Intelligent security management solution of GSM wireless access control for army gun warehouse
[ad_1]
1. The guiding ideology and overview of the design
With the reform and opening up and the vigorous development of the market economy, the management methods are becoming more electronic and informatized. The security system (TV monitoring, anti-theft alarm and access control) has become an important part of modern management, because the security system has greatly improved the security of the entire defense area. The safety factor increases the shock to criminals and greatly reduces the work intensity of security management personnel.
As an important place for storing all kinds of guns and ammunition, the Armed Police Force Guns and Ammunition Depot requires very high protection. Therefore, it is far from enough to rely solely on the past air defense, and the corresponding technical defense measures must be matched to achieve the goal of safety.
According to relevant security regulations and requirements, this program comprehensively considers various factors, adopts advanced monitoring equipment at home and abroad, and makes full use of our company’s rich construction experience and perfect service to install an advanced, mature and stable set of guns and ammunition depots. The network management and control system of the firearms and ammunition has been built into a first-class security monitoring system that meets actual needs, is economical and practical, has advanced technology, is convenient to operate, has strong scalability, and has standardized management.
2. System design user requirements
1. User situation: The guns and ammunition depots are located in *** city and surrounding districts and counties, divided into 9 squadrons, each of which has a squadron, with a total of 138 guns and ammunition depots. Each has a duty room, shares a service desk and a main door leading to the corridor of the building. In addition to storing ammunition, the ammunition warehouse also has anti-riot equipment.
2. User requirements: Police officers who receive guns and ammunition cannot enter the gate of the gun warehouse at will. Normal access needs to be confirmed by the detachment on-duty staff before they can enter the gun warehouse through remote grants. Specific requirements are as follows:
On-site door opening mode: When the on-site staff need to enter the gun warehouse, they need to apply to the headquarter. After the headquarter is remotely authorized, use the fingerprint mode to enter and it must be used by two people at the same time. Once in, the door is automatically locked and the next time the door is opened Must be re-authorized by the detachment.
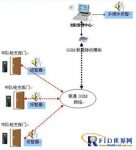
Data transmission and authorization line selection: The data management of the access control of the gun warehouse is transmitted to the detachment center access control management system through GSM in real time for display and processing; at the same time, the detachment center access control management system can directly authorize the access control unit of the squadron through GSM. Remote control to open and close the door.
System guarantee: The access control system uses GSM for communication, and uses RS485/RS232 to control through the army’s local area network (remote control to open the door) when the GSM communication is interrupted. In the case of GSM or intranet interruption, two or more other door opening methods should be provided to ensure that the door can be opened under normal demand.
System alarm: When the detachment allows the use of a mechanical key to open the door, an alarm sound can be issued on site, and the door opening alarm information will be reported to the central access control management system in real time via GSM. At the same time, the information is sent to the cell phone of the corresponding person in charge of the area. When there is an illegal intrusion (forcibly opening the door), an alarm sound can be issued on site, and the door opening alarm information will be reported to the central access control management system in real time via GSM. At the same time, the information is sent to the cell phone of the corresponding person in charge of the area. The management center can sound an alarm when it receives an alarm message.
The workflow is as follows:
1. When there is no weapon to use, the door lock will not be energized and cannot be opened normally.
2. When it is necessary to deal with the weapons in the weapon room, the squadron calls the detachment duty room. There are two situations:
A. If the squadron can unlock the lock with fingerprints normally, the squadron receives the squadron’s request to open the door. After the head of duty has passed the fingerprint verification, it is authorized to send an unlocking text message to the squadron weapons room. The weapons room receiving terminal transmits the unlocking instruction to the door lock after receiving the text message. When the door lock is powered on, the squadron can open the door by entering two fingerprints.
B. If the squadron cannot unlock normally (the squadron cadres with fingerprints are not on the spot, fingerprints are damaged, etc.), the squadron receives a call to open the door, and after the two fingerprints of the head of duty and the cadre on duty are verified at the same time, they are directly authorized to send the unlock to the squadron weapon room. Instruction, the weapon room receiving terminal will open the door directly after receiving the unlocking text message.
