Shenzhen rental house access control management plan
[ad_1]
Chapter 1 System Introduction
1.1 Background
In order to meet the requirements of the grassroots and actual combat of public security information construction services, innovate the management model of rental houses and mobile personnel, strengthen the comprehensive management level of social security, and improve the ability of public security to prevent and control. Shenzhen rental housing video access alarm system with functions such as video surveillance and alarm. For details, please refer to “Shenzhen Rental House Video Access Control and Alarm System Technical Specifications” (hereinafter referred to as “Specifications”).
1.2 System construction goals
Combined with the construction of the second and third categories of Shenzhen’s electronic prevention and control project, standardize the construction of Shenzhen rental house video access control alarm system, maximize the use of relevant information resources, give full play to the role of system security and technology prevention, and maintain Shenzhen’s social security and stability. Provide a strong security guarantee for the sustainable and healthy development of Shenzhen’s economy.
The video access control alarm system for rental houses in Shenzhen should organically combine the access control system, video monitoring system and alarm system to achieve alarm linkage. At the same time, through the system, the information of personnel passing through the entrance and exit of the rental house shall be collected and back-stage comparison, for the public security organs to investigate Provide technical support for solving cases, combating prevention, public security management, etc.
1.3 System standards and principles
The video access control alarm system for rental houses in Shenzhen adopts an open architecture, selects standardized interfaces and protocols, and has good compatibility and scalability. It complies with relevant national and industry standards and regulations, and complies with the Ministry of Public Security’s “On the Development of Urban Alarm and Monitoring Technology” “Opinions on System Construction”, “Technical Guidelines for the Construction of Urban Alarm and Monitoring System”, “Implementation Plan for the “3111” Pilot Project of Urban Alarm and Monitoring System Construction”, “Guidelines for the Construction of Social Security Video Surveillance System in Guangdong Province” by the Department of Public Security of Guangdong Province, Technical Specification for Data Transmission of Social Security Video Surveillance System in Guangdong Province.
Chapter 2 Program Introduction
2.1 System introduction
Shenzhen is a modern city with a developed economy, advanced technology, and a large population. More than 90% of the population are migrants. This part of the population has the characteristics of high mobility, scattered living locations, different cultural qualities and living standards, and high management difficulties. . Therefore, it is very difficult to adopt ordinary management methods, requiring a large number of security personnel to conduct 24-hour patrols. The management cost is very high, not only time-consuming and laborious, but also due to the existence of management blind spots, which frequently leads to vicious criminal cases such as burglary and robbery. The personal and property safety of personnel cannot be guaranteed.
In order to create a safe living environment for renters, while saving management costs, improving management efficiency and eliminating management blind spots, this program is specially designed and adopted the most stable, reliable and safest UISYS access control management system.
The UISYS access control management system adopts a distributed application and centralized management model. It has the characteristics of flexible system architecture, high safety performance, high cost performance, powerful system functions, easy operation, graphical management, and good scalability. The system also adopts a three-level structure of hardware equipment + server platform software + management workstation and TCP/IP network communication, which realizes the coexistence of multiple servers and multiple workstations and cross-regional management, which meets the requirements of relevant departments in Shenzhen for renting houses and renting personnel. Distributed application and centralized management are required to achieve the purpose of humanized and scientific management.
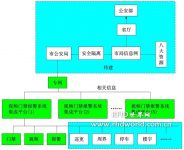
2.2 System structure
The system adopts the management mode of “hardware equipment + server platform software + workstation”. Each management office can configure equipment workstations, street office workstations, lease office workstations, owner workstations, mobile phone workstations, monitoring workstations, patrol workstations, and linkage workstations according to management functions. .
2.2.1 Overall structure

