Security gun management system for military and political institutions based on semi-active RFID technology
[ad_1]
1 Introduction
1.1 Document construction instructions
The purpose of this program is to allow integrators, engineering companies and users to understand the design concepts, principles, overall planning and how to play its huge role in the field of Internet of Things RFID technology in school communication, home-school communication and campus safety management, and explain in detail the relevant Information such as the working principle and installation location of the Internet of Things equipment, so that integrators, engineering companies, and users can correctly understand the revolutionary changes brought about by the Internet of Things in the field of intelligent transportation, and establish a correct understanding of the Internet of Things in the field of security gun management in military and political institutions.
1.2 Explanation of terms and abbreviations
Term explanation
Term explanation
RFIDRadio frequency identification is a communication technology that can identify specific targets and read and write related data through radio signals without the need to establish mechanical or optical contact between the identification system and specific targets
The RFID active and semi-active radio frequency card is composed of an embedded processor and its software, a transmitting and receiving antenna in the card, a transceiver circuit and a high-energy battery. The special number is pre-stored in the microcontroller, and the unique encrypted identification code is transmitted intermittently Radio signal. The high-energy battery in the card provides energy for the normal operation of the active card, and the battery in the card can be replaced.
The industrial-grade omnidirectional reader is composed of information acquisition, processing, information transmission, and embedded software. Its main function is to complete the real-time acquisition and processing of the output signal of the active electronic label or the semi-active electronic label identification code.
Low-frequency activation locator and low-frequency activation access control device are used to trigger and wake up semi-active electronic tags.In the process of waking up, it can be used for various types of positioning and various types of access control statistics with the help of its characteristics.
The sound and light alarm is a device that is used to send out alarm information at the system terminal by using a switch to energize
2. Project background
2.1 System overview
system introduction
Police guns are a special tool to deter crime, so the management of police guns is particularly important. The management of police guns refers to the effective monitoring and management of guns in the storage, warehousing, transportation, use, carrying, and return. If the supervision is not in place, it will bring major security risks to the country and society.
This system uses RFID technology to be applied to the management of armed police guns, and uses the RFID gun monitoring cabinet to monitor the number and number of the guns in the cabinet in real time. It does manage all the links before, during, during, and in use, and return of the guns, and report the abnormal movement of the guns to the system monitoring center in real time.
This system is an automatic identification technology, a scientific and technological means that can effectively monitor the expenditure of guns online, and is an effective tool for tracking management and statistical management.
Problems that this system can solve
1. The guard post is on duty and the firearms are out of position to report to the police;
2. The outpost personnel on duty leave their positions to report to the police;
3. Handover of managed gun management personnel;
4. Monthly personnel induction statistics report, etc.
2.2 The idea of system design
The intelligent management system for prison guards’ guns involves embedded technology, mobile computing technology, radio frequency identification, computer software, databases, digital communications, etc. Therefore, in addition to its functions, the stability, reliability, anti-interference ability, fault tolerance and abnormal protection are also fully considered when designing the scheme. The system uses the existing mature industrial TCP/IP communication network as the main transmission platform, and the corresponding wireless identification base stations, RFID identification tags and other equipment are connected to the system, through the special software for the intelligent management of prison guards’ guns and the main system with a standard special database Perform background data exchange to achieve regional target tracking and positioning and safety management. The overall design of the system is mainly reflected in:
1) Realize the effective identification and monitoring of the entry and exit of targets in the deployment control area, so that the management system fully reflects “humanization, informationization and high automation”;
2) Provide managers with various management information such as personnel entry and exit restrictions, cross-zone alarms, safety monitoring, help alarms, and reasonable scheduling. Once there is an emergency, the system can immediately know and trace the location and traceability of all controlled targets. Sports history to ensure the efficient operation of safety management work;
3) The safety, scalability, easy maintenance and easy operation of the system design;
4) Easy networking, BS structure, easy realization of a wider geographical network monitoring;
2.3 System design features
