RFID prison intelligent management and security system
[ad_1]
1. Current situation analysis
The current situation of prison personnel management in our country is mostly still at the stage of patrolling by prison guards and monitoring and alarming by cameras. With the gradual development of information construction, the prison system access control, security monitoring, emergency command system, etc. have made great progress, but there are still multiple systems that operate independently and cannot achieve linkage mechanisms; there are too many monitoring probes, and limited police forces cannot monitor all at the same time Camera status; due to the relatively lagging behind of the prison information construction, a series of vicious incidents have continued to occur, such as Henan Prison, Hanzhong in Shaanxi, Jieshou in Anhui, Hohhot, Changde in Hunan, Fangchenggang, Fuyang City, etc., which have caused extremes in society. Great harm, in order to prevent the recurrence of prison escapes and prevent criminals from harming society again, making the construction of information intelligence in prisons extremely urgent. The rapid development of RFID technology in the country has brought new opportunities for the intelligent construction of prisons. In order to improve the informatization level of prison management, promote the management of prison detainees to be institutionalized, standardized, and real-time, and ensure the safety and stability of prisons. The gradual realization of “intelligent all-round supervision” in the prison area has laid a solid foundation.
2. System design
2.1 Guiding ideology and principles of system construction
The system construction aims to improve the informatization level of prison management work and prevent the occurrence of jailbreak incidents. It focuses on real-time, efficient, and scientific prison management work, takes the promotion and full application of information systems as the core, and takes low investment and high Benefit and focus on quality as the goal, carry out system design and overall planning within the overall framework of the construction of the digital informatization supervision area, and comprehensively promote supervision in accordance with the overall construction idea of “planning, step-by-step construction, construction while using, and gradual improvement”. The process of informatization and modernization of the management and administration of detainees in the district.
2.2 System principle
The prison’s intelligent management and security protection system adopts the application of RFID electronic tags, and uses electronic tags as the most advanced identification code at present. It has the characteristics of not easy to break, reliable data, long service life, and long effective communication distance. It is a substitute for barcodes and infrared rays. The best choice for logos. Install it on the controlled target and use it as the unique identifier of the target for tracking and positioning. At work, managers use networked wireless identification base stations to track and locate targets.
2.2.1 Principles of RFID automatic identification technology
The system composed of RFID and short-range communication equipment mainly includes two parts: smart RFID and RFID read-write units (RWU). The wireless communication between the read-write equipment RWU and RFID realizes the communication between the information management system and RFID. Information exchange.
The read-write device RWU is an RFID read-write controller, which is composed of a microprocessor, a security module, a microwave communication controller and communication interfaces such as RS232, 485, TCP/IP, etc. It uses short-range communication protocols and microwave wireless transmission methods to realize RWU For the purpose of safe and reliable information exchange with RFID, RWU connects to the host computer through RS232, 485, WIFI, GPRS, TCP/IP, etc., receives control commands and data from the host computer and returns data.
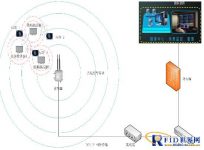
2.2.2. Principles of Regional Positioning and Tracking
ReaderSignal coverage is responsible for long-distance signal transmission, and the receiving range is constant; the wristband tag is a 2.4G&125K composite tag, which is responsible for receiving the low-frequency activation number sent by the low-frequency activator and transmitting this number to the reader in real time. The low-frequency activator is in the 125K frequency band, and the activator actively transmits continuous low-frequency pulse signals (the activator number is included in the carrier data); the matching low-frequency activation tag continuously turns on the low-frequency receiving function, and when it receives an activation signal from an activator, the tag The low-frequency chip will analyze the activator number in real time and detect the RSSI field strength value of the low-frequency signal, then wake up and pass it to the MCU microcontroller, and then turn on the on-board 2.4G radio frequency chip for a strong signal transmission (wireless transmission) The data packet contains the tag ID, activator number and low-frequency field strength RSSI value).
Schematic diagram:

1. When the wristband tag is in the low-frequency activator 1, 2, 3, the activator 1, 2, 3 will transmit its own activation to the wristband tag, the wristband tag will send the activator to the reader, and the reader will The information is transmitted to the background, and the management platform locks the tag position to the 3-meter area covered by the activator according to the location of the reader and the number of the low-frequency activator in advance.
2. When the wristband label is at the cross position of the low-frequency activator 1, 2, 3, the activator 1, 2, 3 will transmit its own activation code and its own signal strength value to the wristband label, and the wristband label will transmit the activator number and signal The strength is sent to the reader, and the reader transmits the information to the background. The management platform calculates that the wristband label is closer to the activator according to the location of the activator in advance and the signal strength, so as to achieve three-point area positioning and precise positioning.
