Face recognition access control solution for campus gates
[ad_1]
Chapter One System Overview
1.1 Overview
The management of school gates is generally managed by security personnel. This method has certain safety hazards, such as chaotic management and easy entry of some foreigners due to human negligence. Although many school gates use traditional card swiping methods to enter the campus, the problem of losing student cards also poses a certain security risk to the management of the campus. In order to better strengthen the management of campus security, prevent outsiders from entering, and provide students with a safe and comfortable learning and living environment, we have introduced the following campus entrance and exit face recognition access control system solutions. After using this solution, when students enter the campus, they do not need to swipe their card to open the door. They only need to swipe their face on the face recognition device to enter and exit. This can solve the cost of the school card without worrying about the security issues after the card is lost. The safety factor of the campus is greatly improved.
1.2 Features of Biometrics Technology
Biometric recognition: such as fingerprints, iris, human face, voice, etc., mainly use automated technology to measure their physical characteristics or personal behavior characteristics, and compare these characteristics or characteristics with the template data of the database to complete a solution for authentication.
A. Fingerprint recognition: Among all the biological characteristics of the human body used for individual identification, fingerprint characteristics are the first to be discovered and applied. But every time a fingerprint is used, it will leave the user’s fingerprint imprints on the fingerprint capture head, and these fingerprint marks may be used to replicate; in addition, because some people or groups of people have very few fingerprint features, it is difficult to image , So it needs to be recognized multiple times or cannot be recognized;
B. Iris recognition: The current iris recognition has not been tested, only a small-scale test has been conducted using statistical principles, and the only certification test in the real world has not been conducted; at the same time, the requirements for the light source are very high, and the equipment required materials Expensive, low cost performance, and extremely difficult to read with dark eyes;
C. Voice recognition: Because the range of sound changes is too large, it is difficult to carry out some precise matching; the sound will affect the results of collection and comparison with changes in volume, speed and sound quality (for example, when you have a cold); at the same time Voice recognition is easy to fool the voice recognition system with the voice recorded on the tape;
D. Face recognition: It is a computer technology that uses the analysis and comparison of the visual feature information of the human face to identify the identity. It has the characteristics of naturalness, non-mandatory and non-contact. At the same time, face recognition uses the unique characteristics of the face, which is not easy to be copied, has a high recognition rate, and a fast recognition speed; in addition, the face recognition successfully passed the twin test, and the application performance can be recognized by the test;
Main features of face recognition:
1. Uniqueness: Everyone has a face, and it cannot be copied or counterfeited, so the security is higher.
2. Good naturalness: Face recognition technology is the same as the biological characteristics used by humans (or even other living beings) for individual recognition. Other biological characteristics such as fingerprints and iris do not have this characteristic.
3. Simple and convenient: no need to carry a card, fast recognition speed, simple and convenient operation.
4. Non-contact: There is no need to touch the equipment, and there is no need to worry about the contact transmission of the virus, which is both hygienic and safe.
Therefore, if the face recognition technology is widely used in the access control attendance identification system, the security and reliability of the access control system operation will be greatly improved, and the possibility of entering the office building through the impersonation of the identity will be greatly reduced. Greatly reduce the existing and potential technical loopholes, hidden dangers and risks in the access control security system. At the same time, the unique feature of the face eliminates the act of clocking in at the root and standardizes the corporate attendance management system.
1.3 System design standards and specifications
※ International integrated wiring standard ISO/IEC118012
※ “Code for Electrical Design of Civil Buildings” (JGJ/T16-92) Ministry of Construction
※”Intelligent Building Design Standard” (DBJ08-4-95) Shanghai Construction Commission 1996
※”Code for Design of Integrated Wiring Engineering for Buildings and Building Groups” China Engineering Construction Standards Association
※”Code for Construction and Acceptance of Comprehensive Wiring Engineering of Buildings and Building Groups” China Engineering Construction Standards Association
※”The People’s Republic of China Security Industry Standard” GA/T74-94
※”People’s Republic of China Public Safety Industry Standard” GA/T70-94
※ “Technical Specification for Monitoring System Engineering” GB/50198-94
※ All computer hardware systems meet the following standards:
Electromagnetic regulations: FCC Class B or CISPR22 Class B
Chapter 2 Application of Face Recognition in Campus System
2.1 Design principles
The premise of the design of the campus access control system is to meet the various needs of users. Utilize its advanced, mature, reliable, flexible technology and good price-performance ratio to maximize the long-term interests of users and allow users to obtain the greatest return with the smallest investment.