1) Highly automated. The system can automatically detect the time and location information of the controlled target passing through the controlled area, and automatically realize the detection, statistics and safety management of the controlled target;
2) Mature and reliable network communication system. The wireless identification base station installed in the deployment control area transmits the collected information to the central centralized control system through the TCP/IP communication network in real time, without human intervention in the whole process;
3) Complete data statistics and information query software. The system software is equipped with a dedicated database management system, including information collection and statistical analysis system for controlled targets, statistics and management analysis system for attendance operations, display and print various statistical report data, for the query and management of prison guards and senior prison management staff A full range of services;
4) The safety, stability and reliability design of the system. The system products fully adopt the design of continuous and reliable working all-weather in an outdoor environment;
5) Complete alarm call system configuration for abnormal conditions (including invalid card, invalid card, unauthorized card entry);
2.4 Main functions realized by the system
1) Real-time tracking and monitoring of controlled prison guards and guns and emergency prison guard button for help, the position is automatically displayed;
2) Real-time query and print the current and a certain period of time controlled prison guards, the number of guns, activity trajectory and distribution;
3) Controlled guns and prison guards are forced to leave their positions without permission or due to other factors. The system will automatically alarm, and the video system will automatically pop up a video box. With the help of monitoring software, managers can clearly observe the scene of the incident online;
4) The system monitoring center station and network terminals can be operated in a local area network, so that all terminals on the Internet can share monitoring information and system comprehensive analysis information, and query various data reports within the scope of use rights;
5) The monitoring software has a strong drawing ability, and provides a corresponding graphics library, the operator can continuously monitor
At the same time, it is easy to realize online and complete graphic editing, drawing and modification;
The entire system will try its best to maintain the user’s existing network system and application system, and reserve interfaces, which can be combined with the existing application system or the future application system to realize the unified management function of multiple parties and reduce or avoid the user’s repeated investment.
2.5 Principles of System Construction
System construction includes both software and hardware. When developing, purchasing and integrating software and hardware, the company guarantees that the following principles are followed:
1) Advanced
The main construction idea of the intelligent management of prison guards’ guns is to use radio frequency automatic identification technology, embedded mobile computing technology and software technology to construct a product intelligent tracking system covering a large area, with the advantages of advanced technology, mature products, and high cost performance.
2) Economical
On the premise of ensuring that the technical requirements are met, the system design uses products with the best performance-to-price ratio as much as possible. The construction of the system maximizes the role of some of the original equipment, such as computer networks, equipment, software, etc., saves investment for users to the greatest extent, and protects existing user investments.
3) Practicality
The construction of the system fully meets the application requirements and actual conditions of this project, highlighting strong practicability, friendly interface and simple operation.
4) Scalability
In the system plan, the system capacity and network development plan are designed according to the viewpoint of system analysis and overall planning, which not only considers the current ease of use, but also has appropriate advancement.
3. General introduction of the system scheme
According to the overall functions of the system, the overall design plan of the prison guard guns intelligent management system consists of two parts: the first: the guard post firearms on duty, the personnel departure alarm subsystem; the second: the gun management personnel handover, the monthly report statistics subsystem for the post personnel. The two systems are complementary and mutually dependent to form a complete intelligent management system for prison guards’ guns.The following will introduce the system network construction topology diagram, working principle, system function, system composition, and system equipment installation topology diagram of the two subsystems respectively.
3.1 The Intelligent Monitoring Subsystem for Guns of Sentinels and Prison Guards
3.1.1 Topology diagram of system network construction

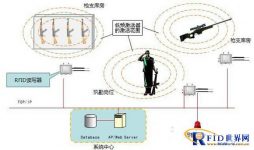
System network topology diagram
The reader adopts the RJ45 network interface. After the reader receives the data, it is transmitted to the Hub or wireless router through the TCP/IP network interface. The data read by the reader is transmitted to the local area network through the hub or wireless route, and is connected to the local area network The PC terminal can analyze the format of the data transmitted by the reader. After the data is analyzed, the PC server executes commands according to the pre-set program, such as: starting the alarm to alarm, recording the time of departure and other information.