3. When the door lock is opened illegally, the squadron accepts the terminal to send an alarm message to the detachment, and the detachment duty room can instruct the squadron to check the safety of the weapon room based on this to increase reliability.
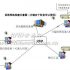
Equipment networking structure diagram: (take a single detachment as an example)

Three, system design
1. System design architecture:

2. Scheme equipment selection (main controller):
In response to customer needs, we chose Shenzhen Ruisheng Industrial RS-500GSM SMS base station access control management system. The selection basis is as follows:
Solid foundation: The manufacturer has 15 years of security experience and more than seven years of experience in the development of access control and other mainframes. The base station access control system is developed based on industrial control equipment technology and is durable.
Trustworthy: The manufacturer is the first domestic enterprise to develop and develop SMS access control. SMS access control systems have been developed for more than 5 years, and SMS access control systems have been used for more than 4 years.
Confidence guarantee: We are very familiar with the requirements of GSM access control management, have been successfully applied and thousands of devices are operating normally.
Humanized design: According to the characteristics of the room GSM application, the system also has the function of automatically forwarding short messages, or automatically forwarding the content of the alarm area short messages to the mobile phone of the management staff in the corresponding area, so that the alarm information can be processed in time.
Thoughtful thinking: There are multiple ways to open the door such as fingerprint input to open the door, proximity card to open the door, SMS to open the door, GSM remote door to open, and support dual fingerprints, four fingerprints at the same time to authenticate the door opening mode, which is convenient for different customers.
The most complete functions: door opening information, door closing information, door closing delay start information, door closing delay closing information, forced entry alarm start information, forced entry alarm end information, exit button opening information, door closing information, and remote control information are all uploaded and saved in real time , Well documented.
Perfect reminder function: once someone illegally breaks in and steals, the local alarm and headquarters alarm will sound at the same time.
Intuitive interface display function: In addition to the specific information of the corresponding personnel, it is also equipped with personal image information.
Comprehensive environmental monitoring: In addition to daily common functions, it also provides multiple input points for customers to access other equipment.
Anti-theft alarm function: With infrared, door sensor and other input interfaces, once the manned method enters the system, an alarm will be generated immediately and the alarm information will be uploaded in real time.
Multiple communication modes: GSM short message communication mode, LAN communication mode. And the two modes can be mixed and used at the same time.
function list:
.jpg)
3. Scheme equipment selection (application of fingerprint collector):
The fingerprint access control system takes advantage of the uniqueness and immutability of human fingerprints, and uses fingerprints as the feature of identity recognition to truly recognize people or objects, solve the security problem, and replace the traditional access control with keys and ICs. It is the most advanced and safest access control system, which has the disadvantage of identifying objects and not identifying people in identification methods such as cards and proximity cards. In this simple, safe and efficient smart fingerprint access control management, the user only needs to tap his finger to complete the operation easily.
Working principle: According to the uniqueness of each person’s fingerprint, the fingerprint is determined as the key. Through the pre-file in the system, the personal fingerprint characteristic value is stored in Fingerscan. When the user needs access, the fingerprint scanner collects the characteristic information of the user’s fingerprint, and passes the fingerprint characteristic value to the host for analysis and comparison after photoelectric conversion. , To determine whether the user has access permissions. If the user has the required permissions.
4. Scheme equipment selection (function conforms to certification):
Communication mode: Shenzhen Ruisheng Industrial RS-500GSM supports GSM and LAN communication modes, and has multiple communication modes that fully meet the requirements of Party A.
Door opening methods: The system itself has four door opening methods, including dual fingerprint input door opening, LAN remote door opening, GSM remote door opening, and wireless remote control door opening. If the key opening mode is added, there are five door opening methods in total.