Design advancement: The system design and product selection should have a certain technological advancement when put into use, but not blindly pursue immature new technologies or impractical new functions to fully protect users’ investment
Reasonable structure: the use of advanced and mature technology to build each subsystem can make it operate in a safe and balanced manner, effectively eliminate the bottleneck that may occur between each system, and the selected equipment ensures that each subsystem has good scalability and a wide range of compatibility. Stability and safety are the key to the system. The system is based on stability, safety, and efficiency to ensure normal and reliable operation of the system.
Reliability: The design of the system should have high reliability. After a system failure or accident causes an interruption, it can ensure the accuracy, integrity and consistency of the data, and have the function of rapid recovery.
Easy to operate and maintain: The products used should be simple, easy to operate, and easy to maintain. The face recognition intelligent system is a system for various management levels. The configuration of the system and its functions is based on the principle of providing users with comfort, safety, convenience, and speed. Its operation should be simple and easy to learn, and must not be “intelligent”. It brings inconvenience and even annoyance to users.
Compatibility: All systems are relatively open systems, with standard interfaces between products, and a variety of communication standard protocols, which facilitate the access of third-party and fourth-party equipment, and facilitate the replacement, upgrade and maintenance of equipment.
Modularization: the establishment of each sub-system until the overall system strictly implements the modular structure to meet the requirements of system function expansion, replacement of operating equipment, and maintenance functions to ensure the efficient and reliable operation of the system.
Scalability: Using object-oriented and modular development technology, software and hardware modules with other functions can be expanded at any time as needed, with good scalability.
Centralized management: the front-end field equipment and sub-systems in this system are centralized in the center for unified control, and the control and settings of all remote equipment can be implemented in the center to ensure that the system is efficient, orderly, reliable, and convenient to perform its management functions .
2.2 Campus face recognition access control applications
● It is necessary to manage the entrance and exit of the campus to prevent the entry and exit of idle personnel.
● Important office places on campus, where unified network management is required.
Chapter Three Project Demand Analysis
The client requested that face recognition devices be installed at all entrances and exits of the campus to control the entry and exit of personnel, and real-time capture of the faces of personnel entering and exiting and generating entry and exit records for the relevant departments of the school to view. The gate of the school enters from the gate during normal school hours, and enters and exits through the campus card + face or pure face. All visits and exits during school hours are passed through face verification. During school hours, there are too many people to assemble and go out without passing through the gates, but the camera needs to be captured for face capture and recording.
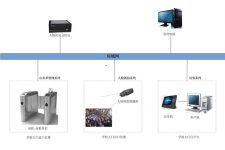
According to the actual requirements of customers, the company’s self-developed personal identification verification terminal can be installed at the entrance of the school gate (a single device can support 5000 people offline), and the portrait photos of students and teachers can be sent to the gate companion through the background software Realize face-swiping to open the door; install a smart door guard system (face capture camera + comparison analysis box) in the direction of the door exit, and compare the snapshots and record the time when students and teachers leave the campus; when strangers want to enter the campus, they need to be at the door guard The room uses the visitor’s machine to register with the combination of the person and the ID. After the registration is completed, the gate can be entered into the campus within the specified time. The gate partner itself has good resistance to light, and it can be used normally in outdoor situations. However, when the outdoor strong light shines directly on the lens, it will seriously affect the recognition speed of the camera, resulting in a low pass rate, and the gate partner itself is not completely rainproof, so In this case, an awning needs to be added to prevent direct sunlight from hitting the lens and rain.
The current demand situation of your school:
1. Install a computer server in the management center to manage all equipment and generate record queries
2. At the entrance of each gate, a personal identification verification terminal is installed for access control
3. Install a smart door guard system (face capture camera + comparison analysis box) at the exit of the gate
4. The guard room installs the person card to verify the visitor machine (visitor registration)
According to requirements, make the following hardware configurations:
1. A set of personal identification verification management system (software)
2. Personal identification verification terminal equipment (gate turns companion)
3. Face capture camera
4. Face comparison analysis box
5. A computer (self-provisioned), used to manage all devices, view student entry and exit records and manage face templates
3.2 Entry and exit management system
The entrance and exit management system is an important sub-system in the management system for identification verification. The customer sets the photos of the personnel as a whitelist through the background management software and sends them to the corresponding front-end equipment, so that authorized users can directly on the corresponding equipment Swipe face to pass, on the contrary, unauthorized users cannot pass
Safety regulations: UL Listed (U.S.) or EN60950 (International)
System composition:
This set of entrance and exit access control system is composed of face recognition device gate partner, human identification verification management software and network.