2.3 System components
The system consists of 4 parts: prison intelligent management and security system software, RFID data acquisition system and video alarm linkage system, visitor management system
2.3.1 Prison intelligent management and security system software
The software mainly consists of three parts
1) The collection terminal of the prison intelligent management and security system: receiving data system, running in the background, no operation interface.
2) Prison intelligent management and security protection system server: only placed in the management center, logged in by the administrator, basic data maintenance can be performed, and all positioning information is displayed.
3) Prison intelligent management and security protection system client: placed on the client, logged in by general users, display the location information of the current floor.
2.3.2 RFID data acquisition system
The system consists of the following parts
1) 2.4G reader (directional reader, omnidirectional reader)
Orientation reader: It is mainly used for receiving signals from activated wristband tags on prison walls, and for large-scale coverage of signals in open areas and positioning in large areas.
Omnidirectional reader: It is mainly used for the positioning of prison production areas, living areas, restaurants and other areas, and it also receives signals from activated tags in the prison room.
2) 125K low frequency trigger (access control trigger, perimeter trigger)
Access control trigger: It is mainly used to judge the direction of the entrance and exit of detainees in each prison area. The access control activator can realize the remote open attendance of detainees and prison guards and record the time of entry and exit in real time. It can also realize large areas through the access control activator. Precise positioning;
Perimeter trigger: It is mainly used to control the prison wall and judge the entry and exit of the wider entrance guard. Through the perimeter trigger, it can prevent prison detainees from escaping from the gate and wall, and prevent the occurrence of escape time.
3) Anti-disassembly prison wristband label (anti-disassembly, waterproof, shockproof, replaceable battery)
Anti-disassembly prison wristband label: This wristband combines 125K&2.4G two frequency bands, if the customer needs it, it can be combined again.
An IC card to realize the functions of access control and attendance, dining in the cafeteria, and supermarket shopping; the main function of the wristband is to be worn by prison detainees to prevent or prevent prison detainees from escaping through the fence and door control;
4) Prison guard electronic tag (with the function of asking for help and alarming)
Prison guard electronic tags: Prison guard electronic tags are worn by prison guards, which mainly play a role in protecting their own life and safety.
When prison guards are besieged by prison detainees or found that detainees gather for fights or escape from prison, they can use the prison guard label button and anti-disassembly chain to realize help and alarm to avoid serious accidents;
5) Handheld reader
The main function of the handheld reader: the prison guard monitors the detainees who seek medical treatment on bail (the detainee leaves a certain area of the prison guard, the handheld device will alarm in time, and the handheld GPS or police car GPS coordinate information and special help signal information will be sent back through the handheld GPRS remote transmission function. Go to the command center in the background to facilitate the command center to take emergency measures to avoid accidents;
6) Computer network equipment
Computer network equipment includes computer servers, monitors, network switches, hubs, network cabinets, etc.;
2.3.3 Video alarm linkage system
System composition
The video alarm linkage system mainly consists of cameras, pan-tilts, protective covers, lenses, alarm controllers, sound and light alarms, etc.
2.3.4 Visitor Management System
System composition
The visitor management system is mainly composed of query machines (with second-generation identity card readers), application software, switches, and servers
3. Overall system architecture
3.1 The overall design of the system

System overall design drawing
Remarks: The design of the entire prison includes three parts: the perimeter area of the prison wall, the production workshop and the living area and other internal areas, and the non-indoor area within the wall. The three parts are independent and closely related to each other, forming three prison security precautions. system.
3.2 Software system architecture

Software system architecture
4. System function
1) Real-time tracking and monitoring of the controlled target and emergency button for help, and the position is automatically displayed;
2) Real-time query and print the number of controlled targets (production area, living area, leisure area, etc.), live
Dynamic trajectory and distribution;
3) Detainees trespassing in the restricted area backstage will automatically alarm.Some areas are restricted areas (wall guard area, dangerous goods source area
Etc.), unauthorized detainees illegally break into the background system and automatically alarm and pop up the video window of the incident; at important prison gates, the permission and time period permissions can be set in advance, and the entry and exit of unauthorized personnel will automatically trigger the alarm ;
4) Unauthorized departure alarm, detainees or prison guards in specific areas such as living area, production area, prison, prison guard sentry area, etc. are not allowed to leave the area without authorization. Once they leave illegally, the system will automatically alarm and leave the personnel’s identity information, Location information is automatically displayed;
5) Track playback, prison managers and authorized leaders can query the movement track of a certain prison detainee or a certain group of detainees during a certain period of time according to their own authority;
6) The detainees will automatically alarm when they leave the custody of the background. The prison guard wears a handheld and the detainee’s wristband is authorized by the background to communicate with each other. If the distance between the two exceeds the allowable range, the background automatically activates the alarm device;
7) Emergency call for help and emergency help are divided into two situations: 1. When prison guards are besieged by detainees or some detainees find bad intentions, they can press the prison guard card button or pull off the anti-disassembly hanging chain for emergency help; 2. . Prison detainees can press the wristband label help button to ask for help when encountering a besieging situation or other threats to their own safety;
8) All-in-one card function, the prison electronic wristband has a built-in contactless all-in-one card chip. The prison guard card can realize access control, electronic door lock, inspection, attendance and internal consumption functions, and the electronic wristband of detainees can realize functions such as dining and internal consumption;
9) Query statistics and report functions, the management system can automatically generate various charts that meet the daily management of managers
Including: bar graph, pie graph, curve graph, list, etc. These charts can conveniently help prison managers analyze and count the work and activities of various personnel over a period of time, as well as the occurrence, frequency, location, and cause of various alarm events that are necessary for prison management. factor.