3.1.2 The working principle of the system
1) Install an anti-disassembly electronic tag on the gun on duty at the sentry post. The tag is a semi-active electronic tag. It usually sleeps and only sends a signal to the outside world when it is awakened by a low-frequency activator, and the tag has electronic protection. Demolition function, when the personnel remove it from the gun, the electronic anti-demolition function is activated, and the label and related alarm devices will send out an alarm signal;

2) Install a low-frequency activator at the position where the sentry is on duty. The low-frequency activator has an antenna and the distance to trigger the tag is about 3 meters. If the tag is within the activation range of the low-frequency activator, the tag is activated and emits normal signals. The signal was received by a nearby reader;
3) Install a 2.4G industrial-grade omnidirectional reader near the duty position of the sentry post. The reader is an omnidirectional long-distance identification device. When a nearby tag is activated by the activator, it will receive the information of the tag, and when the tag is activated After leaving the active area and staying in sleep, there is no message that the reader cannot receive data, then the relay device inside the reader will act, and the acousto-optic alarm that drives the link will send out an alarm signal;
4) The personnel leaving alarm device has the same principle as the firearm leaving alarm.

Schematic diagram
3.1.3 System function
1) Real-time detection and inspection, the manager clicks the page refresh option, the receiver will call out all the sentry and prison guard status, sentry duty information, and sentry duty gun information within a few seconds, and upload System management software informs managers
2) Regional positioning, the regional non-precision positioning can be achieved by the receivers installed in different posts. Because the receivers installed in different sentries have different IP addresses, the receivers wirelessly receive the electronic label information for encryption, and send their own IP addresses to the upper computer. The upper computer uses different IP addresses and signal strength values. , The number of readings to make location judgments;
3) Firearms and prison guards leave their positions to report to the police. Prison guards and guns are equipped with active electronic tags. The electronic tags have a tamper-proof function. Once the tags are forcibly removed from the guns, the electronic tags immediately send a special ID to the receiver, and the receiver receives the signal and outputs a 5V switch. The signal drives the alarm to alarm; for prison guards and firearms who are not authorized by the leader, if they are forcibly taken out of the sentry monitoring area, the alarm will be triggered immediately to alarm;
4) Video linkage, on-site real-time online; each sentry is equipped with a monitoring probe, which works around the clock, and the information is stored in the hard disk memory in real time. When the receiver receives the special ID, it sends an instruction to the background service manager, so that a video box will pop up on the software, and the manager can instantly query the location of the abnormal situation and the on-site situation to avoid danger;
5) Call the police for help. When prison guards are attacked by prisoners or encounter special circumstances, they can press the label button to activate the alarm device to give an alarm.
3.1.4 System composition
1) Long-distance fixed omnidirectional reader (all-in-one);
2) Long-distance active anti-disassembly electronic tags, hung or pasted on the surface of the gun;
3) Low frequency activator;
4) PC display screen, server, computer;
5) Alarm controller and alarm;
6) Intelligent management system software for prison guards’ firearms, used for prison guards/gun authorization, location display, gun addition and scrapping, sentry guards’ readjustment and replacement, etc.;
7) A card issuer, which records information about prison guards and guns into the computer;
3.2 Perimeter prison guard inspection real-time tracking and positioning management subsystem
3.2.1 System function
1) Regional positioning, the non-precise positioning of the area can be achieved by the receiver installed on the fence. Because the receivers installed on different road sections have different IP addresses, the receivers wirelessly receive the electronic label information for encryption, and send their own IP addresses to the upper computer. The upper computer uses different IP addresses, signal strength values, The number of readings makes location judgments;
2) Firearms and prison guards leave their positions to report to the police. Prison guards and guns are equipped with active electronic tags. The electronic tags have a tamper-proof function. Once the tags are forcibly removed from the guns, the electronic tags immediately send a special ID to the receiver, and the receiver receives the signal and outputs a 5V switch. The signal drives the alarm to alarm; for prison guards and firearms who are not authorized by the leader, if they are forcibly moved away from the monitoring area, the alarm will be triggered immediately to alarm;
3) Firearms and prison guards cross the border to report to the police. Prison guards need to patrol according to the pre-set line, enter an unauthorized area without permission, the alarm will alarm immediately;
4) Video linkage, on-site real-time online; monitoring probes are installed around the wall, and the probes work around the clock. When the receiver receives a special ID, it will send an instruction to the background service manager, so that a video box will pop up on the software, and the manager can query it immediately The location of the abnormal situation and the on-site situation to avoid the emergence of dangerous situations;
5) Call the police for help. When prison guards are attacked by prisoners or encounter special circumstances, they can press the label button within the monitoring range to activate the alarm device to give an alarm.
