Second-generation card telecommunications application solutions
[ad_1]
1. Application background of identity verification system
According to relevant statistics, the amount of mobile phone charges owed to China Mobile and China Unicom has reached 15 to 16 billion yuan. Due to the poor anti-counterfeiting performance of the first generation of ID cards and the shortcomings such as easy forgery, malicious arrears of fraudulent use of other people’s ID cards and counterfeit ID cards have emerged one after another, causing a lot of economic losses to the country and individuals.
With the renewal of the second-generation ID card nationwide, the security of the second-generation ID card for residents has been improved. In addition to visual identification, the authenticity of the ID card can also be identified by a machine. This greatly improves the security and reliability of identification, and will greatly reduce the loss of credit fraud in the telecommunications industry.
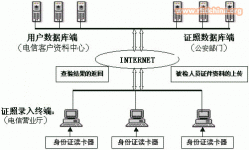
2. Identity verification system
System overall structure diagram

3. System design goals
⑴Two-factor verification: the authenticity of the identity is verified by visual and machine-readable two-fold verification to ensure the authenticity and accuracy of the user’s identity;
⑵Electronic entry: directly read user information such as user name and ID card number into the system, eliminating manual operation and improving entry speed and accuracy;
⑶Electronic management, optimizing the work process: eliminating the need to keep copies of ID cards and other links, saving costs and improving work efficiency.
⑷Information management: to realize the independent construction of payment, credit management/anti-fraud, unified customer information management and other systems.
⑸ Provide secondary application development for customer needs, such as the storage, query and index of the identified user identity information.
4. System composition

The system is equipped with an SDK software development kit, which can be well compatible with the original telecom business and charging system, and embed the certificate recognition collection program into the original various application systems. The device is light in weight, small in size, and the serial port completes data transmission. The acceptance of the transformation of the original business is very simple and convenient.
5. Work flow

6. System function
⑴Instant input of customer information:
The system uses a high-speed ID card reader (recognition of ID card images within 1 second) and high-precision recognition technology to solve the operational problems of slow manual entry by business personnel and difficulty in entry of rare characters;
⑵ Paper files become electronic management:
Extract customer information to the computer through a special reading software, without having to search through paper documents that are easy to lose or deteriorate;
⑶Introduce automatic identification technology: automatically convert customer profile, name, ID number, address and other information into database records;
⑷ Automatically establish a customer database: use the system to establish a database of basic customer information to facilitate information sharing;
⑸ Applicant record query:
Upload to the customer data center through the intranet line, and compare and query with the customer information in the library. If there is no record of the customer in the library and the identity verification is correct, the customer will open a new account for business registration; if the query is found in the library If there is the customer record and the customer status is normal, the effective customer new business registration will be executed; if the customer is found to be a “blacklisted” person in the database, an alarm will be issued and the corresponding processing will be carried out;
⑹ Do not increase the burden of investment: only need to install ID card information collection equipment and hook up with the original application system.
7. System advantages
(1) For the management department, it is possible to accurately grasp customer information; greatly reduce the workload of sales personnel; effectively filter malicious fraud by holding false certificates in advance, which is equivalent to plugging many loopholes in management and registration.
⑵For consumers, there is no need to fill in complicated forms; reduce the waiting time for customers to handle business; avoid others from borrowing ID cards or copies for malicious activities, and it is easier to distinguish the person responsible for the problem when traced.
⑶ Application of the customer ID card full information automatic collection system can effectively solve the management drawbacks and make the database and ID card information accurate; the data becomes valuable basic information such as reminders, tracing arrears, customer service, etc., and realizes customer electronic management . The information management department uses the “customer ID card automatic collection equipment + electronic database” program to reform the business process, so as to implement once and for all three-dimensional management of key links such as account opening, service, database construction, collection of arrears, and fraud prevention.
[ad_2]



