IoT smart prison management system solution
[ad_1]
1 System background
After more than 50 years of development since the founding of the People’s Republic of China, especially more than 20 years since the reform and opening up, the reform and development of our country’s prison management system has made remarkable progress. However, due to conceptual and institutional reasons, my country’s prison management system is still relatively backward compared with developed countries.
The original intention of setting up prisons in China is the same as in other countries, to realize the reform of criminals through labor. Many senior prison administrators believe that the key to the quality of prison management depends on monitoring, but if the monitoring is not well compatible and linked with other subsystems, it will actually play a very limited role in prison management.
We urgently need such a system. In the system, there are video surveillance functions, perimeter prevention and alarm functions, and access control, patrol, personnel positioning, and command and dispatch functions. Prison guards can know the specific location of inmates in prison in real time, what they are doing, whether there are violent conflicts, whether there are inmates intending to flee, whether there are police officers who have been kidnapped by inmates, and whether there are any visitors. In the plot to escape from prison. When these situations happen unfortunately, even if the on-duty personnel are negligent, they can also be informed of the situation on the spot through other means, and the preset effective solutions can be popped up in real time and staffed. In places like prisons where everyone needs to be monitored from time to time, it is also necessary to monitor the staff due to concerns about the access rights of relevant staff and their own management system.
In response to the above problems, China Chuangyi Technology has proposed a prison monitoring and management solution. This article will introduce the solution from three aspects: prisoner positioning management, regional prison staff management, and prison security comprehensive management.
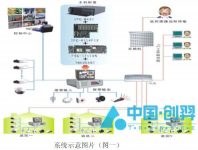
2 System overview
The prison personnel positioning system adopts the most advanced Zigbee wireless identification technology. According to the needs of prison personnel situation management and monitoring, a set of software and hardware application system is specially designed and developed. It is a safe and reliable way to distinguish and identify detainees. The intelligent prison administration management system realizes the informatization of prison management in a real sense and enters the path of “requiring police power from science and technology”.
The system enables managers to grasp the detailed information and number of detainees in each controlled area of the prison in real time, effectively prevent the escape of detainees, reduce the chance of criminals forming parties and making troubles, secretly monitor high-risk detainees, and track down and follow up on violent incidents. If it happens, the personal safety of managers and detainees is guaranteed to the utmost extent. In addition, the system can also automatically count the number of people in the designated area and the information of police officers on duty in the surrounding area, and dynamically monitor outgoing personnel throughout the entire process, which greatly reduces the work intensity of prison management staff. It can quickly locate the location of police officers on duty. The police can be mobilized efficiently in the event of an incident.
3 System principle and function
3.1 Supervised personnel management system
Prisoners bring a wristband electronic tag card into the surveillance area every day. Because the electronic tag is active, the working mode is active, that is, the ID number information is continuously transmitted to the outside. When the prisoner arrives in the surveillance area, install The card reader in the monitoring area will read the tag ID information, and the card reader will transmit the signal to the computer through wireless transmission or other intermediate devices, and the detailed information of the prisoner can be seen by comparing the ID number database. The fixed card reader in each monitoring area can be monitored at a fixed time interval through software settings. For example, it can be automatically refreshed once every 30 minutes, that is, it can be automatically executed once.
In all places of the prison: houses, roads, walls, etc., place RFID readers, cameras, speakers and other monitoring equipment. In the event of signal disappearance, unauthorized cross-regional behavior, disassembly or cutting of wrist tags, etc., the infrared camera immediately captures and records the on-site situation, and the central control room sounds and lights alarms. The horn is managed.

3.1.1 Real-time monitoring of personnel
The location of all detainees and police officers is displayed on the electronic map in real time, and the monitoring personnel can dynamically grasp the number of personnel and real-time distribution. Move the mouse to the personnel icon to view the detailed information of the personnel.

