anti-virus functions, protects system data, and establishes a backup system to automatically perform full and incremental backups on a regular basis. In the system, the radio frequency card is used as identification, and encryption is used in the processing and transmission of key information to prevent unauthorized access to the information and ensure the non-attackability of the system.
The platform of this application scheme is: WIN2000; the database is SQLSERVER2000 large-scale database; the server is WIN2000SERVER.
2.5.2 Reliability of network operation
Reliability includes the reliability of network operation, the reliability of hardware equipment, the reliability of running software, and the addition of power failure protection, data backup and other means to the system to ensure the normal and long-term operation of the system.
This application scheme uses a network architecture that combines real-time and non-real-time. The system management center has a central database, and each subsystem has a local library. Each local library and the center realize data exchange through the campus network, so that each application subsystem depends on the campus network. It can also be operated separately from the campus network, which increases the safety and reliability of operation. Consumer terminals have their own batteries, which can work in the event of a power failure. Consumer terminals also have a storage function that can save certain consumption records. 9) Other personnel only have the authority to view their own information.
3 Summary and outlook
In the construction of digital campus informatization, the convenience and versatility of users and management, and the security issues with identity authentication as the core are two major difficulties, and they are also the key to the success or failure of the application scheme. This application scheme has detailed design in 6 aspects, including overall planning, overall deployment, organizational guarantee, personnel management, information management, and security management. In terms of data analysis, statistics and program evaluation, this application program has a positive effect on the school’s information construction and student management, and it is worthy of promotion.
This application scheme uses student ID/teacher ID as the only identity authentication, which is convenient to carry, all-in-one card use, convenient to use, and conforms to the principles of ease of use and versatility. The use of this application system facilitates the study, life and management of teachers and students, improves the efficiency of work and study, and conforms to the principle of high efficiency. This application system considers three aspects of physical security, network security, and information security to ensure the security of the system.
[ad_2]