10) Armed police and their out-of-position alarm. For armed police and firearms that are not authorized by the leader, if they are forcibly taken out of the sentry monitoring area, an alarm will be triggered immediately;
11) Video linkage, on-site real-time online; monitoring probes are installed in sentries, prisons, production areas, living areas, leisure areas, etc., the probes work around the clock, and the information is stored in the hard disk memory in real time. When the reader receives a special ID (the prison guard has illegally left with a gun, the detainee breaks into an unauthorized area, the prison guard is surrounded, etc.), it sends an instruction to the background service manager to pop up a video box on the software, and the manager can Instantly check the location of the abnormal situation and the on-site situation to avoid dangerous situations;
12) The visitor system, the identity verification of visitors and prison internal personnel entering and exiting the prison gate, improving the security level;
5. System overall design
The overall plan is the top priority of the prison’s intelligent management and security system construction. Our company has conducted detailed investigations on the escape incidents in recent years, and according to the work process of prison guards and the law of activities of prison detainees, the intelligent management of the prison is carried out. And the construction of the security protection system is divided into three parts: the intelligent management system of the prison area, the intelligent management system of the medical service organization outside the prison area, and the intelligent management of the medical treatment outside the prison. The three parts complement each other and jointly build the intelligent management and security protection of the prison. system.
Below we will explain in detail the three components of the prison’s intelligent management and security system:
5.1 Intelligent management system for prison area
The construction of an intelligent management system for prison areas mainly includes the following parts: 1. Perimeter management systems such as prison walls, production areas, and living areas; 2. Real-time positioning systems for access control and area of living areas, production areas, restaurants, prisons, etc.; 3. Gun management system for guard posts and armed police;
1) Perimeter management system for prison walls, production areas, and living areas
Prison wall
The prison fence is the last security guarantee of the prison’s intelligent management and security system, which prevents the prison from being detained.
The most important checkpoint for personnel to escape from prison plays a decisive role in the security of the entire prison system. Therefore, the requirements for the stability, timeliness, and anti-interference of the equipment are extremely high. In order to ensure the stable operation of the system, we will design the plan Fang gave thorough consideration.
The composition of the prison fence perimeter management system: 2.4G directional reader + 125K perimeter activator + 125K cable antenna, the equipment installation layout diagram is as follows:

Schematic diagram of equipment installation and layout
Prison perimeter function: prevent detainees from breaking out of prison; when detainees are close to the electronic fence about 3 meters (with an error of not more than 50 cm), the alarm device will automatically start the alarm, and the large screen will display the scene of the incident-breaking into the restricted area and being in custody Personnel identity information, location information and online viewing of the scene through the video linkage function;
Prison perimeter installation method: along the middle of the fence or 30 cm from the fence shallowly buried underground (the perimeter cable antenna needs to be covered with PVC pipes to prevent the antenna from bending and deforming, being corroded by water, etc.), install a perimeter activator every 50 meters And a waterproof test electronic tag (when the activator is damaged, it can be detected in the background to ensure the stable operation of the activator), and a directional reader is installed as a signal receiver every 80 meters.
Production area, living area, etc.