3.1.2 Personnel search and location
Enter the name or number of the personnel to quickly locate the location of the prisoner or police officer you are looking for.
3.1.3 Illegal assembly alarm
In the designated area, the system can set the maximum allowable number of personnel. Once the number of people exceeds the preset number, an alarm message will be sent out immediately.
3.1.4 Forbidden zone intrusion alarm
Some areas are restricted areas. Unauthorized entry of location tags will cause an alarm. When entering and exiting certain gates, you can set up which location tags can pass in advance. When the location tags that do not meet the requirements enter and exit the gate, an alarm message will be issued ; Or some areas can only be entered at a certain time, if entering at other times, it will be regarded as illegal intrusion, and an alarm will also be issued.
3.1.5 Unauthorized departure alarm
It is stipulated that certain prisoners cannot leave a certain area, or cannot leave a designated place within a certain period of time, and an alarm will be issued once they leave.
3.1.6 Activity track record
The system records the location and time of all personnel passing through all the time, can track and replay the personnel’s movement route, and master its detailed activity route and time.
3.1.7 Automatic roll call
It can automatically count the personnel of each factory regularly, showing the number of people who should have arrived, the number of people who have arrived, and the number of people who have not arrived. If the personnel have not arrived, an alarm will be issued in time to remind the prison guards to find and locate the missing personnel in time to prevent accidents. The prisoner has already set the workstation number in the system. Once the prisoner enters the wrong workstation or leaves the factory within an irregular time, an alarm message will also be issued.
3.1.8 Out of care alarm
Bind the prisoner location tag with the police location tag, which can be bound one-to-one or many-to-many. When the walking trajectory of the prisoner and the police are inconsistent for more than the allowed time, the system will send an alarm message. Or limit the distance between the prisoner and the police. When the distance between the two is more than the specified distance, the system will send an alarm message.
3.1.9 Emergency call
Prison guards and prisoners locate tags with alarm buttons. Once an emergency occurs, you can press the alarm button. The monitoring center can receive the alarm information in time, know the location of the alarm, and provide support quickly.
3.1.10 Remote monitoring and inspection
The system can be operated through the Internet to realize remote management and monitoring, and managers can check the prison situation at any time even if they are not in the prison.
3.2 Regional prison guards management system
Each prison guard in the area is issued an active tag, and the relevant information of the person is recorded on the tag, such as the person’s name, gender, date of birth, department, level, image, history records of entering and exiting the specified area, and access permissions, etc.; in the area A fixed card reader is placed at the gate to monitor the entry and exit of prison guards. When someone approaches the gate, the card reader will give an alarm first to remind the guard that the guard is about to leave the surveillance area. Then the card reader recognizes the tag and transmits the data to the upper computer of the terminal in the guard room, and the upper computer will display the specific information of the person, such as name and picture. If necessary, relevant data can be sent to the general control center; a certain number of fixed card readers can be installed in the area to realize the regional positioning of prison guards. The number of card readers installed is based on the on-site measurement area. The readers are arranged (each reader has a certain recognition range and can only recognize the surrounding area) as shown in the figure:

3.2.1 Accurate regional positioning
The system can realize area positioning, and in a controlled area, personnel can be positioned within an area. Since there are readers everywhere in the area, each area is within the signal range of the fixed reader, so all the electronic tags in the area can be covered by the information of the reader, so as to achieve regional positioning;
3.2.2 Strict access control
At the gate of the area, a fixed card reader is installed. Personnel want to leave the area, and the guard can only let him out after receiving the approval of two specific leaders. Otherwise, personnel are prohibited from leaving the area. When the person goes out, the reader records the time when the person goes out, and records and informs the time when the person returns. If the card reader fails to read the return information of the person within the specified return time, the system will alarm the guard and related personnel.
3.2.3 Judgment of persons approaching the gate
The system can judge the people close to the gate. When a person approaches the card reader at the door, the reader can send the read tag information to the system host computer at the door guard, and the system host computer can quickly call up the person’s basic information from the system database and display it on the host On board, such as name, department, photo, etc., so that the guard can better judge who is approaching;
3.2.4 Monitoring integration
The system can be integrated with the monitoring system of the area. After the area is located, the monitoring screen of a certain monitor in the area can be viewed;
3.2.5 PDA leader inspection
The system is equipped with a handheld PDA in case the leader wants to check the situation of the personnel in a certain area.
4 System software introduction
This article takes the prisoner location management system software as an example:
4.1 Personnel Information Management
Log in to the system by entering the corresponding user name and password.
4.2 Main function interface
The main function interface display: video linkage, personnel trajectory, personnel positioning, file management, abnormal alarm, data analysis, travel monitoring functions, click to enter the corresponding function interface.
4.3 Reader scan
The system can automatically detect the position and information of all the reading heads in the prison, making it easy to find and locate. The system includes two directional card readers and omnidirectional card readers. The test results are shown in the figure:

4.4 Personnel track management
Personnel trajectory tracking function is to provide managers with a more effective management mode, which can check the status of prisoners at any time: letting out, eating, working, studying, sleeping, etc. and moving the trajectory in this state. The trajectory can be displayed on the plane in real time. On the map, behavior analysis can be performed as a management basis for managers. As shown in the figure:

4.5 Personnel Location Management
Through the coordinated use of directional and omnidirectional card readers, precise regional positioning of personnel can be achieved, as shown in the figure:

4.6 Alarm management
Alarm management includes: illegal gathering alarm, restricted area intrusion alarm, unauthorized departure alarm, out of guard alarm, emergency call, equipment abnormal alarm, track abnormal alarm, etc.
4.7 Itinerary monitoring
Corresponding to special prisoners, the whole journey can be monitored for a certain person, and a specific area can be monitored and managed for a certain period of time.
4.8 File management
Establish a digital file of each person, record various information of each person in detail, and establish a multi-dimensional query system, which can query various information simply and quickly. The original personnel information system can be integrated to realize information sharing. Recording the daily behavior of the managed personnel can comprehensively analyze their behavior patterns. Automatically collect criminal information, fully realize informatization, establish a multi-dimensional database retrieval system for detailed digital files of each prisoner, and provide management personnel with comprehensive, fast and multi-dimensional query tools.
5 System characteristics
Bring the management of prisons to a higher level, conducive to reforming prisoners, and conducive to the construction of a harmonious society;
Adopt advanced RFID radio frequency identification technology to locate and track prisoners;
Not only can it meet the use environment in prisons, but it can also be extended to the field work to locate and track prisoners;
It can complete the interface with other systems (such as: fence, AB gate, high-voltage power grid, alarm, patrol, access control, intercom public address and other systems);
Information sharing can be browsed by other departments through the Internet.
6 System composition
Chuangyi Technology Prison Monitoring and Management System mainly consists of hardware equipment and software system. The hardware equipment adopts the latest high-performance products developed by our company. Main components: China Chuangyi third-generation anti-disassembly wristband, CY-RZGG-200 standard version reader, CY-RMZ-203 handheld + GPS+GPRS and Chuangyi technology information collection system.
6.1 China Chuangyi third-generation anti-disassembly wristband
Prisoner tag: It is worn on the wrist by means of a wrist strap. The tag is designed to prevent disassembly. Anti-disassembly wristband The electronic tag wristband is made of special materials and has a simple design. Any wearer will feel very comfortable. The product has the outstanding characteristics of ultra-low power consumption, long service life, low average cost, maintenance-free, and is safe and healthy to the human body, without electromagnetic radiation pollution, and safer to use. The anti-disassembly wristband electronic tag and read-write equipment can complete automatic identification of personnel and automatic inspection of legal identity without interruption. It can be widely used in attendance, personnel tracking, and automatic access management of personnel in schools, enterprises and institutions. Especially in today’s increasingly prominent security issues, the demand for safety management and real-time tracking of personnel in special industries is becoming stronger. The anti-disassembly wristband electronic tag has provided customers with success with its excellent performance, reliability and high cost performance. s solution.
Product (omitted)
7 System summary
Prisons are an important part of the national judicial organs and are responsible for the implementation of laws and regulations, education and reformation. The security of prisons is related to the stability of the society and its status is of decisive importance. Therefore, the construction of prison security systems is particularly important. Among them, through the integration of various security systems in prisons, the realization of the linkage of video surveillance and other security services is becoming the focus and difficulty of prison security construction.
The launch of Chuangyi Technology’s prison monitoring and management system will bring a brand new overall solution to the prison industry that can truly realize the full integration of all prison security services, providing a platform for resource sharing and information exchange for various business subsystems, and through video The linkage and integration of monitoring and other various security services improves the intuitiveness and convenience of management and prevention.
Currently, ZIGBEE technology has been applied to prison monitoring and management. Chuangyi Technology Prison Monitoring and Management System is an intelligent management system that distinguishes and recognizes prison inmates and managers in a safe and reliable manner, and associates each person’s information in the management system with each person in reality on a one-to-one basis. Realize the informationization of the prison management system in a real sense. It has been widely used in prison management in developed countries such as Europe and the United States. Practice has proved that this is a very efficient and reliable management technology.
[ad_2]


