RFID barrier-free automatic induction access control statistics management
[ad_1]
Due to the development of digital technology and microelectronics technology, RFID access control systems have long surpassed the traditional doorway and key management functions. The safety requirements of the modern working environment, departmental administrative management, daily attendance management, company catering consumption, etc., are all closely related to the access control system. Departments such as apartments, residential quarters, factory patrols, company R&D technical departments, medical units’ non-disturbance areas, finance and finance are all ideal places for the application of RFID access control systems.
How to control the people entering and leaving the door more quickly and accurately, and automatically record the information of people entering and leaving without missing the record, is a higher-level problem that needs to be solved urgently for automatic access control and automatic attendance today.
At the same time, it is also required to reflect the humanization and intelligence of technology. The smart card worn by personnel can be carried arbitrarily, which does not give people a sense of control. At the same time, it is convenient to use. Attendance. The installation of the card reader antenna should not cause visual damage or obstruction to the original building, and maintain the overall delicacy and beauty of the building.
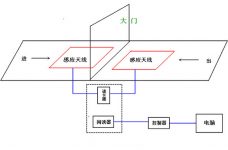
The remote automatic induction identification and personnel entry and exit identification management system designed by our company can fundamentally solve this problem, reduce labor management costs, and improve management efficiency. The system consists of an access controller, a long-distance card reader, an induction antenna, an induction card, a computer network, a database, etc.

1. Scheme design
Points to note in the remote automatic access control attendance management system: The card reading distance is required to be 1-2 meters away from the door, and 0.5 meters on the left and right (carry the card can be placed in the pocket or purse at will), and people come from a distance Just walk to a position about 1-2 meters in front of the door and read the card. When the door is unlocked, the person pushes the door in. The time is just right. There is no need to stay in front of the door. A series of actions are completed continuously.
1. The induction card carried by the employee can be carried anywhere, and the card can be placed in the employee’s pocket, bag or hung in front of the employee as an identification card.
2. The sensing range of the card is stable, and the card is read in a fixed area, and it cannot be far or near. The sensing distance cannot be too far or too close. If the distance is too far, an employee will produce a wrong record when passing by the passage, and if the distance is too close, the passage will not be sensed.
3. In order to reflect human care, the card cannot be directional and can be placed arbitrarily, and employees must not be required to place the card in order to identify it.
4. The system must have multiple identification and anti-conflict capabilities. There are a lot of people entering and leaving at the same time during the peak hours of staff commuting. The system must ensure that all cards can be accurately identified at a high speed.
5. The system must accurately determine the direction of entry and exit of personnel, and can not just record incidents to prevent false entry and exit.
6. The number of records generated by the system should not be too many. One entry and exit can only generate one record at most. If dozens of records are generated for one entry and exit, and the number of people is large, the number of cumbersome records generated every day will seriously affect the use of the system. When counting attendance, it will cause the statistics to be unavailable for a long time.
7. The radio frequency signal generated by the card reader and proximity card must be harmless to the human body, because employees spend most of their time within the signal range, and the safety of everyone should not be forsaken for the convenience of management.
8. The card must be an active card, high and low frequency are combined with each other. Passive cards will be shielded by the human body and by ordinary objects. When many people are crowded together to enter and exit, the card leakage is serious.
9. The card must work passively, not in a dormant state within the sensing range, not working, and not actively sending signals to prevent any tiny radiation signals. Actively sending signal 1 can easily cause high battery power consumption. 2. Easy to cause cumbersome records
10. The product must be used in a large number of personnel identification projects, and a stable operation system for more than 5 years as a reference basis.
Second, the implementation of the program
1. The active high and low frequency hybrid proximity card and low frequency card reader used in this system design are truly fast, accurate, and long-distance induction radio frequency identification products. The card reading distance can reach hundreds of meters, and the coverage channel width can reach several At ten meters, it can recognize up to 500 induction cards at the same time, and the card reading speed can reach 200 km/h, so it can accurately identify and track fast-moving objects or people from a long distance.