2.2.2 Access control system structure
2.2.2.1 Access control system structure of rental house

2.2.3 Platform software structure diagram

2.2.4 Workstation module diagram

Chapter 3 System Function and Composition
3.1 System function
UISYS access control management system adopts TCP/IP network communication mode, coexistence of multiple server workstations, multiple alarm methods, graphical management methods, multiple linkage methods, multiple report queries and other designs to achieve intuitive, convenient and fast management requirements.
The TCP/IP communication mode ensures that the communication between the front-end equipment and the system management platform is not restricted by region and distance, and meets the requirements of decentralized front-end applications and centralized management of rental houses.
The coexistence of multiple workstations is a unique management method of the UISYS system, which is the modular management of different functions. The management department can perform management operations in the corresponding workstations according to management functions and management rights, avoiding the cross operation of multiple management departments on the same interface, reducing the impact of management personnel misoperation and illegal operations, and enhancing the security of the system Sex and reliability.
In the plan, in order to take into account the security of the rental house and the effective management of the entry and exit identification vouchers, and according to the actual characteristics of the rental house, the uniqueness of the ID card and the residence permit and the non-lending characteristics, the design adopts two-way swipe card entry and exit management Method and use of ID card or residence permit as the proof of entrance and exit for renters. In order to avoid situations where the elderly and children do not have ID cards or residence permits, the system also uses IC cards as the exclusive voucher for entry and exit of the elderly and children to achieve humanized management.
The system is also designed with a linkage function. When an alarm event occurs in the rental house or when entering or exiting the card, the system will link the electronic map, siren, camera, etc. to perform sound and light alarm and video recording, and display the alarm information or credit card record in real time, and capture images and information Bind and save for future reference.
The system has specially designed owner workstation and mobile phone workstation for rental house owners. Through the owner’s workstation or mobile phone workstation, the owner can permit and prohibit operation of the entry and exit authority of the rented personnel in his rental house, effectively controlling the phenomenon of lease renewal and malicious rent arrears. Through the workstation, the owner can also query the entry and exit credit card records and alarm records of the rental house, so as to know the situation of the rental house in time.
The system provides various operational queries and report output, and managers can perform related queries and print out according to their needs, so as to trace the relevant responsible persons.
3.2 System composition
UISYS access control management system is composed of server + basic functions (monitoring workstation, street office workstation, rental office workstation, neighborhood committee workstation, owner workstation, mobile phone workstation, linkage workstation, equipment workstation), etc.
3.2.1 Monitoring workstation
The monitoring workstation is one of the workstations of the UISYS access control management system. It is mainly used for real-time monitoring of the public security bureau/police station and displaying emergency alarms (such as fire alarms) that occur in various communities. The monitoring workstation adopts electronic map and graphical interface design to visually and intuitively display what location and what kind of alarms are generated.
The public security bureau/police station can quickly lock the alarm location through the electronic map

Community electronic map warning location display

Various alarm settings:

Alarm conditions and alarm level settings:

Alarm sound setting:

Real-time display of alarm events

Set up alarm linkage according to different events

Five levels of handicap dispatching personnel settings, automatic dialing of the set call when high-alarm

3.2.2 Subdistrict Office Workstation
The Subdistrict Office Workstation is one of the workstations of the UISYS Access Control Management System. It is mainly used as a management workstation for the Subdistrict Office to add renters and enter data.
Data entry for renters

Snapshots of renters

3.2.3 Rental office workstations
The rental office workstation is one of the workstations of the UISYS access control management system. It is mainly used by the rental management personnel to issue cards and authorize the rental personnel.
Issue cards to renters

Authorize renters

Key personnel concern settings:

Key personnel pay attention. When a rented person is set as the focus of attention, the system will generate an alarm as long as the rented person swipes his card, but it does not affect his normal entry and exit. For example, managers can set a certain suspect as a key focus object, and understand the whereabouts of the focus object in a timely manner, so that it can take countermeasures when necessary.
3.2.4 Owner’s Workstation
The owner’s workstation is one of the workstations of the UISYS access control management system. It is mainly used by the owner to control the entry and exit permissions of the rented personnel in their rented houses, as well as to monitor and display various alarm events and entry and exit records in real time.
The landlord prohibits entry and exit permissions by removing the rented personnel

The owner grants access rights by adding people

The owner monitors various event statuses of his own building through the owner’s workstation

3.2.5 Mobile Workstation
The mobile phone workstation is one of the workstations of the UISYS access control management system. It is mainly used by the owner to operate through the mobile phone to permit and prohibit the operation of the entry and exit permissions of the rented personnel in the rented house, and to control the door status.
Mobile workstation login interface

Mobile phone workstation building display interface

The owner allows or prohibits the operation of the access authority through the mobile phone workstation