Face recognition gate partner: face recognition access control unit, this device communicates with the server through a network cable, and can directly control the gate switch.
Power supply: The power supply of the executive structure that provides the power supply for system operation.The principle of getting electricity from nearby can be adopted
Management software: Through the computer, all face templates can be network managed to realize access control management.
Network: Use the campus intranet to manage and control the management system

3.2.3 System features
◆Multi-terminal access and management
◆Multi-door and multi-terminal data sharing
◆Register face information pictures in batches, and distribute designated households to the front end of face recognition access control through the network
◆Support extended ID card, IC/ID card whitelist entry
◆Real-time verification record split-screen display
◆Whitelist management
◆Validity setting
◆Support breakpoint resumable transfer between device and software
◆Background software supports offline distribution of personnel templates
3.2.4 Application implementation
1. Equipment installation
The face recognition gate companion is installed at the entrance and exit of each gate. First, make a 48mm diameter circular control on the 400mm edge of the gate to facilitate the fixation of the equipment.After the device is fixed, connect the two signal lines (switching signal) of the face device to the control line position of the gate, and when the personnel comparison is successful, the signal output controls the gate to open the door
2. Face template collection management
Collect student photos uniformly in the campus management center. After the collection is completed, they will be uniformly entered into the whitelist in the management system and sent to each terminal. There are several precautions for photo collection:
① You can use the mobile phone rear camera, SLR camera or high-definition camera to shoot; do not use the front camera to shoot, the front camera is mostly a wide-angle lens, and the picture distortion affects the recognition.
② Do not use full-body photos, only the shoulders and above.
③ Do not use ID photos; in particular, the PS photos of most women’s ID photos are severe, which affects recognition.
④ Do not shoot near windows, entrances and exits, etc., where one side is bright and the other is dark or backlit.
⑤ The subject of the shot should have a straight head, natural expression, no obstruction, and no obvious make-up; the photos after shooting should not be PS, they can be cut, and they should be reduced in proportion to the length and width, but do not zoom in.
3. Face recognition to open the door
The student who has registered the face template scans the face in front of the face recognition gate, and the system automatically compares the registration information in the database to confirm whether the student is a valid face template that has already been registered. If it is valid and has the permission to open the door, Then the door open signal is output to control the door lock to open, and the system records the student’s door opening event.
3.2.5 Product introduction
The identification verification terminal (gate companion) is a new generation of barrier-type multifunctional dynamic face recognition ID card verification system product independently developed by Kepa Company. It integrates on-site face collection, identity verification, whitelist undocumented automatic identification, etc. Function as one. From reading ID card information to collecting face photos on site, comparing them, and obtaining results, the whole process is automated, without the need to increase peripheral hardware configuration, the operation process, and the installation is simple and convenient, and can be linked with various gates to open the door.
Features
★ High-definition display large 8-inch color screen, the entire information collection and verification are visible
★ Long-life fill light has built-in positive white light high display LED face light source, infrared human body induction triggers automatically
★ Integrated design The material and process of the equipment adopt integrated design, with its own relay signal output
★ When the device is offline, the data is saved locally when the device is offline, and the data is automatically uploaded to the background software after going online
★ The equipment with strong anti-light interference is equipped with a front 2 million high-definition wide dynamic camera, which can be accurately identified even in harsh environments
★ Easy installation The equipment is easy to install and easy to wire. Just connect the signal wire to the gate signal.
3.3 Visitor Management System
Visitor personnel safety management and internal personnel management is one of the key points of safety management in many occasions, especially campus safety. For a long time, many units still use simple manual visitor registration. This visitor management method can no longer meet the needs of information; the traditional manual visitor registration adopts manual input, so the authenticity of the information cannot be guaranteed; the quality of visitors is different, and the fonts are registered. Scribbled, so that the registration information cannot be confirmed when needed; paper storage is easy to lose, easy to damage, difficult to find, and the information is difficult to store for a long time. Therefore, it is no longer suitable for modern working methods and cannot meet the safety requirements.
Kepa visitor management system uses face recognition technology to specifically design for the management problems caused by the unpredictability of temporary visitors.The system can make the registration work more convenient and faster, the registration information is more complete, the security is higher, and the
Plus quick and effective query of visit records.
[ad_2]



