Application scheme of underground personnel and equipment positioning system
[ad_1]
1. System overview
As a basic energy source, coal has made great contributions to my country’s economic growth for a long time. 70% of my country’s energy consumption comes from coal, and it has always occupied a leading position in the development of the entire national economy. But on the other hand, due to the industrial structure of the coal industry, there is a huge gap between its mining equipment, the quality of its employees, and the level of science and technology compared with other industries. Especially in recent years, the number of coal mine accidents has been increasing. How to strengthen safe production and improve the efficiency of search and rescue work has been placed in front of the state, competent departments and leaders at all levels. The main reasons for these major accidents are:
(1) The information communication between the ground and underground personnel is not timely;
(2) It is difficult for surface personnel to dynamically grasp the distribution and operation of underground personnel in time, and to accurately locate personnel;
(3) Once a coal mine accident occurs, the efficiency of emergency rescue and safety rescue is low, and the search and rescue effect is poor. In order to maintain coal mine safety production, four ministries including the State Administration of Work Safety and the State Coal Supervision Bureau have issued “Several Guiding Opinions on the Management of Labor Quotas in Coal Mining Enterprises.” The “Opinions” stipulate that in the production process of coal mines, the mine mouth must be listed to indicate the actual number of people working underground. This is also the bottom line of the lowest technical measures for relevant national departments in order to promptly organize emergency rescues in the event of a coal safety accident.
Coal miners have high work intensity, heavy work pressure, and various realistic factors. It is difficult to require every underground worker to consciously sign in before going down. For this reason, how to correctly handle safety and production, safety and efficiency Relationship, how to accurately, real-time, and quickly perform coal mine safety monitoring functions, effectively manage miners, and ensure the efficient operation of emergency rescue and safety rescue is particularly important and urgent. Facing the new situation, new opportunities and new challenges, the leaders of the national competent departments at all levels put forward high requirements and expectations for work safety. At the same time, how to change the current management mode of coal mine enterprises for the lagging people underground, and how to realize the modernization and informatization of management have also become the concerns of all coal mine enterprises. We believe that it is imperative to establish informatization and intelligentization with the main objectives of disaster prevention, accident rescue, and electronic information management.
During the “Tenth Five-Year Plan” period, the electronic information construction of the coal industry was based on the development of the “Ninth Five-Year Plan”, focusing on the strategic tasks of reforming and developing the coal industry, focusing on the development and utilization of information and knowledge resources, combining with the actual needs of the coal industry. The informatization construction of coal mine production safety monitoring and control, automatic control and enterprise management systems has been incorporated into the operation and management schedule of safety production enterprises. As a leader in RFID technology, Beijing Lianxin Yongyi Technology Co., Ltd. has adopted the latest international RFID technology and developed a “underground personnel and equipment positioning system”. The realization of this system will improve the safety production and operation management of coal mine enterprises. Steps,
Upgrading brings new opportunities.
Radio frequency identification technology (RFID) is an advanced technology that uses electronic chips for non-contact automatic management. When entering and exiting personnel wear an identity card equipped with a radio frequency identification chip and pass through the door, they can complete identification and identity verification without any operation. The whole process operation to the pass record. And it can communicate with the back-end management system to provide real-time and reliable technical guarantee for the safety management of downhole personnel.
working principle
The underground personnel management system belongs to the category of coal mine safety management system. Install automatic card reader control devices at the passage openings of important parts such as controlled management areas, entrances and exits, main equipment control center computer rooms, valuables warehouses, and manage and monitor through the central control room downhole personnel management security management software. The system adopts The computer multi-task distributed processing mode can carry out real-time control or set program automatic control on the position of each passageway, passage object and passage time. This technology has been widely used in the entrance and exit security management of government agencies, enterprises, finance, public security departments, military bases, smart communities, schools, and high-end hotels, and has played an important role.
2. Introduction to RFID
1. RFID concept
RFID is the abbreviation of Radio Frequency Identification, that is, radio frequency identification. It is a non-contact automatic identification technology that automatically recognizes target objects through radio frequency signals and can quickly track items and exchange data. The recognition work does not require manual intervention and can work in a variety of harsh environments. RFID technology can identify high-speed moving objects and can identify multiple tags at the same time, and the operation is quick and convenient. It provides the possibility for the perfect realization of ERP, CRM and other business systems, and can greatly improve the business and business model. RFID technology was born during the Second World War. It is the successor of traditional barcode technology, also known as “electronic tags.” The US military began to study RFID technology as early as the second half of the 20th century, and this technology has been widely used in weapons and logistics management systems. During the “Iraq War”, the United States used RFID to deploy weapons and materials very accurately, ensuring the accurate supply of front-line ammunition and materials.