Directional readers + perimeter activators + perimeter cable antennas must also be installed on the boundaries of production areas and living areas to prevent detainees from entering illegal areas without permission and prevent accidents; monitoring center prison guards and Senior prison leaders can set the boundaries according to actual needs, such as: how far away the detainees are from the boundary, call the police, detainees are not allowed to enter a certain area during a certain period of time, and detainees can enter the perimeter for a certain period of time to clean up Lawns and so on;
2) Gun management system for sentries and armed police
The construction of the guard post and armed police gun management system includes two parts: first, the intelligent monitoring subsystem of guard post and armed police guns; second: real-time tracking and positioning management subsystem for perimeter prison guards;
◇ Intelligent monitoring subsystem for sentry and armed police guns
The construction plan of the intelligent monitoring subsystem for the sentry and armed police guns

Construction plan
A set of information collection equipment is installed inside or on top of each sentry post, which is responsible for receiving armed police gun electronic tags and emergency help signals issued by armed police (detainees snatching guns, detainees fighting, detainees having abnormal behaviors, etc.) and responsible for passing information through the RJ45 network Pass it to the back-end monitoring center; the armed police gun stock is equipped with a special electronic tag, and the electronic tag will send the electronic tag signal to the signal receiver in real time. If the back-end does not detect the electronic tag within a period of time (such as: 5 seconds, 10 seconds, etc.) The alarm system and security monitoring system of the monitoring center will automatically start. At this time, the LCD screen will display the current sentry situation, the identity information of the armed police on duty, the position information of the armed police on duty, etc. The monitoring center can dispatch the nearby armed police to assist in processing according to the actual situation. Emergencies to prevent serious situations from appearing.
◇ Perimeter armed police patrol real-time tracking and positioning management subsystem
Perimeter armed police patrol real-time tracking system functions:
1) Regional positioning, through the activator and signal receiver installed on the fence, the regional non-precision positioning can be realized
2) Alarm for firearms and armed police when they leave their positions
3) The armed police failed to patrol the scheduled route with guns, and the system called the police
4) When the armed police encounter an emergency, they call the police for help
5) Armed police and gun track playback
3) Real-time positioning system for access control areas such as living areas, production areas, restaurants, prisons, etc.
The real-time positioning system for access control areas such as living areas, production areas, restaurants, prisons, etc. includes two parts: first, the regional access control management system; second, the regional real-time positioning system;
◇ Regional access control management system
Investigation on the status quo of access control management: Detainees from the living area to the production area to work, eat in the restaurant or return from the production area to the living area, are led by the team leader and registered in and out through the only channel inside and outside the gate. At present, manual registration and counting of the number of people are used, and the work intensity of prison guards is very high. Through the regional access control management system, the data of the roll call can be directly transmitted to the prison guard’s PDA or background monitoring center through the local area network or WIFI, GPRS, etc., thereby reducing the work intensity of the prison guard.
Regional access control management system function: real-time roll call and specific authority settings for detainees from the prison living area to work and production areas, restaurants, cells, etc., when they pass the gate (gate) (a detainee can only pass the access control within a specified time, Otherwise, an alarm will be triggered) to strengthen the standardization and safety of prison management;
Take the living area to the production area as an example, as shown in the figure below:

Access monitoring map
Install a set of 125K access control activator and signal receiver in the living area and production area channel (determined by the on-site environment). Because this channel is the only channel for all detainees to enter the production area or return to the living area, there is a large daily flow of people for the system Higher reliability, dual-antenna access control can be used;
The system will automatically record the entry and exit information of all detainees (personal information, quantity, entry and exit time of detainees), and can automatically match the rules of the background system. When detainees who do not meet the passing rules pass, the duty room immediately performs sound and light Call the police and record violations.
◇ Regional real-time positioning system
The regional real-time positioning system mainly monitors personnel in large areas such as prison living area, work area, and activity area. Through the combination of omnidirectional locator, directional reader, and boundary activator, it is aimed at production area, activity area, etc. Carrying out all-round location monitoring, real-time understanding of the details of detainees and prison guards, and intuitive understanding of the actual number of personnel in the area, personnel information, etc., which can be understood at a glance through software, which greatly reduces the workload of prison guards and realizes Technology requires police force.
【Function description】
In indoor and outdoor labor places, key prisons, toilets, squares and other areas, signal coverage is achieved through the combination of omnidirectional positioning receivers and directional positioning receivers;
The system will roll the names of detainees in the area every 5-10 seconds (settable). When the detainees leave the designated area, the system will immediately alarm and display the alarm location and information of the detainees in violation of the rules.
The system can also control and restrict each area according to the event segment. If a person enters the area during the controlled time period, the system will immediately sound and light alarm and notify the nearest prison guard to deal with it in time, which greatly avoids accidents. , The setting of controlled time can be flexibly changed with the prison regulations.
5.2 Intelligent construction of medical service institutions outside prison
The overall construction of the prison’s intelligent management and security system needs to take into account the intelligent construction of medical service institutions for detainees to seek medical treatment. In recent years, there have been incidents of detainees’ escape from prison for medical treatment. The painful lessons remind us that we must not ignore the detainees. Take care of all aspects.
Taking into account the cost of intelligent construction of the entire prison staff and the particularity of medical service institutions outside the prison area, the intelligent construction of medical service institutions outside the prison area can adopt a policy of focusing on deployment and control, focusing on the future, and gradually improving, such as: entrance and exit of the building, Install positioning equipment for inter-floor passages, electronic fences, and hospital entrances and exits to prevent accidents;
[ad_2]