2. The working mechanism of Chuangzhan long-distance active induction products is: each induction card has a 64-bit code, when the induction card is present in the reading range of the reader, the induction card is continuously emitted by the reader The electromagnetic inquiry signal is activated, and a response signal carrying the proximity card number is fed back to the reader. It is through the interrogation and response of the proximity card and the reader that the reader can accurately and quickly identify The number carried in the proximity card, and the read proximity card number is output to a computer, external controller or other terminal equipment in a certain output format, so as to realize the remote identification of the proximity card.
3. The management center distributes an RFID proximity card with a 64-bit code to each person, and installs an RFID low-frequency long-distance card reader at the gate. When the person carrying the card arrives at the passage, the card reader can sense the card. And the information in the card (card number) is transmitted back to the card, and the card transmits the signal wirelessly to the reader. The reader transmits the signal to the control device through wire. The controller judges the legality of the card information and generates corresponding control actions. Pass the received proximity card number to the management software to automatically determine and identify the entry and exit records and directions. The managers can monitor and manage the entry and exit of each channel in real time, and record the front and back positions of the personnel.
4. Extended application: The system can also be equipped with access control functions at various positions. An electric lock is installed on the door as an executive part of the access control system. The access control controller determines whether to open the door lock by judging the permission of the proximity card; magnetic lock or electric The mortise lock adopts the power-off door opening type, which meets the fire protection requirements, and all the fire door locks are automatically opened when a fire occurs. The blocking facility (such as the door) opens when the card is read, effectively preventing unauthorized persons from entering a specific area. For visitors and outsiders contacting the business, the management is carried out by issuing temporary cards. Outsiders visiting need to register on the visitor machine at the designated location of the management department. The registration staff will ask the visitors to go to the floor and department, and confirm by telephone contact. After that, issue the induction card with the corresponding authority and print the visitor slip. The visitor can enter and leave the designated floor or department with the authorization card in his hand, and cannot enter or leave other floors or departments, which not only guarantees safety management, but also does not hinder normal work communication. When leaving, return the card and the visitor list signed by the interviewer; through the hierarchical authority management of the proximity card, the effective management of the safety of the entire unit is realized.
To further ensure safety, video surveillance cameras can be linked as one of the auxiliary means of access control management.
5. The CTV series of long-distance active cards used in the system can be used for long-distance recognition or short-distance recognition. Combined with a low-frequency active card reader with a reading distance of 1-5 meters, it can realize access control, attendance, and consumption. , Visitors, elevators, vehicles, patrol management and other all-in-one card functions, long-distance card reader output with standard WG34/26 interface, can be connected to any access control attendance card manufacturer’s system. In addition, the remote sensing active card also has the characteristics of non-copying, safety and reliability, long life, and reuse. The non-contact card reading method reduces the mechanical wear of the card to zero. The issued proximity card can be printed with a photo as a work permit.
RFID access control system, as one of the facilities with relatively complete security performance, is playing an increasingly active role. From ordinary read-only access control cards to logical encryption authentication access control cards, their security performance has been qualitatively different. The read-only access control card adopts one-way communication mode, and now most of them are only used in some common occasions. The long-distance active logic encryption access control card adopts two-way encrypted communication, and its security is greatly improved. Take NXP’s Mifare access control card as an example. Its security authentication is completed by verifying the independent KeyA and KeyB of each sector. Through the different combinations of the sector control word to KeyA and KeyB, the safety control of the reading and writing of sector data is realized. Since the key is a relatively fixed password set in advance, and one card has one password, or one card with multiple passwords, the protected data in the card can be read and written only after passing multiple key detection and authentication. operate. Restricted by the verification mechanism of KeyA and KeyB, although the terminal device can solve the authentication of the logic encryption card to its terminal device, it cannot solve the authentication of the logic encryption card by the terminal device itself.
[ad_2]