In recent years, RFID has attracted attention due to its long-distance reading and high storage capacity. At present, many multinational companies, including Wal-Mart, have begun to use RFID technology to assist enterprise management. At the same time, many warehouses abroad also use RFID technology to realize warehouse automation management. According to relevant authoritative data, the worldwide sales of radio frequency identification products are increasing at an annual rate of 25.3%.
2. RFID system composition
Tag (i.e. radio frequency card): It is composed of coupling elements and chips. The tag contains a built-in antenna for communication with the radio frequency antenna.
Reader: A device that reads (and can also write in the card reader) tag information.
Antenna (built-in): transmit radio frequency signals between the tag and the reader. Some systems also connect to an external computer (host computer system) through the RS232 or RS485 interface of the reader for data exchange.
3. RFID technical features
1) Data reading and writing (Read Write) function: as long as the RFID Reader can directly read the information into the database without contact, and can process multiple tags at a time, and can write the status of logistics processing into the tags for download For one-stage logistics processing.
2) Easy to miniaturize and diversified shapes: RFID is not limited by size and shape in reading, and does not need to match the fixed size and printing quality of the paper for reading accuracy. In addition, RFID electronic tags can be miniaturized and applied to different products. Therefore, the production of products can be controlled more flexibly, especially in the application on the production line.
3) Environmental resistance: Once the paper is soiled, it will be invisible, but RFID has strong resistance to water, oil, medicine and other substances. RFID can also read data in a dark or dirty environment.
4) Reusable: Since RFID is electronic data, it can be overwritten repeatedly, so the label can be recycled and reused. For example, passive RFID can be used without a battery, and there is no need for maintenance.
5) Penetration: If RFID is covered by non-metallic or non-transparent materials such as paper, wood and plastic, it can also communicate through penetration. However, if it is ferrous metal, communication is not possible.
6) Large data memory capacity: Data capacity will be expanded with the development of memory specifications. In the future, the amount of data that items need to carry will become larger and larger, and the demand for the expansion of the capacity of the label will also increase. This RFID will not Suffer
limit.
7) System security: Transferring product data from the central computer to the workpiece will provide security for the system and greatly improve the security of the system.
8) Data security: The accuracy of the data stored in the radio frequency tag is ensured by means of verification or cyclic redundancy verification.
Three, system function
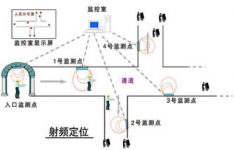
The downhole positioning system for personnel and equipment is developed by Beijing Lianxin Yongyi Technology Co., Ltd. and related organizations. It uses the most advanced RFID technology in the world. The underground personnel and equipment positioning system can timely and accurately reflect the dynamics of personnel and equipment in various areas of the underground to the ground computer system, so that managers can grasp the distribution of underground personnel and equipment and the movement trajectory of each miner at any time. Carry out more reasonable scheduling management. When an accident occurs, rescuers can also quickly understand the location of relevant personnel based on the data and graphics provided by the underground personnel and equipment positioning system, and take corresponding rescue measures in time to improve the efficiency of emergency rescue work.
The downhole personnel and equipment positioning system is a comprehensive application system integrating downhole personnel attendance, tracking and positioning, post-disaster first aid, and daily management. It is also the domestically most advanced technology, the most stable operation, and the most professionally designed underground positioning system. The realization of this scientific and technological achievement will bring new opportunities for the safety production and daily management of coal mine enterprises as well as emergency first aid. The use of RFID system for underground personnel management can effectively improve deficiencies and eliminate loopholes. The staff puts the small tag (identity card) anywhere on the body (pockets, bags are acceptable), and normally passes through the gate with RFID equipment, the system will automatically record the entry and exit information.
On the one hand, for managers, they hope to strengthen safety and security work and effectively manage personnel entry and exit to prevent safety accidents; on the other hand, for personnel entering and exiting, they hope to reduce complicated procedures and be able to Fast and smooth traffic under the premise of lawfulness. The intelligent downhole personnel management system uses computers and automatic identification technology to manage and manage personnel downhole personnel, which can effectively coordinate the contradiction between convenient and quick entry and exit methods and strict safety precautions, and reduce the risk of personnel entering and exiting the door of the building and the studio. Management difficulty.
