Design Scheme of Face Recognition Access Control System for Fei Ruisi Prison
[ad_1]
1 Overview of the prison face recognition access control system
With the advancement of prisons, the traditional monitoring and management model is facing the challenge of reform. On the one hand, the form of security protection is becoming more and more severe; on the other hand, the organization is compressed and personnel are streamlined. The new situation has put forward new demands for safety and security work. Under the unified arrangement of the prison, a face recognition access control system was set up in the area according to technical requirements, and the system was reasonably and effectively integrated to achieve an organic combination of physical defense, technical defense, and civil defense.
The prison gate and AB gate are important parts of the supervision site and the outside world. In order to strictly control the entry and exit of personnel in the prison area and production area, prevent criminals from escaping, realize effective unified command, and ensure the safety of supervision places, intelligent face recognition management systems are installed at the prison gates and AB gates.
The prison face recognition access control management system consists of the following 6 subsystems:
1. The entrance guard management system outside the prison
2. Access control management system for police passages
3. Access control management system for meeting family members
4. Vehicle access control management system (shares a system with police access)
5. Attendance system
6. Face management system for criminals in custody
2 System function
1. The entrance guard management system of the prison’s outer gate: the ID card recognition system is used in conjunction with the face recognition system to strictly control the entry and exit of outsiders to avoid the possibility of criminals using the identity of outsiders to escape from prison; this system is used for the data of all police officers in the prison Entry includes face image collection, personal information software, dispatch card, and registration of outsiders, including ID card identification, face image collection, personal information input, temporary card dispatch, etc.
2. Police access control management system: using IC card plus infrared face recognition, double verification, face IC card technology according to the uniqueness, certainty and classification characteristics of the face, the advanced face recognition technology and smart card read and write The technology is highly integrated, with all functions of face-to-face acquisition and IC card reading and writing, and features such as high efficiency, accuracy, and safety. It can strictly supervise and control the entry and exit of every police officer and outsider, and prevent the entry and exit of non-permitted personnel. In addition, it forms an alarm box matrix with the access control system, which is used for automatic pop-up of the corresponding cabinet when the police officer exchanges card A with card B.
3. Access control management system for meeting family members: The combination of face recognition and IC card is adopted to ensure a high degree of uniformity of personnel entering and exiting, to strictly prevent prisoners from pretending to be family members to escape from this channel, and strictly control personnel going out. And it is perfectly used in conjunction with the butterfly gate.
4. Vehicle passage access control management system (shares a system with police passage): It is used in conjunction with the police passage access control management system and strictly controls the entry and exit and inspection of outside personnel.
5. Attendance system: Infrared face recognition access control system also has an attendance system. At the same time, it can also use only the IC card attendance system according to the actual situation of each door. Face recognition and IC card management can be combined arbitrarily, which is convenient for management.
6. The face image management system of detained criminals: Using infrared face recognition technology, the face images of all detained criminals are recorded into the system database, and the personal information of the criminals is strictly managed.This system is installed in the Investigation Section to manage personnel information and face registration of all criminals in custody
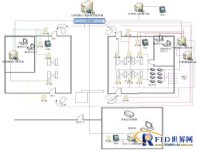
3Face Recognition Access Control System Expansion Diagram of Ferris Prison

4 System description, configuration introduction and implementation process
4.1 System description and configuration introduction
1. Install a face recognition access control system host at the outside gate of the prison, an external face recognition terminal and a card reader (using dual camera terminals, color + infrared), and an ID card recognition system.
2. 1 set of face recognition access control management system host, external 1 face recognition terminal and 9 card readers (using dual camera terminals, color + infrared); install a set of face recognition IDVR, connect the police channel and family channel AB The camera outside the door (IDVR function: in addition to the DVR function, there is also a face image capture function); 8 alarm box matrixes are installed, connected to the access control system, and connected to the cabinet locks of 1000 cabinets to automatically pop up the cabinets for easy replacement B card.
3. 1 set of face recognition access control management system host, an external face recognition terminal and 5 card readers (using dual camera terminals, color + infrared);
4. Install a face recognition system host for the face image management system of the detained prison in the investigation section (or other departments), and an external face recognition terminal (using dual camera terminals, color + infrared)
5. Install a face recognition server in the main monitoring room to back up data. The data can be coordinated with the attendance system to manage human resources and achieve attendance; establish a database, and all face recognition access control subsystems and prison management systems share the same server Database, easy to manage, and share information in time.