6) Replay of prison guard and gun trajectory. The prison senior management can inquire about the trajectory of the prison guards in any period of time.
3.2.2 System composition
1) Long-distance fixed perimeter reader;
2) Long-distance active anti-disassembly electronic tags, hung or pasted on the surface of the gun;
3) Long-distance active button electronic tag, which can be carried by prison guards;
4) Special antenna for electronic fence;
5) PC display screen, server, computer;
6) Alarm controller, alarm;
7) Intelligent management system software for prison guards’ guns, used for prison guards/guns authorization, location display, gun addition and scrapping, sentry guards’ readjustment and replacement, etc.;
8) A card issuer, which records information about prison guards and guns into the computer;
4. System hardware introduction
RW-R 801 industrial grade omnidirectional reader
RW-R800 Desktop Card Issuer
RW-R750 (Access Control/Perimeter) Low Frequency Activator
RW-T737 dual-frequency anti-theft electronic tag
RW-T812 Keychain Electronic Tag
Way of working
The tag adopts “active or passive mode” to work, the tag actively emits a signal or is triggered by the instruction of the reader (or low-frequency activator) to emit the signal. The frequency of sending is adjustable.
The activators distributed in various areas or inside and outside the access control have been actively transmitting 125KHz low-frequency signals at close range. The dual-frequency electronic tags within the signal range of any activator can be successfully activated, and the digital number transmitted by the activator can be obtained. Calculate the RSSI field strength value. The tag then wirelessly transmits data such as “tag ID + tag status information + activator number + RSSI value” at 2.4 GHz frequency.
After receiving the wireless data, the neighboring 2.4GHz reader will upload it to the host computer through various standard interfaces such as RJ45 and RS485.
Access recognition
A 125KHz low-frequency activator can be installed inside and outside the door control (the effective activation distance can be adjusted by the antenna position, transmission power, antenna shape and size). The dual-frequency tags that pass through the access control will be activated by the activators inside and outside the door in turn. According to this sequence, the entrance and exit identification judgments of large and small access control can be accurately realized. Accurate floor determination can also be made.
Real-time positioning
According to some characteristics of 125KHz low frequency (such as field strength RSSI value, strong penetrating power, clear boundary, easy adjustment of signal range, etc.), multiple activators can be used to perform more accurate real-time positioning of the RTLS area.
Communication security
When the active electronic tag communicates with the supporting reader, a special communication protocol is used to verify the legitimacy of the device, and a meticulous encryption algorithm has been developed to prevent data cracking to ensure data security during the communication process.
Reliable work
The product meets the requirements of industrial environment applications such as waterproof, dustproof, and impact resistance;
Interface standard
Comply with ISO18000-4 standard specification
typical application
Access management of personnel, assets, and vehicles in various industries
RTLS real-time regional positioning of personnel, assets, and vehicles in various industries
Personnel and asset room identification and positioning, location and shelf management
Monitoring and management of electronic fences and boundary control lines
Vehicle weighing automatic identification system
[ad_2]