A) Using the intelligent downhole personnel management system, it can effectively record the precise time of the cardholder’s passage, and give an alarm to those who do not have a card;
B) Through the host system of the management center, the list of all personnel in the tunnel can be monitored in real time;
C) The recorded entry and exit time information can be used for security inspections, attendance management and other applications in a period of time at the same time.
Real-time dynamic display function of underground personnel
1) How many people are there in a certain place in the well at any one time, and their identities;
2) Query the actual position of one or more personnel in the mine;
3) Record a series of information such as the arrival/departure time and total working hours of relevant personnel at any location, so as to supervise and implement whether important inspection personnel (such as gas detection personnel) conduct on-site inspections on time and on-site, or perform various items. Data detection and processing, fundamentally try to eliminate related accidents caused by human factors;
4) Multi-point sharing can be realized for multiple leaders to view at different locations at the same time.
Rich map function
It has the functions of zooming in, zooming out, moving, ruler distance measurement, field of view control, center movement, soil layer control, map printing, etc.
Restricted zone alarm function
For the designated restricted area, if a person enters, the real-time sound alarm will be displayed and the person entering the restricted area will be displayed.
Personnel track query
You can find the path that a person has gone through in a certain period of time, and draw the line trajectory in the picture.
Abundant personnel ability to go down well to check attendance
It can perform statistics on the personnel entering and exiting the well, realizing the attendance record of the personnel entering and exiting the well, and establishing various information reports of the personnel entering and exiting the well (such as: logging time report, attendance monthly report, overtime report, absence report, etc.).
Post-disaster first aid information Once various accidents occur, the upper computer can immediately display the number of personnel, personnel information, personnel location and other information at the accident site, which greatly improves the rescue efficiency and rescue effect.
4. System composition and working principle
1. System composition
Underground personnel and equipment positioning system equipment mainly includes: central station host, data communication box, B multi-function substation, wireless identification sensors for coal mines, and wireless identification cards for coal mines.

Schematic diagram of personnel positioning system
2. Working principle
First of all, place a certain number of wireless identification sensors in the areas and tunnels where people need to be tracked downhole according to the specific needs of the site. Normally, only one location needs to be placed to track the people entering and leaving the location. The wireless identification sensor is connected to the ground computer through the transmission bus, and the multi-function substation is connected with the wireless identification sensor to provide working power. In this way, a system is set up in which the underground computer is connected to the underground wireless identification sensor through a cable.
Then wear a wireless identification card for the downhole personnel who need to perform personnel tracking and positioning. When the downhole personnel enter the well, as long as they pass or approach any wireless identification sensor placed in the tunnel, the wireless identification sensor will immediately sense the signal and upload it. To the central station host computer, the software of the central station host computer can determine the specific information (such as: identity, location, specific time), and display it in the control at the same time
Heart’s large screen or computer display, and make a backup.
Managers can view a certain area according to the distribution diagram on the large screen or on the computer, and the computer will then count and display the personnel in this area. The central station host computer will sort out various attendance reports of each underground worker in this period according to the personnel access information for a period of time. In addition, once an accident occurs underground, the personnel at the accident site can be found immediately based on the personnel distribution information in the computer, and then special detectors can be used to further determine the location of the personnel at the accident site to help rescuers rescue them in an accurate and rapid manner Trapped personnel. The management principles of mine carts and other equipment are roughly the same.
3. System design principles
(1) Realize the effective identification of the entry and exit of the working surface of the underground tunnel, so that the system management fully reflects the “humanization, information and high automation”;
(2) Provide senior management personnel with various information inquiries on attendance, personnel entry and exit restrictions, etc.;
(3) Once a safety accident occurs, the system can immediately know the exact number of workers on the tunnel working surface, ensuring the efficient operation of emergency rescue and safety rescue work;
(4) After a safety accident occurs, the mobile identification device can detect whether there is anyone within the scope of the accident site, which is convenient for the timely deployment of rescue work;
(5) The safety, scalability, easy maintenance and easy operation of the system design.