6. Install emergency door opening buttons on the inside of door A, outside door B, duty room or general monitoring room. Install door-opening buttons on the inside of door A and outside of door B beside the desk in the duty room or in the monitoring room to activate the button to open the door when urgently needed. )
In addition, due to emergency situations, for example, an emergency in the prison cell area and a large amount of police force is required to enter the prison cell, the butterfly gate can be guaranteed to be normally open or normally closed. This function can be implemented in 2 ways:
A. As mentioned above, a button is set in the duty room, and a button with password control can be installed as needed to prevent others from breaking into the duty room to maliciously control the button.
B. Use the software management control function to set management authority to realize the normally open or normally closed of the butterfly gate. It is recommended to adopt this scheme.
First, all police officers must go to the outside gate registration office of the prison, use the face recognition access control management system to register personal information, issue a new A card, and automatically generate the corresponding B card. The A card is worn by the police outside the supervision area, and the B card is stored in The cabinet in the police passage is used for wearing in the supervision area. And enter 5 personal infrared face images as templates and a color face image as archives, and verify and authorize them. When the police officer enters the prison area, he walks to the door A of the police channel and puts the IC card on the card reader. After confirmation, the camera of the IDVR system at the door A will record in real time and immediately capture the face of the police officer and pop it up in the duty room in real time. On the monitoring LCD screen, the person on duty compares the captured photo with the personal information on the IC card. After confirmation, the duty responder opens door A to allow the person to enter. Police officers must consciously and cooperatively look at the camera above the door to facilitate the capture of facial images.
After entering door A, the police officer uses the card reader on the butterfly gate with card A to swipe the card, and displays personal information on the monitor in the duty room. The access control management system sends instructions to the alarm box, and the alarm box immediately issues instructions to the corresponding card storage cabinet. The corresponding card storage cabinet is automatically ejected. After manual comparison, the staff on duty exchanges card A for card B, and the staff on duty opens door B to allow police officers to enter the supervision area.
4.2 Introduction to the system process
4.2.1 Police channel
Police officer
—Enter
First, all police officers must go to the outside gate registration office of the prison, use the face recognition access control management system to register personal information, issue a new A card, and automatically generate the corresponding B card. The A card is worn by the police outside the supervision area, and the B card is stored in The cabinet in the police passage is used for wearing in the supervision area. And enter 5 personal infrared face images as templates and one color face image as archives, and verify and authorize them. When the policeman enters the prison area, he walks to the gate of the police channel A, puts the IC card on the card reader, after confirmation, the camera of the IDVR system at gate A performs real-time video recording and immediately captures the policeman’s face image, and pops it up in the duty room in real time On the monitoring LCD screen, the person on duty compares this captured photo with the personal information on the IC card. After confirmation, the respondent on duty opens door A to allow the person to enter. Police officers must consciously and cooperatively look at the camera above the door to facilitate the capture of facial images. After entering door A, the police officer swiped the card with the card reader on the butterfly gate with card A, and displayed personal information on the monitor in the duty room. The access control management system sent instructions to the alarm box, and the alarm box immediately issued instructions to the corresponding card storage cabinet. The corresponding card storage cabinet will automatically pop up. After manual comparison, the staff on duty exchanges card A for card B, and the staff on duty opens door B to allow police officers to enter the supervision area.
—Out of the supervision zone
The police officer walks to the door B of the police channel with the B card, puts the IC card on the card reader, after confirmation, the camera of the IDVR system at the door B performs real-time video recording and immediately captures the police officer’s face image, and pops up the monitor LCD display in the duty room in real time On the screen, the person on duty compares this captured photo with the personal information on the IC card. After confirmation, the duty responder opens door B to allow the person to enter. Police officers must consciously and cooperatively look at the camera above the door to facilitate the capture of facial images.
