RFID item positioning management system solution
[ad_1]
1. System Overview
Dingchuang Hengda RFID item positioning management system is an item management system that uses RFID technology and specifically solves the constant research and development brought about by item positioning in the past. Mainly realize the functions of real-time monitoring of items, item management, authority management, area management, item movement track playback, alarm record query, access record query, etc., changing the traditional manual method of classifying equipment information management, recording and query management It provides comprehensive, reliable and efficient dynamic data and decision-making basis for the management of items, realizes the informatization, standardization and standardization of item management, and comprehensively improves the work efficiency and management level of item management. This system automatically While counting the number of vehicles carried, it can also perform operations such as attendance on the driver, which is more convenient and scientific management, and the system also provides a third-party interface for customers to seamlessly connect with other software.
2. System composition

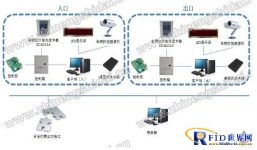
System composition diagram (Figure 2-1)
The hardware of this system includes: activeelectronic label, 2.4G active reader (DC-0302A), 2.4G locator (DC0310A), item positioning management system host, server, image capture camera, etc.
3. Software function

PC-side software interface diagram of item positioning management system (3-1)

PC-side software function diagram of item positioning management system (3-2)
The PC-side software of the item positioning management system includes: real-time monitoring, object management, system settings, query statistics, and area management.
3.1 Real-time monitoring
After real-time monitoring is turned on, the system will monitor the area covered by all readers. If an item with an RFID active tag appears in the reader’s read-write range, the system will record the information of the item bound to the tag And its trigger event, if this item is an unauthorized entry or exit, an alarm will be processed;
Monitor the status of items
Deployment map management
3.2 Object management
Functions for related management of users and items;
User Management
Item management
Inbound management: Bind a positioning card to the item. When entering the warehouse, you can enter the item number, positioning card number, item type, item description and other related information. After the information is reported to the host by the base station, it will be displayed in the item information column of item management;
Item inventory: item inventory can automatically count various types of items and quantities without manual operation;
Outgoing statistics: Outgoing statistics include item number, item type, storage time, outgoing time, destination and other information. It can be inquired according to the item number, item type, whereabouts and time;
3.3 Query Statistics
Provides a variety of query methods, which can be used to query items according to their area, shelf number, item type, item number, location card number, maintenance status, and storage time;
Track playback: You can query information about the place and time of entry and exit of the specified item within the specified time
Alarm record query
Access record query
3.4 Area Management
Set up the management function of the authority of the area where the item is located;
Item authorization
Regional authorization
3.5 System Settings
System settings and management of system user information and permissions.
Permission settings
parameter settings
Operator management
change Password
4. System Features
The system uses RFID technology to achieve long-distance control, better, safer and more accurate supervision of items.
Good anti-interference can greatly reduce the misreading rate.
While monitoring the items in real time, you can also authorize the items to be prohibited from entering and exiting places. If the item appears in the restricted area, the alarm will be reported to improve safety.
The user can query whether the item is lent or alarmed according to the specified conditions, so that the user has a more intuitive visual state, which is more convenient and faster than the previous file management;
The system provides a variety of flexible third-party interfaces to seamlessly connect with third-party application systems.
[ad_2]