4. System design basis
(1) GA/T75 “Procedures and Requirements for Safety Protection Engineering”
(2) MT209-1990 “General Technical Requirements for Electrical and Electronic Products for Communication, Testing and Control in Coal Mines”
5. System design features
High degree of automation: The system can automatically detect the time and location information of the underground tunnel workers passing the monitoring point, and automatically realize the statistics and management of attendance operations;
Advanced communication system: the identification system installed in each channel of the underground mine can transmit the data passed by relevant personnel to the network server in real time, without human intervention in the whole process;
Complete data statistics and information query software: LH scheduling algorithm is used to optimize the data processing capacity of the system. The system software has a dedicated database management system, including the information collection and statistical analysis system for workers passing through the tunnel, and the statistics and management analysis system for attendance operations. Print all kinds of statistical report data to provide a full range of services for the inquiry and management of senior management personnel;
Systematic safety, stability, and reliability design: The system products adopt the tunnel wall-mounted design, no on-site construction in the tunnel is required, and the system can continue to operate normally for 24 hours in harsh environments;
Complete alarm call system configuration for abnormal conditions (including invalid identification card and entry of invalid identification card);
Convenience: When personnel go down the well, swipe their card, and the system will automatically alarm for non-card holders. Through the setting of the management system, the management center can monitor the personnel entering and exiting in real time;
Reliability: radio frequency induction, stable and reliable, with its own judgment ability;
Flexibility: It can run on the Internet, and can register or cancel the card at any time;
Versatility: One card can be used for underground personnel management, as well as patrol, attendance, consumption and other management integrated on the card to achieve a “one card” to improve management efficiency and level;
Compatibility: The system can be connected to devices from different manufacturers, has the ability to connect devices with different protocols and interfaces, and can be adapted to the various communication interfaces and communication procedures provided by users;
Openness: The system database interface adopts an open structure to suit user requirements. At the same time, it provides a secondary development interface of the database, so that users have the ability to expand the system independently;
Advanced system platform: using Windows network operating system and high real-time dynamic database technology, with high real-time data processing capabilities; geographic information display and query system based on GIS technology;
6. Equipment advantages
High recognition reliability, 100% front-end recognition rate;
Long recognition distance (recognition distance can reach more than 10-30 meters);
High anti-collision performance (each detection point can identify up to 200 people at the same time);
High recognition stability (bit error rate is less than 1/100,000);
Fast recognition speed (up to 200 km/h recognition speed).
The communication distance is long, up to 20 kilometers.
It is widely used, easy to install and easy to operate.
7. On-site advantages
Environmental adaptability: high anti-interference, no special requirements for underground interference sources and perimeter environment;
Installation convenience: sensor integrated structure design, no need for external antenna or ground sense;
Operational reliability: The internal circuit is highly integrated, and the device failure rate is minimized.
8. Electrical characteristics
Ultra-low power consumption, the wireless tag can work continuously for 5 years without changing the battery;
Convenience and safety, the label does not require an external miner’s lamp power supply, does not need to be charged, and does not need to replace the battery;
No radiation, no impact on human body and environment, safer and healthier.
Five, system design plan
This system follows the principle of “uniform wireless identification card, unified equipment, unified management”, and implements the system of “one person, one wireless identification card” according to the permission of staff and teams. Entry permit”. The specific plan is as follows:
(1) Mining production units install a certain number of wireless identification sensors in all tunnels, and the specific location is determined according to the site conditions to meet the radiation area;
(2) Mining production units issue and equip relevant personnel with wireless identification cards, which are installed in safety helmets or other suitable positions;
(3) When issuing a wireless identification card, log in the basic information of the employee corresponding to the wireless identification card, including name, age, gender, team, type of work, position, and personal photo in the system database;
(4) The wireless identification card will become effective after the safety production department authorizes the wireless identification card. The scope of authorization includes: the employee can be qualified to enter the tunnel of the work surface, the aging, invalidation, and loss of the sensor, etc.,
To prevent irrelevant and illegal persons from entering the tunnel;
(5) Personnel entering the tunnel must wear a safety helmet equipped with a wireless identification card. When the person passes the identification monitoring point of the tunnel, he is immediately recognized by the system, and through the information exchange of the system network, the information such as the road section and time passed by the person is transmitted to the well safety monitoring center for record, and can be recorded on the large geographic information screen at the same time A prompt message appears on the wall, showing the name of the passing person. If the detected wireless identification card number is invalid or enters a restricted channel, the system will automatically alarm, and the security monitoring center staff on duty receives the alarm signal and immediately executes the relevant safety work management procedures.