After entering the B gate, the police officer must go to the face recognition terminal, swipe the card, and perform face recognition. The terminal will quickly recognize it and capture a color photo for archiving at the same time for easy query. After the verification is successful, the LCD screen below the terminal will display the police officer’s card number, time and other personal information. The access control system quickly passes through the alarm box, automatically opens the corresponding card storage cabinet, and prompts the location of the police card storage cabinet with a voice, and is on duty. The officer takes out the A card, puts the B card into the card storage cabinet, the A card is issued to the police officer, and the police officer can leave door A. If the face recognition verification is unsuccessful, the system quickly recognizes the captured face image with all criminal faces in the database. When the person is found to be a criminal or other unrecorded person, the system automatically sends out different levels of alarms.
foreign workers
—Enter
Outsiders entering the prison area must first go to the ID card recognition system at the prison’s outer gate with their ID card for verification. When the ID card is verified as a valid ID card, then the access control system is used, and the staff on duty allocates a new card to the outsider temporarily. Personnel, enter personal information and collect 5 infrared face image templates and 1 color, and verify them.
Outsiders are led by the police officers and enter the supervision area through the police passage. The entry process for the police officers is as above, and the outsiders only need to follow the police officers to enter.
—Out of the supervision zone
Outside personnel and police officers, when they come to door B, both of them need to put the IC card on the card reader. After confirmation, the camera of the IDVR system at door B will perform real-time video recording and immediately capture the face of the police officer and pop it up on duty in real time. On the room monitoring LCD screen, the on-duty personnel compare the captured photo with the personal information on the IC card. After the on-duty officer confirms both of them, the on-duty responder opens door B to allow entry.
After entering Door B, both police officers and outsiders must go to the face recognition terminal, swipe their card, and perform face recognition. The terminal will quickly recognize it and capture a color photo for archives at the same time for easy query. After the verification is successful, the LCD screen below the terminal will display the card number, time and other personal information of the police officer and outsider. The access control system quickly passes through the alarm box, automatically opens the corresponding card storage cabinet, and prompts the police card storage cabinet with a voice. Location, the duty officer takes out the A card, puts the B card into the card storage cabinet, and issues the A card to the police officer, and the police officer and outside personnel can leave door A. If the face recognition verification is unsuccessful, the system quickly recognizes the captured face image with all criminal faces in the database. When the person is found to be a criminal or other unrecorded person, the system automatically sends out different levels of alarms.
4.2.2 Channels for meeting family members
—Enter
When family members enter the prison area, they must first take the person’s ID card to the ID card recognition system at the gate outside the prison for verification. When the ID card is verified as a valid ID card, then use the access control system. ) To family members, enter personal information and collect 5 infrared mask templates and 1 color, and do verification.
The family members enter the supervision area through the channel to meet the family members, walk to the door A of the family channel, put the IC card on the card reader, after confirmation, the camera of the IDVR system at the door A will perform real-time video recording and immediately capture the face of the family member, and pop up in real time. On the duty room monitoring LCD screen, the on-duty officer compares the captured photo with the personal information on the IC card. After confirmation, the duty responder opens door A to allow the person to enter.
After entering gate A, family members swipe their card with a card reader temporarily stuck on the butterfly gate to display personal information on the monitor in the duty room. Swiping the card on the butterfly gate is valid.
—Out of the supervision zone
The process when family members leave the surveillance area through the family passage is the same as the process when outsiders exit the surveillance area from the police passage.
4.2.3 Vehicle entry
The vehicle is inspected by the existing system of the prison. If the personnel on the other vehicle are police officers or outsiders, they must follow the procedures listed above before they can enter the prison area.
4.3 Composition of a single access control system
4.3.1 Access control management system host
The host of the access control management system is a highly intelligent computer that works independently and is managed by the management and monitoring computer. The host of the access control management system has the following functions:
a) Face comparison and recognition: compare and recognize the face information collected by the face collector to confirm the legitimacy of the user. If it is a legal user, it will send a door open signal to the power station to perform access control. If it is an illegal user, it will refuse to open the door.
b) Data storage: store all the setting parameters, face information, and door opening records of the subsystem.
c) Lock control: Process the access control signal (such as door status signal, etc.) input through the lock controller to control the lock controller.
d) Execute the instructions of the management and monitoring computer: accept the instructions of the management and monitoring computer, and output the access control signal (open door, close the door, the door is normally open for a certain period of time, the door is normally closed for a certain period of time) and alarm signals to the lock controller , Realize the remote control function.
e) Signal collection: output the lock status signal collected by the lock controller to the monitoring computer to centrally monitor the working status of each subsystem;
f) Door opening record output: The door opening record is output to the management monitoring computer, and the access status of each access control point can be inquired in real time in the monitoring center, and the access control report can be output in a centralized manner.
[ad_2]