Access permission operation

Access permission prohibits operation

Control the state of the rental house door through the mobile phone workstation

3.2.6 Linkage Workstation
The linkage workstation is one of the workstations of the UISYS access control management system, which is mainly used for linkage and taking pictures with the video surveillance system. Through the linkage workstation, when an incident occurs at the rental house door (such as normal card swiping, illegal card swiping, coercion to open the door, violent intrusion to open the door overtime, etc.), the linkage camera can realize real-time capture of on-site images and provide evidence for incident traceability.
CCTV alarm linkage

Event query and captured image playback

3.2.7 Equipment Workstation
The equipment workstation is one of the workstations of the UISYS access control management system, which is mainly used by equipment maintenance personnel to manage and maintain equipment and systems. The maintenance personnel of the equipment workstation can realize the addition, deletion, and modification of equipment, the definition of system structure, the management of operators and operation authority, etc.
Add equipment and parameter settings:

The template function can quickly add devices and configuration parameters, without adding and configuring each device one by one.

Through the secure object function, powerful operator authority management can be easily realized

The safety lock setting can lock the operation authority with the operator group to prevent misoperation and illegal operation.

Chapter 4 Hardware Products
4.1 Access Controller
4.1.1 MJ08/16/32NI
Model: MJ08/16/32NI
Detailed product parameters

4.1.2 FC01S Front Controller
Model: FC01S
Detailed product parameters
Card reader interface Wiegand26/34/66, Wiegand adaptive, RS485 interface
Communication interface: RS485
Number of control doors 2 doors
Electric lock control 1
Card interface: 2 way
Door open button 1 way
Door sensor input 1 way
Auxiliary input: 2 channels
Auxiliary input: 1 way
Working power supply Rated voltage DC12V Rated current <0.2 A
Working environment temperature -25℃ ~ 85℃, humidity 0-9 5%
4.1.3 MJ02NI
Model: MJ02NI
Detailed product parameters
CPU: ARM7
Communication interface: 10/100M adaptive Ethernet port
Storage capacity: 2M~32M
Number of card holders: Standard version 10,000/20,000/50,000/100,000 (customizable for larger capacity)
Historical record: Standard version 10,000/20,000/50,000/100,000 (larger capacity can be customized)
Input interface: Wiegand26/34/66, Wiegand adaptive, RS485 interface
Networking distance: unlimited
Anti-tamper input: 1 way
Anti-demolition input: 1 way
Interface protection: overcurrent, overvoltage, lightning protection, anti-reverse connection, anti-short circuit
Rated voltage: DC12V, stable working voltage range: 10~16V
Rated current: <0.2A (without card reader)
Working environment: temperature -25℃~80℃, humidity 5~95%, no condensation
4.1.4 Card reader
4.1.4.1 Haut-C3403G
Model: Haut-C3403G
Detailed product parameters
Card reading type ID card, residence permit card (temporary residence permit card), MIFARE 1 card
Interface method Wiegand interface
Card reading distance 5~10CM
Communication distance ≥100M
Working voltage DC 5V- 1 6 V
Quiescent current ≤80 m A
Working temperature -25℃~70℃
Working humidity 10%~90%
color: gray
Dimensions 126×76×23
4.1.4.2 Haut-C3404G
Model: Haut-C3404G
Detailed product parameters
Card reading type ID card, residence permit card (temporary residence permit card), MIFARE 1 card
Interface method Wiegand interface
Card reading distance 5~10CM
Communication distance ≥100M
Working voltage DC 5V- 1 6 V
Quiescent current ≤80 m A
Working temperature -25℃~70℃
Working humidity 10%~90%
Color dark gray
Dimensions 126×76×23
4.1.4.3 Haut-C3405G
Model: Haut-C3405G
Detailed product parameters
Card reading type ID card, residence permit card (temporary residence permit card), MIFARE 1 card
Interface method Wiegand interface
Card reading distance 5~10CM
Communication distance ≥100M
Working voltage DC 5V- 1 6 V
Quiescent current ≤80 m A
Working temperature -25℃~70℃
Working humidity 10%~90%
Color dark gray
Dimensions 126×76×23
4.1.4.4 Haut-C3410B
Model: Haut-C3410B
Detailed product parameters

[ad_2]