Visitor management system
[ad_1]
Overview
This system is based on the technical requirements of functional design, structure, performance, installation and testing proposed by the corporate agency for personnel access management and public security systems, combined with the current advanced visitor management concepts and network technology, and integrates various intelligences on the industrial PC Intelligent management system for equipment development.
The system can realize: document scanning input, direct reading of information including the second-generation card’s built-in chip, automatic generation of visitor slips, visitor photos, printing receipts, scanning verification, multi-door access and other functions; the system also needs to realize internal personnel entry and exit credit card authentication And tips.
Design Principles
Stability principle: According to the environment in which the visitor system is used, this design does not use any products that have not been certified by the market, and the product selection uses a visitor product with good performance that has been on the market for more than 2 years.
Practical principle: start with professional and practical, eliminate additional costs such as fancy and impractical functions, to ensure that the application personnel can quickly get started, and the maintenance personnel can manage the equipment and judge faults easily.
System scalability: After 18 years of market testing, the Chaolun intelligent enterprise management platform has been continuously summarized and improved for the practical application of enterprise management. It has a modular design and flexible architecture. From the beginning of the design, customers may add functional equipment in the future. The company will expand and upgrade smoothly in the future, effectively ensuring that the company will not repeat investment.
system design
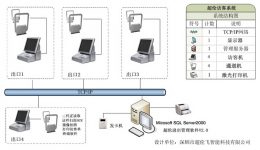
System structure design, Client/Server structure, C/S for short, is a network computing mode that distributes processing tasks between the client and server of a computer network. The client requests information and services from the server, and the server responds to the client’s request, so that each door enters and exits the network, and information is shared without any omissions.
System topology

The central platform system is the core layer of the visitor system: it is composed of various modules such as the all-in-one card central database, identity management, system management, etc., and realizes the functions of internal personnel card issuance management, visitor data center management and other functions, and manages business flow and data flow. The hardware configuration is database server, report printer, card issuing machine, visitor management software, etc.
Application subsystem: It is the application service layer of each door terminal, which directly serves users and provides management of various application functions of the visitor system, including card management, comprehensive inquiry, collection of visitor information, communication with interviewees for confirmation, and internal card swiping prompts Etc.; hardware configuration industrial-grade visitor all-in-one machine, card reader, speaker, etc., optional telephone, etc.
The functions are as follows
Using the latest technology, the second-generation ID card is read and recognized, and the relevant information of the ID card is obtained through the card reading, which is fast and accurate.
The special scanner for ID can scan various IDs such as ID cards and driving licenses, and can do OCR recognition on ID cards without the need for handwriting by visitors, effectively ensuring the correctness of the registration information.
During the registration process, take pictures through the camera and save the taken pictures.
Scan and save the pictures of general documents such as business cards and work permits, and save the information of visitors to the maximum to ensure the integrity of the information.
Users can set their own query and statistics conditions, and quickly query and count past registered data. For example, count how many people have visited during a certain period of time, and who have visited in total.
A large amount of registration data (more than 400,000 entries) is completely stored in the computer system, and the registration information will not be lost.
Users can set various query conditions according to their own needs, and quickly retrieve past registration data.
In the case of simultaneous registration of multiple visitors (multi-door entry and exit), all registration data can be shared in real time via the network, which is convenient for visitors to choose import and export at will.
Temporary personnel cards can be automatically clocked in and registered quickly, and manual storage is not required. If there is an error in reading the card, an alarm can be popped up immediately, and the next temporary personnel can be clocked in and registered after the alarm is cleared.
[ad_2]