(6) Once a safety accident occurs in the tunnel, the safety monitoring center can know the basic situation of the trapped person in the first time. The rescue team uses a mobile long-distance identification device to easily detect the location of the person in distress within a range of 10 meters. Safe and efficient operation of ambulance work.
Six, system hardware
1. Wireless Identification Sensor
The wireless identification sensor for coal mine is a kind of radio frequency identification equipment, which is specially used to identify the wireless identification card worn by personnel, and is installed in the roadway where the personnel need to be detected. This type of sensor uses advanced RFID technology and integrates today’s most advanced 0.18uM microwave chip technology. Compared with the original microwave technology, the performance of RFID has been substantially improved. It completely solves the problem of long-distance, large-flow, The identification and data transmission of ultra-low power consumption and high-speed moving markers are difficult, and the cost is greatly reduced compared with the past. At the same time, it also solves the fatal weakness of low-frequency electromagnetic wave technology with short sensing distance and poor anti-collision capabilities. At the same time, the SUPER-RFID technology integrates:
1. Encrypted calculation and authentication to ensure data security and prevent link eavesdropping and data cracking;
2. Using channel isolation technology, multiple devices do not interfere with each other;
3. Advanced anti-collision technology supports multi-tag reading and writing.
The biggest feature of the wireless identification sensor for coal mines is that it can identify many wireless identification cards quickly and reliably in a large range at the same time, and has the advantages of micro power, high recognition rate, high anti-interference, stability and reliability. Moreover, the structure design is reasonable, the volume is small, and it is very easy to install and maintain.
Main Specifications:
1) Recognition distance: 10-30m adjustable;
2) Recognition speed: within 200 km/h;
3) Anti-collision: It can identify less than 200 wireless tag cards at the same time;
4) Working frequency: 2.4GHz-2.5GHz ISM microwave band, 125 channels, channel bandwidth 8MHz;
5) RF power: -20dBm-0dBm adjustable, the maximum peak power is 1 milliwatt;
6) Receiving sensitivity: -90dBm;
7) Working environment temperature: -40℃-60℃;
8) Power supply: 18V DC;
9) Maximum working current: <100mA.
(Picture of wireless identification sensor)
2. Wireless identification cards for coal mines
The wireless identification card for coal mines is an electronic tag specially used for identification by the wireless identification sensor, which is worn by the miners when they go down the mine.
It is an active radio frequency identification card with an intrinsically safe circuit design. J Wireless identification cards for coal mines also use RFID technology. The biggest feature of this product is that multiple tags can be identified simultaneously in a larger range, and it has the advantages of wireless micro power, stability and reliability, and is small in size and easy to carry or place.
main indicators:
1) Standard size: 60×35×6mm;
2) Recognition distance: 30-50m adjustable;
3) Working frequency: 2.4GHz-2.5GHz ISM microwave band, 125 channels, channel bandwidth 8MHz;
4) RF power: less than -3dBm;
5) Receiving sensitivity: -90dBm;
6) Working environment temperature: -40℃-60℃;
7) Working current: less than 5uA;
8) The ID number is unique in the world;
9) The battery has a one-time service life of more than 5 years.
(Picture of wireless identification card for coal mine)
3. Hardware installation steps and precautions
1) Installation steps
A. According to the underground location map, roughly estimate the direction and length of the wiring, and determine the placement points of the substations and wireless sensors;
B. Laying underground power lines and communication data lines;
C. Set the power substation: adjust the substation on the ground according to the underground grid voltage (660V or 380V), that is, replace the fuse tube in the fuse box, 0.2A for 660V, 0.5A for 380V (factory default 660V);
D. Before going down the well, weld the large and small aviation joints, and take them down the well together with the welded wiring. (The power aviation connector is used for the connection between the wireless sensor and the substation, and the communication aviation connector is used for the connection between the sensor and the communication line);
E. After confirming that the internal fuse of the substation is consistent with the voltage of the underground power grid, transport the substation to the corresponding location underground, and complete the connection between the wireless sensor and the substation and the connection between the substation and the original (380V or 660V) line underground. ;
