Prison criminal/suspect identification electronic label solution
[ad_1]
one.Background overview
As the tasks of public security and judicial organs to maintain social order and combat criminal crimes become more and more serious, the number of detainees, educators, compulsory drug rehabilitation and other criminals in various supervision places continues unabated. The call for information sharing is getting louder and louder, and the backward management model can no longer meet the needs of real struggles. In order to improve the level of management work, leaders at all levels have reached a broad consensus on the importance of establishing an information system for supervisory sites, and it has become an inevitable trend to plan and build an information system for supervisory sites at all levels in a unified manner.
At present, the information systems of supervision sites in various provinces are in the process of preparation or construction. In particular, the public security organs have achieved initial results in some pilot provinces according to the “General Design Plan of the Ministry of Public Security “Golden Shield Project” and the “General Construction Plan of the National Public Security Supervision Information System”. , But at present, the information systems of the public security or judicial departments are only limited to information processing, and information collection is still purely relying on hand input, and it is impossible to truly associate the information system with the detainees. This is a special kind of surveillance system. A safe and reliable information collection system is used in the environment to distinguish and identify detainees, and to truly connect the information of each person in the information system with everyone in reality, so that the information system of the supervision site can be fully utilized. In a real sense, the management informationization of prisons is realized, and the way to “require police power from science and technology” is realized.
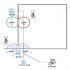
two.System Components
The system is composed of two-level network of host and data acquisition terminal system: (as shown in the figure below)
Three, the main function
1, Introduction
criminal/Criminal suspect identification wristbands are the preferred professional products of the public security and judicial systems, and are now being widely used in legal enforcement agencies in developed countries in Europe and the United States.criminal/The suspect’s identity belt has been proven to be a very convenient and reliable tool in the long-term use process. It can accurately and effectively identify and classify prisoners, eliminate human errors and unnecessary confusion, and greatly reduce guards. The burden of work has improved work efficiency.
2,use
a.Identify
Recognition is the basic function of the prisoner’s identity belt. Cooperating with information management software is extremely important for places with a large number of management objects and greater mobility.
Different from traditional prisoner registration cards or registration cards, professional prisoner identification belts are worn by prisoners personally, and photos and other related materials can be attached to the built-in chip of the identification belt. Therefore, it is very convenient to check and verify the information of prisoners at any place and in any processing process in the prison, and can correspond to more detailed information in the information management software to ensure that each prisoner is accurately identified and processed.
criminal/The identity belt of the criminal suspect is made of high-strength materials, which is very strong and durable. At the same time, a special design is adopted to prevent prisoners from exchanging or damaging the identity belt. Deliberate damaging of the identity belt will be immediately detected and stopped and punished. When the identity belt is tied to the prisoner’s wrist and locked with a metal or hard plastic lock, it cannot be removed unless it is completely destroyed, and it is impossible to transfer it to others.
b.Classification
Classification is a supplement to the recognition function.criminal/The suspect’s identity belt provides a variety of color options, and different types of criminals can be classified by different colors of identity belts.
a) Distinguish according to the nature of the crime, for example, use different colors to distinguish death row prisoners, felon prisoners, and other prisoners.
b) The criminal suspects are classified according to their status during the entire litigation process, such as the distinction between criminal detention, arrest, and sentenced prisoners.
c) According to the characteristics of prisoners, such as high-risk prisoners and other prisoners, or prisoners with infectious diseases and ordinary prisoners.
After using different colored identity tapes for prisoners, you can quickly distinguish various types of criminals or criminal suspects based on this, and improve the efficiency of management. It can visualize the distinction between criminals and criminal suspects in the corresponding information management software.
c.Strengthen management
Strengthening management is the ultimate goal of using identity bands, because identification and classification are all for improving the efficiency of prisoner management and achieving better management results.
On the following occasions:
When prisoners go out or work collectively, when prisoners meet with lawyers or family members, when the investigating unit interrogates the prisoner or even takes the prisoner out of the prison for investigation, and when the prisoner is in court for interrogation, the identity belt can be used to accurately identify the identity of the prisoner. To prevent mistakes, the identity belt can also effectively prevent prisoners from being exchanged in places outside the prison’s control.
Equipped with a handheld device, the guards can retrieve the prisoner’s detailed information based on the chip attached to the identity belt without having to look through the files. The handheld device can also automatically register and transfer the time of a certain prisoner’s exit and entry to the computer. Keep it forever.
3, Advanced features
⑴、Data can be stored in the chip, and data can also be repeatedly written and modified;
⑵、No light is needed when operating the chip, and data can even be read through external packaging materials;
⑶,The electronic chip has a long service life and can work in harsh environments;
⑷、The reading range is farther, on the chip5
⑸、It can realize real-time tracking and positioning, and automatic monitoring;
⑹、The data stored in the chip is protected by encryption, which is more secure;
⑺、The identity belt can be worn very conveniently on the prisoner’s wrist while ensuring maximum safety;
⑻、Provide the most9Different colors are convenient to classify prisoners;
⑼、The special design makes the identity belt difficult to be damaged, even if it is damaged, it can be detected quickly, ensuring the uniqueness and correctness of the identification object.
Fourth, the system software module
[ad_2]