Nanjing Shute Prison Access Control System Solution
[ad_1]
Overview
With the rapid development of information and network technology today, high-tech has promoted the improvement of productivity and also brought changes in people’s ways of thinking, working and lifestyle. The strategic policy of “strengthening the police with science and technology” is profoundly changing the traditional way of police work. The construction of prison access control is one of the important contents of the “Golden Shield Project” and is a necessary foundation for realizing the modernization of prison management and ensuring the safety of prisons. Our company has a prison access control controller specially developed for the needs of prison access control, which can meet the functional requirements of prison access control, and can also carry out secondary development for prison access control systems with special needs.
1. User needs
As a special area with high security, the control and management of the door is very important in the prison. In line with the concept of “wide entry and strict exit”, all access control adopts that entering the door must be swiped without verifying the password. When going out, the door must be swiped (or fingerprint, face recognition, iris, etc.) and then verified before the door can be opened. In the event of a fire alarm or other emergency situations, the access control system can be fully opened and fully locked through the access control management software. After the access control system is powered off, all door locks must be opened manually by the police.
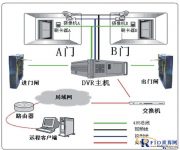
Prison AB door access control system

According to the actual requirements of prison management, adopting the management mode of AB door, the system will realize the dual-door linkage interlocking function, radio frequency identification technology plus authority, fingerprint recognition, face recognition, and control personnel entry and exit functions, and in the B door Make a buffer area on the outside. The implementation of the access control system is as follows:
a. When entering the supervision area in a normal state, swipe the card to open door A and enter the anti-trailing buffer area, and open door B by swiping the card again to enter the internal area. When leaving the supervision area, the center will conduct a third-party verification after swiping the card. The center will check whether the personnel in the surveillance video meet the exit authority. The whole process of going out.
Detailed description
1. AB door interlock function: After passing the first door, if the personnel who want to enter and exit the prison passage want to pass the second door to the prison, they must make sure that the first door is locked correctly before the second door can be opened. Greatly reduce the situation of anti-tailing.
2. Image capture function: the prison channel management controller is linked with the camera. When someone passes through the channel, the camera will capture an image and save it in the management center database. When the staff finishes the task, swipes a valid card or biometrics are recognized, the camera captures again The image is saved in the central database and compared with the first captured image. If all the information is consistent, the management center staff can release it.
3. Infrared alarm function: In order to further improve the anti-trailing function, install a pair of infrared radiation between the AB door channels, mainly installed above the three-roller gate, the purpose is to prevent the trailing person from trying to get from the three-roller gate without swiping the legal card Our infrared alarm was touched by jumping on the plane from time to time. Our management software will automatically handle locking the AB door and check the true identities of those who follow.
4. Anti-tailing management: after successful verification. Only one person can enter at a time, and the follower controller will automatically alarm.
5. Anti-duress function: When prison staff are held hostage by criminals to open the door, they can enter the anti-duress code and the alarm signal has been transmitted to the management center through the channel controller at the same time as the release, to notify relevant personnel to prepare for rescue.
6. Time period setting: According to the demand, you can freely set the invalid time period of opening the access control by swiping the card. At this time, it must be confirmed by the on-duty policeman to manually open the access control and release.
b. Abnormal state (special time period, emergency state:): There is an emergency in the prison, and the staff on duty can open the door AB by setting the software to open the door at the same time. When there is a dangerous situation to the supervision gate, the gate duty officer can set the software to close the door in an emergency, which can lock the AB door at the same time and close the passage. After the emergency is handled, the state of martial law is lifted.
The access control will have a self-check function: it can detect and alarm in time when the communication line is disconnected, the door is violently damaged, the AB door is not closed, the equipment is abnormal, the controller is powered off, and the backup battery is undervoltage.
2. System control method
The access control system in this system adopts non-contact IC card mode. A variety of access control methods can be used to control the users at multiple levels; at the same time, different areas and specific doors and passages in the prison can be controlled in and out; the system can also be networked for real-time monitoring. The use of a visual graphical interface and a development and application runtime platform is convenient for operation and secondary development. It can realize linkage control with other systems such as fire protection, CCTV system, etc.
●One-click martial law by the warden: By operating the access control management software on the computer, you can perform martial law and other management operations on all the access controls of the entire prison;
●Real-time monitoring: The system adopts TCP/IP control mode, which can monitor all door locks in real time, for the time period when the door is opened overtime (such as 30 minutes) or the door is not allowed to be opened (such as: late night 22:00 to 6:00 AM, etc.) An alarm will be issued if the door is opened abnormally. This function has a certain preventive alarm effect for preventing the accidental behavior of prisoners. The warden or legally authorized prison management personnel can monitor and query the status of the door and the door opening record in real time through the network;
●Detailed information record: There is a basis for opening the door. The record of each door opening is detailed and easy to inquire, and there is a basis for checking who, when, and which door opened;
●Level management: IC cards will be divided into multiple categories. According to work needs, different police officers have different permissions. For example, some cards can only open one door, and some can open one floor (or The entire squadron) all doors, and even one card is necessary to open the doors of a building or the entire prison. Of course, every time an IC card with any function is produced, the computer system has a clear record, such as who produced an IC card with what authority and when;
●Can report the loss: the system can report the loss of the lost card;
●Time setting: The system can set the time limit and time domain of the IC card to meet management needs;
●Data sharing: All data in the system supports network sharing for various analysis and inquiries.
Three, the solution
Shute Technology 2258 Smart Access Control Management System is mainly composed of smart card, computer, access control management software, smart card sensor, fingerprint access control machine, face recognizer, network switch, access control controller and electronic door lock. According to specific applications, auxiliary devices such as door opening buttons, door magnetic switches, alarms, communication repeaters, and card issuers can also be connected.

1. Access control at the gate of the prison area
Considering that there are network information points reserved in the supervision room in the access control system of the gates of the prison area (doors A and B), we recommend using Shute Technology 2258 smart access controller, which uses advanced TCP/IP protocol for communication , Can be directly connected to the local area network for use, with the help of the powerful communication capabilities of TCP/IP, it can meet the application occasions with large data volume and high real-time requirements.
The 2258 access control controller can control the access points of the prison gate at the same time. At the same time, the access control has the self-check function: when the communication line is disconnected, the door is violently damaged, the door is not closed for a long time, the device is abnormal, the controller is powered off, and duress It can detect and alarm in time when alarms, false locks of the lock body, mains power failure, undervoltage of the back-up battery, etc. occur. The electric lock used in the system is a mechatronics electric lock specially designed for prisons. It has high mechanical strength, good safety performance, and has anti-vandal and anti-opening design. Man-made damage to the lock body or other abnormal door opening conditions will trigger automatic Call the police.
By setting the authority password for each card, a double verification method of swiping card plus authority password can be realized, which can effectively avoid bad consequences due to card loss, theft or other reasons.
[ad_2]