F. Place the underground wireless sensor;
G. Power-on detection circuit;
H. After confirming that the line connection is intact, enter the personnel and card number data on the PC;
I. Distribute cards and prepare to run downhole personnel positioning system software.
2) Matters needing attention
A. The substation is best placed in a place where 380V or 660V lines pass through underground;
B. The remaining wire length is about 2 meters at the agreed position where the wireless sensor is placed;
C. Wrap the shielding layer of the data line when welding the communication aviation connector;
D. Bring the substation switch joystick before going down the well;
E. The height of the sensor should be moderate (1.5~2 meters), and the front side should be aimed at the other wall of the roadway;
F. In order to ensure the accuracy of card reading, the card is best fixed on the employee’s mine cap;
G. After the pipeline is laid, use a 500V megohmmeter to measure its insulation resistance to ground, which should not be less than 20 megohms;
H. System grounding: The working grounding from the center room to the grounding body should be inserted into a fixed protective sleeve, and the working grounding and protective grounding must be separated.
Seven, system software interface

1) System main menu:
2) Set the read head inspection configuration table

Set the read head inspection configuration table. After clicking, the sub-station inspection table will pop up, select (√) the number of readers installed in the underground, and after all are selected, press save. Double-click the blank area of the sub-station inspection configuration table, and exit without saving. The scheduler only sends commands and reads data to these read heads. A dot represents a reading head. When the read head is operating normally, the color is green, and the communication interruption is red. Move the mouse to a certain dot, and the relevant installation information of the reader will be displayed.
3) Query the current number of underground personnel and regional distribution. The representative reader on the map. After the system is installed, there is no when it runs for the first time. Through the initialization of this subroutine, a reading head icon is generated on the map.

A. Initialization
At the beginning of the system operation, delete some table records and the positioning of the reading head icon. It should be implemented according to the actual situation.
B. Clear the real-time data table
Clear the records in the real-time data table, and at the same time clear the personnel icon on the personnel layer.
C. Generate the reading head icon from the reading head management table
To generate a reading head icon, complete the following 2 steps:
(1) Click this sub-menu, the system will generate a reading head icon based on the record in the reading head management table, and
Temporarily place all the icons in the middle of the map.
(2) Use the reading head moving tool to move the reading head icon to the installation position. Click to move the reading head, move the cross arrow cursor to the reading head icon, and press the left mouse button to move the reading head to the appropriate position. Move the reading head icon to the installation position step by step.

D. People in the circular area
Click the person in the circular area with the mouse, then move the mouse to a certain point on the map, press the left button, pull the mouse, leave this point, draw a dotted circle, release the left button to find out the people in the circular area , The personnel icon flashes in red, the personnel refresh button is for prohibiting refresh, and the relevant data is displayed in the grid list at the bottom left, as follows. Click the right mouse button in the table area, and the option to print this table will pop up. In the table area, click the reading head number with the left mouse button, and an arrow will be used to indicate where the reading head is. Press to clear the grid list.To restore the automatic refresh of the personnel layer, please click the button to change to the automatic refresh state of the personnel layer

E. People in the rectangular area
The method is to find the people in the circular area, but the people in the dotted rectangle.
F. Personnel image information
Click the image information of a person with the mouse, then move the mouse to a person on the map, and press the left button to display a piece of related data about that person in the grid list. At the same time, the person’s tag number, name and department are displayed on the upper right of the map. Double-clicking this display area will clear the display.
4) Statistical attendance function, the activity trace of any designated downhole personnel on the same day or on a specified date can specifically display the precise downhole time and uphole time of each downhole personnel. And according to the type of work (specified full shift time), judge whether different types of personnel are in full shift, so as to determine whether the trip is effective. In the monthly statistics report, the downhole time and the number of downholes (effective times) are classified and counted, which is convenient for assessment. It can also print monthly attendance reports, statistics on underground trips in any time period, and other related reports.
8. System workflow
1) The PC monitoring software sends the command to configure the communication box (the configuration content is mainly the serial port baud rate (9600), etc. and the address of the wireless sensor to be inspected (set by the built-in toggle switch at the factory, remember that the same mine number cannot Repeat) until the configuration is successful!
2) The data communication box sends addresses and control commands to the underground. If the wireless sensor address matches the address contained in the inspection command, it will send data and status signals to the communication box one by one.
3) The data communication box converts the data and status signals sent by the downhole sensors into RS-232 standard signals, and performs serial communication with the ground host.
4) The PC underground personnel monitoring software updates the content of the electronic map according to the received data in time, and saves the data for statistical information at any time.
[ad_2]