System security: Supports the access of multiple detection devices such as door sensors. Once someone enters illegally, the system’s local siren will immediately generate an alarm to frighten the thieves. At the same time, the alarm information will be uploaded to the headquarters via GSM, and the corresponding alarm equipment of the headquarters will immediately generate an alarm. , And send the relevant alarm information to the mobile phone of the relevant person in charge in real time.
System software functions: door opening information, door closing information, door closing delay start information, door closing delay closing information, forced entry alarm start information, forced entry alarm end information, exit button opening information, door closing information, and remote control information are all uploaded and saved in real time, Well documented. And there is an operation log, and all the operating software information of the staff on duty is saved and can be queried.
Work flow: Work flow completely according to customer requirements.
5. Scheme equipment selection (system design composition):
Squadron equipment:
GSM wireless access controller;
Fingerprint collector;
Safety electric control door lock, door magnetic induction device
Alarm device, exit button
Detachment equipment:
GSM wireless receiving module
Management computer (provided by the detachment)
Speaker system (provided by the detachment)
Fourth, the main equipment performance of the system
1. Multifunctional RS-500GSM controller:
GSM wireless access controller is a comprehensive security management system integrating GSM wireless communication, embedded computer technology and radio frequency technology. The system hardware core adopts mega128 high-end microprocessor, adopts modular structure design, has powerful access control management function, and each access control point has the functions of patrol inspection and patrol sign-in; it is equipped with temperature and humidity collection ports. Real-time detection of environmental temperature and humidity; customizable 8-channel input, 8-channel output and linkage relationship between outputs, monitoring and linkage control of environmental variables (such as smoke detection, anti-leakage, fire protection, infrared anti-theft, etc.). The management center system software adopts SQL background database, maintains real-time wireless connection with each detection point, customizes each input/output port, collects the environmental variable data of each monitoring point in real time, and feeds back the working status of each point in real time through the electronic map. It is a comprehensive security management system that integrates access control management, anti-theft alarm, environmental monitoring, patrol inspection and security linkage functions. It is an important unattended location such as mobile base stations, unattended computer rooms, substations, bank vaults, oil fields, and granaries. The best choice for safety precautions.
SMS function introduction:
It can store the valid fingerprints downloaded from the SMS module;
Can upload entry and exit records of access control;
The door open and close state can be uploaded. When the door is opened and closed, the access control machine uploads the door open and close action state; when the control center wants to query the door state, the controller can upload the current state of the door;
Set the time period according to your needs, and you can set a time period (a certain year, a certain day, and a certain day) for fingerprints to enter and exit. After this period of time, the card is invalid;
Open and close doors remotely, add or delete fingerprints;
Can upload alarm information about illegal door opening;
Set the master mobile phone number, only authorized master mobile phone numbers can communicate with this controller and control the operation of this controller.
Control function introduction:
It can be connected to 2 fingerprint collectors and can control the two-way control of the entrance and exit of a door.
One set of electric lock relay and one set of alarm level signal output and six sets of relay output.
One set of exit button and one level of door sensor input and six sets of other switch input interfaces.
The exit button is controlled by time zone
Manage 20,000 valid fingerprints and store 30,000 access records offline
With the door open alarm for no reason, door open delay alarm function, offline can store 1000 alarm records
16 time zones can be set, each time zone can be set according to a weekly plan, and a maximum of four time periods can be set per day
Timing automatic opening/closing, remote opening/closing
Through different application software, it can double as attendance machine and patrol controller
Provide 232 interface for access to LAN
Small and beautiful appearance, with communication and power indicator lights
Pluggable terminal block, easy to install
technical parameter :
Power supply: rated voltage 12VDC (±10%) rated current <0.5A
Output parameters: working voltage DC≤15V, working current≤1A
Fingerprint reader interface: 12V DC, 150mA card reader power supply
Working environment: temperature -15℃~+60℃, humidity 0~90%
2. Fingerprint collector: (fingerprint machine with W26 interface)
[ad_2]